- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Cisco Switches - Turn Off Default Behavior / Asymmetric Switching / Disable MAC Learning ?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Switches - Turn Off Default Behavior / Asymmetric Switching / Disable MAC Learning ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2019 10:26 AM
Hello CISCO Community. I have an idea but I am not sure if I am just limited in the IOS to make this work or if there are any other technologies / configurations to make it happen.
Basically, I am connecting two switches together with 2 links and I want the traffic to go firth on one link but come back on the other. STP will be blocking one of the ports so this option of course will be turned off for this to work.
I have seen somewhere that there is such thing as "no mac-address-table learning" for an MWR Router (https://www.cisco.com/c/en/us/td/docs/wireless/mwr_2941_dc/software_config/guide/3_4/2941_34_Config_Guide/mac_lrn.html) but I could not find if this can also be done on Catalyst Switches or Switch Modules.
Has anyone ever tried this and is this at all possible ? You may ask why am I doing this ? Each of the LINKS between the switches are using a certain technology that carries traffic only one way (Satellite Communication). One of the links is going to serve as a pure TX port (planning to make static MAC tables for the remote destination devices) and the other one will be used only for RX traffic.
Please let me know if there is an
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-14-2019 11:11 AM
Hi,
Terminating the STP will cause a Layer 2 loop in your network and will down soon and the mentioned command will not work on the switch also.
But really, This is the first time, I am facing this issue. Can you answer some of the questions as?
1. At the remote site, are TX and RX ports have the same mac address?
Really, I am not sure but I hope a HUB will resolve your issue but a letter on how the switch will decide that where will forward traffic based on the ARP because of the same IP address on RX and TX at the remote end.
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 05:04 AM
Hi Deepak, thanks for the reply. Yes, the host at the remote end behind the switch should have the same MAC.
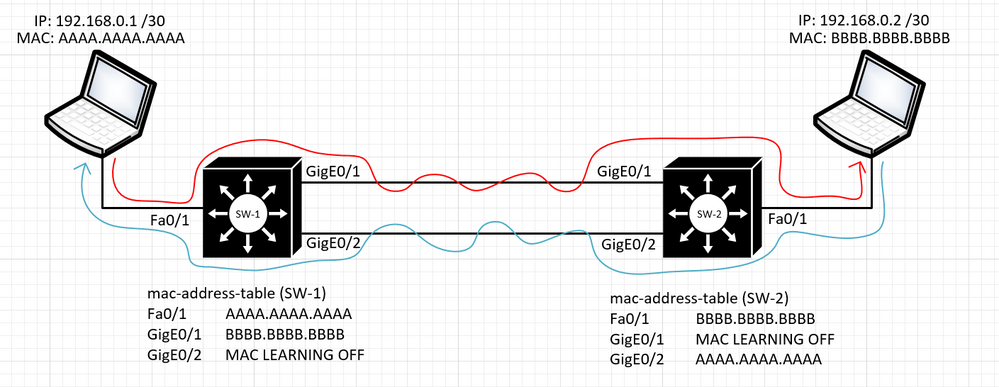
The idea would be to have all frames leaving the Head Office go out of one port (the uplink) on the SW towards the destination. Once there the switch should make a decision and send the frame out the port where the HOST is ... the HOST will then reply and the frames on the way back should be funneled out a different port (mostly using static mac address table entries I guess) to reach the Head Office. I have tried playing around a little bit with port-security and disabling STP but that does not really help much because broadcast frames still flood the loop.
I have also found that static mac-address-table configuration get's rewritten on the SW if the HOST mac address makes it around the loop and back to the source SW, in which case the MAC ADDRESS table becomes incorrect.
Here is what I am looking forward to achieve.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 05:42 AM
Hi,
I don't know why are you trying the same? Both hosts are in the same subnet so it is very difficult (I can say not possible). This is possible using the Layer 3 interface but you can't keep the same VLAN subnet on both switches (Don't think about VXLAN etc).
I have another solution for you as go with port-channel/Teaming/Etherchannel configuration between both switches. Here your both ports will work as a single logical port and you will get 4Gbps speed (count in full-duplex).
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 05:46 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 05:42 AM - edited 10-15-2019 05:44 AM
I'm curious why you want to do this.
each UTP port all ready as a separate transmit and a receive link?
and as you describe it the streams by itself are unidirectional, So why split it between two physical ports?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 06:26 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 06:46 AM
Hello,
First of all I need to mention, that even if such topology will work somehow, it will be extremely ""not-recommended" design.
Is it possible to put those hosts to different VLANs and use routing? In this case it would be easy to achieve asymmetric flow.
Regarding your requirements. In additional to what you have tried, I suggest to try to use ingress MAC ACL, which will block AAL the L2 traffic on those interfaces, where you don't expect input, to prevent the looping, meaning on Gi0/1 SW-1, and Gi0/2 SW-2.
You still will need to disable STP, have static MAC entries, and disable MAC learning on those ingress interfaces (not sure if MAC ACL will prevent switch from learning MACs). But MAC ACL should prevent traffic from looping and overwrite static enrtries.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 06:55 AM - edited 10-15-2019 07:02 AM
Thank you VB10, yes I was thinking about splitting the flows in VLANS but I am working on finding an as transparent as possible layer 2 system solution over satellite links - I am sure there will be quite a lot of limitations but this is just the first step.
I will definitely look into the MAC ACL, I have tried something similar with port-security but even like this, broadcast storms are inevitable since there are other frames that by default are flooded around ... ideally I would need any frame with unknown destination to be dropped at the switch to avoid consuming precious satellite BW :)
I was also trying to look for information on how to disable MAC ADDRESS LEARNING on CISCO SW but the Catalysts that I have do not have the "mac-address-table learning" configuration options.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2019 07:21 AM
Yes, mainly broadcast traffic needs to be blocked by Port MAC ACL, to prevent flooding and MAC overwriting. But it's better to block all the ingress traffic, since we don't expect any incoming packets on those interfaces.
MAC ACL should also support simple "deny any any" statement.
Production satellite traffic should be sent according to static entries via different interfaces.
But MAC ACL on Port can be applied only to ingress direction, meaning that traffic from remote switch still will be sent over the link and consume some bandwidth. In order to prevent such scenario, you can also consider to use "vlan-filter" feature with MAC ACL on remote switch (source). But then ACL will be more conplex, it needs to exclude legitimate "production" traffic, and it depends on number of hosts and whether anything else is connected to those swithes.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide