- Cisco Community
- Technology and Support
- Networking
- Switching
- Re: Help before buying Cisco SG350 series switch
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-17-2019 09:46 AM - edited 08-20-2019 01:18 AM
Hi,
I am looking at a Cisco managed switch to do the following:
- have 3 or 4 VLANs: private, office, guest and optionally shared (that could go in private and be shared via ACL rules)
- Each VLAN in a different subnet
- private VLAN: PC to manage all VLANs and connected devices, NAS-1, router, WLAN-AP, shared clients (NAS-2, printer...), have internet access
- office VLAN: have access to internet and some shared clients (NAS-2, printer...)
- guest VLAN: internet access only
- shared : NAS-2, printer, have internet access
The switch will be cable wired mainly to:
- a home/SOHO router non VLAN aware where the DHCP server will be disabled. It will have the DNS service configured on it
- a UniFi AP AC LR that is VLAN aware and that will broadcast 3 SSIDs: private, office and guest for each VLAN
- the management PC
The Switch should be able to:
- work as a DHCP server for all the VLANs
- do inter-VLAN routing
- have ACL rules if I want to put the shared resources in the private VLAN and allow access via ACL
Exp:
Cable Modem
|
Home/SOHO Router WAN port
+
Home/SOHO Router LAN 1
192.168.1.01
|
Managed Switch + DHCP server
+ Port 1: default VLAN 1 connected to home router: 192.168.1.10
+ Port 2: VLAN 10 (private / management): 10.0.10.0/24
+ Ports 3-4: VLAN 20 (office): 10.0.20.0/24
+ Ports 5-7: VLAN 30 (shared): 10.0.30.0/24
+ Port 8: VLAN 40 (guest): 10.0.40.0/24
Will the SG350 series fulfil my needs or should I look at another model ?
If yes, I read the manual and I am really uncertain if the DHCP server will serve all the VLANs via dedicated pools:
- what would be the "Default Router IP Address" and the "Domain Name Server IP Address" for each DHCP pool ?
- for my use, do I need to configure the NetBIOS, SNTP and TFTP entries as I am not sure about their purpose in the DHCP setup
Many thanks for your help
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2019 11:39 PM - edited 08-18-2019 11:47 PM
Hello Filomena,
your understanding is correct. Let us give a look to some details:
the port connecting to the non Vlan aware router must be an access port in specific Vlan 1.
As you have noted the router needs to configure static routes for all the Vlan associated IP subnets pointing to next-hop Switch vlan 1 IP address 192.168.1.1 ( in your first post you say 192.168.1.1 is the IP address of interface vlan1 on the switch)
What is really important to add is that the router must perform NAT = Network Address Translation for all the subnets connected to the new switch.
More specifically you need to modify an ACL or a list that defines what source addresses should be translated to the "WAN" interface IP address when routing to the internet.
Without NAT internet access is not possible from private IP addresses like the 192.168.x.0/24 or 10.x.y.0/24 are (RFC 1918 private IPv4 addresses).
So you need to verify if the router allows to extend NAT configuration for subnets that are not directly connected to it.
In some cases there is this limitation, and if this limitation is present the router is not good to do its job.
The router will route packets to the switch for destinations that are in the Vlan 10,20,30,40 IP subnets using untagged frames and sending to the MAC address of the SVI interface vlan1 on the switch.
The switch will perform packet rewrite changing the L2 header:
changing the source MAC address to that of SVI Vlan X
changing the destination MAC address to that of the end device in Vlan X.
At the IP level the TTL is decremented by one and the IPv4 header checksum is recalculated (actually increased by one).
And yes the switch wil perform inter vlan routing.
Again, the switch should be able to do all its tasks (it cannot do NAT) and you need to verify that NAT configuration on the router can be extended to cover also the IP subnets of Vlans 10-40.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 11:49 PM
Hello Filomena,
you need to make a tradeoff / compromise between what you can do.
Using an RV340 router for me means moving inter vlan routing from the SG350 (a multilayer switch working in hardware) to a SW based router.
Yes, the RV340 may have a GE interface to connect to the internet but:
a) as many SW based routers it may be not able to support a GE at full speed
b) if used for intervlan routing it becomes a bottle-neck as the inter vlan traffic is limited to the one GE trunk between the router and the switch. (traffic counts twice a 50 Mbps flow between Vlan 10 and Vlan 20 will use 50 Mbps in both directions on the link between router and switch)
If instead you use the SG350 as multilayer switch the inter vlan routing is not limited to 1 GE in total but it is limited by the switching fabric bandwidth that should be at least of 10-20 Gbps.
I see a big difference here.
I don't think the RV340 can perform NAT for not directly connected subnets as you can see in the GUI there is a NAT enable flag for connected interfaces. I remember a thread where we tried with another user to enable NAT for static routes with no success.
You know your network scenario and your needs.
In my opinion is better to have far better local inter vlan routing performance on the SG350 and have a router able to perform NAT for not directly connected subnets even if this means a slower internet connection.
If your end users are using any SaaS (software as a service ) like MS Office365 Google equivalent or you have cloud connection then you need a very fast and symmetric internet pipe.
If most of the traffic is local between Vlans the solution with the SG350 performing inter-vlan routing is to be preferred.
Of course, if you change the network design the port 1 of the switch must become a trunk carrying all Vlans but that port becomes the bottle neck of performance in inter vlan routing.
Your understanding of FW rules on RV340 is correct, but I would not go with this router for the afore mentioned limitations on NAT.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2019 01:37 PM - edited 08-18-2019 01:49 PM
After more readings in the manual and forum:
- the switch should do inter-VLAN routing (IPv4 based)
- DHCP server should work for all 3 VLAN if I setup a DHCP pool for each of the VLANs IPv4 ranges
- the DHCP "default router" is the "default-router" cli command, and should point to the corresponding VLAN IP
Now, my question remains, if all above is true, to give internet access to all my VLANs through port 1:
- I trunk port 1 connected to the home router (non VLAN aware)
- on router: I create static routes for the VLANs 10, 20, 30 and 40 redirecting to the VLAN1 address 192.168.1.1
In my understanding, router will untag all egress traffic anyway.
On ingress, the switch should do the intervlan routing based on the IPv4 address of the concerned client.
Please if someone can kindly confirm my setup or if I have no choice than using a VLAN aware router (which I want to avoid to limit costs)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-18-2019 11:39 PM - edited 08-18-2019 11:47 PM
Hello Filomena,
your understanding is correct. Let us give a look to some details:
the port connecting to the non Vlan aware router must be an access port in specific Vlan 1.
As you have noted the router needs to configure static routes for all the Vlan associated IP subnets pointing to next-hop Switch vlan 1 IP address 192.168.1.1 ( in your first post you say 192.168.1.1 is the IP address of interface vlan1 on the switch)
What is really important to add is that the router must perform NAT = Network Address Translation for all the subnets connected to the new switch.
More specifically you need to modify an ACL or a list that defines what source addresses should be translated to the "WAN" interface IP address when routing to the internet.
Without NAT internet access is not possible from private IP addresses like the 192.168.x.0/24 or 10.x.y.0/24 are (RFC 1918 private IPv4 addresses).
So you need to verify if the router allows to extend NAT configuration for subnets that are not directly connected to it.
In some cases there is this limitation, and if this limitation is present the router is not good to do its job.
The router will route packets to the switch for destinations that are in the Vlan 10,20,30,40 IP subnets using untagged frames and sending to the MAC address of the SVI interface vlan1 on the switch.
The switch will perform packet rewrite changing the L2 header:
changing the source MAC address to that of SVI Vlan X
changing the destination MAC address to that of the end device in Vlan X.
At the IP level the TTL is decremented by one and the IPv4 header checksum is recalculated (actually increased by one).
And yes the switch wil perform inter vlan routing.
Again, the switch should be able to do all its tasks (it cannot do NAT) and you need to verify that NAT configuration on the router can be extended to cover also the IP subnets of Vlans 10-40.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2019 02:50 AM
Many thanks for your help,
I got your correction to change the Port 1 to Access and not Trunk (I thought the switch would automatically do subnet-vlan when inter-VLAN routing is enabled instead of dropping ingress untagged packets on the Trunk).
About NAT: I verified and as you suggested, my Netgear R7000 router will only NAT its own subnet. It won't NAT traffic from other subnets. However, I can install a custom firmware to either support VLAN (I can go with port 1 as Trunk and no need for static routes I guess in this case) or support NAT for subnets and keep my above setup.
I still have a few clarifications to ask you as I am not really sure about them:
- with the above setup and NAT for subnets working on the router, can I go with regular VLAN and no need for the non standard subnet-based VLAN ? Inter-VLAN routing will take care of ingress untagged traffic through VLAN1 (no loop traffic issues)
- port 1 (connecting to the router): is it better to keep it utagged (Access) in native VLAN1 or should it be in a dedicated VLAN on its own ?
- the "Domain Name Server IP Address" in each DHCP pool: can I use the router address, that is 192.168.1.0 and the inter-VLAN routing takes care of it ? Or should the DNS IP for each DHCP pool point to the VLAN 1 address (192.168.1.1 in my setup) and configure a DHCP pool for VLAN1 with DNS IP being the router connected to it (192.168.1.0) ?
- in switch DHCP server: do I need to configure the NetBIOS, SNTP and TFTP entries as I am really not sure about their purpose in the DHCP setup
Again, many thanks for your support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2019 03:05 AM - edited 08-19-2019 03:06 AM
Hello Filomena,
if you are going to upgrade the firmware on the netgear router and you can enable the NAT for subnets not directly connected I would go this way for better performance:
enabling inter Vlan routing on netgear should provide far less performance then inter vlan routing on the switch (switch works in hardware the router is likely software based).
>> with the above setup and NAT for subnets working on the router, can I go with regular VLAN and no need for the non standard subnet-based VLAN ? Inter-VLAN routing will take care of ingress untagged traffic through VLAN1 (no loop traffic issues)
I don't understand this question inter vlan routing should remain on the switch for performance reasons as explained above
>> port 1 (connecting to the router): is it better to keep it utagged (Access) in native VLAN1 or should it be in a dedicated VLAN on its own ?
it must be in access mode Vlan 1 to create a working configuration. Both devices must have IP addresses in the same subnet to be able to communicate (to make ARP to work)
>> the "Domain Name Server IP Address" in each DHCP pool: can I use the router address, that is 192.168.1.0 and the inter-VLAN routing takes care of it ? Or should the DNS IP for each DHCP pool point to the VLAN 1 address (192.168.1.1 in my setup) and configure a DHCP pool for VLAN1 with DNS IP being the router connected to it (192.168.1.0) ?
If the subnet mask is 255.255.255.0 192.168.1.0 is reserved as the subnet address and cannot be used on the router interface. Usable addresses are 192.168.1.1 to 192.168.1.254 with 192.168.1.255 reserved for broadcast.
So if your router is using 192.168.1.254 yes you can provide it in the DNS field in each DHCP pool.
192.168.1.0 is acceptable only if the subnet mask is 255.255.254.0 and the subnet is 192.168.0.0/23.
>> in switch DHCP server: do I need to configure the NetBIOS, SNTP and TFTP entries as I am really not sure about their purpose in the DHCP setup.
These optional entries are intended to provide IP addresses of some well known servers for devices like IP phones or other that can use a TFTP server and so on.
if you don't have a TFTP server or other type of servers do not populate these fields.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2019 04:15 AM
Many thanks, things are clear and I am going to buy the Switch :-)
- The unclear question was: I go with 802.1Q regular VLAN and no need for the "subnet-based VLAN" mode on switch in my case, but I now understand that it is a yes since the inter-VLAN routing you explained will do its job
- my other question you didn't get: can I leave native VLAN 1 on its own and create another VLAN2, untagged member port 1 to router, IP 192.168.2.0/24, router on 192.168.2.1 ? Or I am obliged to untag the path to router on the native VLAN. I read some switches need the untagged ingress always on VLAN1, but read nothing in manual that would force me to use the native VLAN1 for this
Big thanks for your help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2019 04:57 AM
Hello Filomena,
>> About the first point I am not familiar with the used terms however the inter vlan routing should be performed on the switch.
>> my other question you didn't get: can I leave native VLAN 1 on its own and create another VLAN2, untagged member port 1 to router, IP 192.168.2.0/24, router on 192.168.2.1 ? Or I am obliged to untag the path to router on the native VLAN. I read some switches need the untagged ingress always on VLAN1, but read nothing in manual that would force me to use the native VLAN1 for this
You can use whatever Vlan you want to connect to the router. However the port must be in access mode and the corresponding SVI interface must have an IP address on the same IP subnet of the router.
You can even connect two different ports in access mode in Vlan 1,2 respectively to two different router ports if you want.
The native vlan is a single port characteristic used on 802.1Q trunk ports (the native is untagged).
Two different trunk ports can use different native vlans, but on each link both sides must agree on native vlan id.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-19-2019 11:31 AM
many thanks
I accepted your post as an answer
One I got the hardware and setup, I'll come back if I need more help
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2019 01:26 AM - edited 08-20-2019 01:28 AM
I have two more clarifications to ask please:
- It seems like Inter-VLAN routing on the Cisco SG350 series is global (IPv4 routing enabled on all created VLANs) and not a per-VLAN option like on some other switches/routers I read about. This means that by default all VLANs can communicate to each other and that I have to add a manual ACL rule to block traffic from specific VLANs !
Let's say if I have 5 VLANs and I want to share one of them. I would need for each VLAN to add ACL rules blocking access from each other VLAN, except for the shared one. Looks like a complex task on long term maintenance !
Is there a simpler option / wizard to isolate a VLAN without manually creating all the ACL rules ? Or is there another Cisco Switch line that makes this possible ?
- On the router, in my case, if I add a static route 0.0.0.0 192.168.1.1 (router internal IP), will it forward the traffic to the WAN port without needing to NAT the subnets ? Or I am not well understanding the difference between NAT and static routes ?
Sorry to insist with all my newbie questionings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2019 02:30 AM - edited 08-20-2019 02:34 AM
Hello Filomena,
>> it seems like Inter-VLAN routing on the Cisco SG350 series is global (IPv4 routing enabled on all created VLANs) and not a per-VLAN option like on some other switches/routers I read about. This means that by default all VLANs can communicate to each other and that I have to add a manual ACL rule to block traffic from specific VLANs !
Yes inter vlan routing is enabled at global level with an ip routing command this is true also for Cisco IOS switches.
If you want to limit connectivity you need to use an ACL applied to SVI interface.
Note: if you block one side of the communication this can be enough.
Usually ACLs on SVI are applied inbound and the source address is the Vlan subnet with its subnet mask.
see the admin guide
On pag 42 it explains how an ACL can be applied to one or more SVI vlan interfaces.
>> Is there a simpler option / wizard to isolate a VLAN without manually creating all the ACL rules ? Or is there another Cisco Switch line that makes this possible ?
Enterprise oriented switches like C3650 can support VRFs but it is probably a too complex technology for your network.
In addition each VRF would require a dedicated link to the router so the ACLs would only be moved upstream to the netgear router.
>> On the router, in my case, if I add a static route 0.0.0.0 192.168.1.1 (router internal IP), will it forward the traffic to the WAN port without needing to NAT the subnets ? Or I am not well understanding the difference between NAT and static routes ?
First of all a default static route would be
ip route 0.0.0.0 0.0.0.0 192.168.1.X
where 192.168.1.X is the IP address of the telecom router. This is called iP next-hop the router needs to be able to resolve it with ARP. You cannot use the router IP address as a next-hop.
because the default route is 0.0.0.0/0.
NAT is needed regardless of how you perform routing between the router and the switch because the IP addresses are Private (see RFC 1918) they cannot be sent over the public internet.
Routing including static routing instructs the device on how to forward packets based on their destination address.
NAT is a network address translation feature that modifies the packets changing their source IP address from private to a "public" one. With PAT or NAT overload multiple internal addresses are converted to the same public address by using different TCP or UDP ports (this is the key to be able to send return traffic to the correct internal host).
To make an example
if host 10.10.10.10 wants to reach a website at 200.200.200.200 (let use suppose it has performed DNS and got an answer) the host will create a TCP packet with:
IP source address 10.10.10.10
IP destination address 200.200.200.200
Ip protocol 6 (TCP)
TCP source port 12345
TCP destination port 80
The packet is sent to the router that will change it to its "WAN" address and it can use a different TCP port if port 12435 is in use
so
(10.10.10.10 , 12345) (200.200.200.200, 80) this is called a TCP socket is translated to
( WAN , 22500) ( 200.200.200.200, 80 ) that is another socket. Note that the destination address is not changed it is public and also the destination TCP port because it represents the type of service you want to access (a web server using HTTP in this case).
The answer from the server has then the destination address translated to 10.10.10.10 and the TCP port changed to 12345 on the router.
This is what NAT does and it is different from routing.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-20-2019 05:07 AM
sounds clear, many thanks again.
Any suggestion on an affordable Cisco router as an upgrade that will fill my needs without further complexity ?
I am thinking that for my business needs, it is a better investment to get a decent router rather than flashing custom unsupported firmware on my Netgear R7000.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 01:18 AM - edited 08-21-2019 01:19 AM
Hello Filomena,
if you want to buy a Cisco router I would go for a Cisco 800 series router.
SMB routers like RV340 may have the same limitations on NAT that your current netgear router has.
For example looking at RV340 admin guide I see an option to flag NAT enable on interfaces, so this makes me think it works only on connected subnets.
A Cisco IOS router can use an access-list to define what IP addresses need to be translated and it is not constrained to directly connected subnets.
You can go with a Cisco 881 for example.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 07:26 AM - edited 08-21-2019 10:46 AM
I was also looking at the RV series, mainly the RV345 or RV340 and thought they were fine !
In fact, the NAT config page shows no VLAN/subnet option:
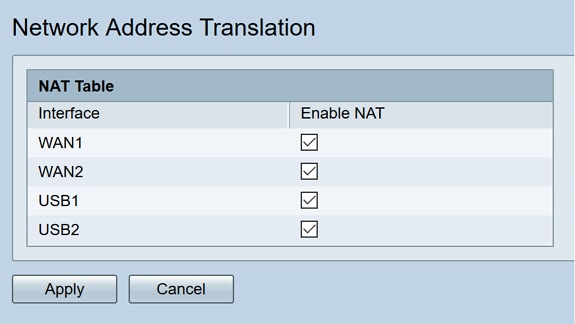
They have static NAT though... but I don't think it will do the job I guess !
However, they have a firewall setup with access rules (no ACL support, but very similar !)
source interface: VLAN1 (or VLAN as soon as other VLANs are created), no possibility to select individual VLANs if other than VLAN1:
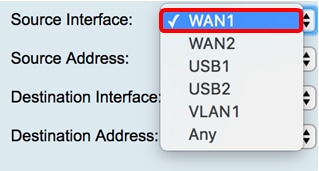
Source address (subnet possible):
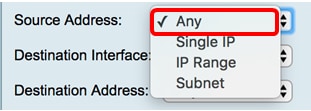
Destination interface/address (WAN1 or WAN2 in my case):
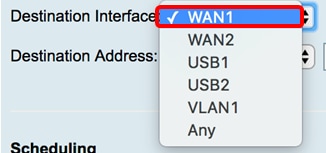
And access rules priority:
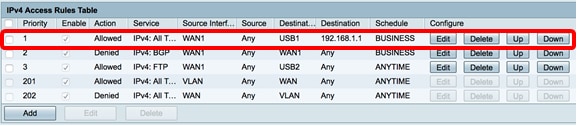
Specs do not specify if by default the NAT rules allow VLAN subnets, but I would have supposed yes since the router supports VLAN and access rules !
The number of firewall access rules is limited to 202 rules, should be enough I guess for my needs.
I imagined setting up access rules like this in router:
- source interface VLAN, source address any, target WAN1, permit any (allow internet access for all VLANs)
- source WAN1, destination interface VLAN, destination address any, permit any (is it also needed for internet access ?)
And if I want to restrict internet access to a specific VLAN, I imagined adding a rule with higher priority before the above permit rules:
- source interface VLAN, source address subnet, target WAN1, deny any (block internet access for specific VLAN subnet)
- source WAN1, destination interface VLAN, destination address subnet, deny any (is it also needed to block internet access ?)
Or I could just go with a per VLAN rule to only permit internet access to the specific VLANs I need:
- source interface VLAN, source address subnet, destination interface WAN1, permit any (allow internet access for a specific VLAN)
- source interface WAN1, destination interface VLAN, destination address subnet, permit any (is it also needed to block internet access ?)
The 800 series are 10/100 base-T, I really need 1000 Base-T even on the WAN and ideally LAG.
The 900 series: look amazing, but I fear they are too much advanced setup for my knowledge and needs
I dislike the no VPN support however: could push me to Ubiquiti. But for simplicity, I'd like to keep same brands in router/switch. I could keep the Netgear R7000 router for only OpenVPN access.
To summerize it, my new setup:
ISP Cable Modem
|
Cisco RV345 SMB router
(10.0.10.1)
+
Router Port 1 (Trunk/Tagged to all VLANs)
|
Cisco SG350 + DHCP server enabled
+ VLAN 10 (private): 10.0.10.0/24
* Port 1 (trunk) : connected to router
* Port 2 (trunk): connected to WLAN AP (3 tagged SSIDs for VLANs 10, 20 and 40)
* Port 3 (access) : management PC
+ VLAN 20 (office): 10.0.20.0/24, Ports 1-2 (trunk), Ports 4-5 (access)
+ VLAN 30 (shared): 10.0.30.0/24, Ports 1-2 (trunk), Ports 6-7 (access)
+ VLAN 40 (guest): 10.0.40.0/24, Ports 1-2 (trunk), Port 8 (access)
- RV345 router: static IP 192.168.1.1, create VLANs, disable DHCP server, disable inter-VLAN routing, firewall access rules for subnets -> WAN1, no static routes configured
- SG350 switch: DHCP pools for each VLAN, static IP for port 1 : 192.168.1.0, IPv4 routing enabled, ACL and ACE rules to manage interVLAN communication
- WLAN AP: setup with the 4 VLANs, 3 SSIDs for VLANs 10,20 and 40
- From my screen captures and config propositions, do you think the RV345 would give VLAN subnets access to internet despite the no clear specs about NAT ? Should I ask for support through an official ticket for confirmation or in dedicated forum ?
- Do I need firewall access rules in both ways (egress and ingress): subnet -> WAN and WAN -> Subnet ?
- Since I will go with a VLAN router, I guess I should now trunk the switch port 1 to the router and same with router port ?
- No more need to define static routes between subnets on router if I trunk the interface to the switch ?
Again, many thanks for all the teaching you gave me as a noob in this area
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-21-2019 11:49 PM
Hello Filomena,
you need to make a tradeoff / compromise between what you can do.
Using an RV340 router for me means moving inter vlan routing from the SG350 (a multilayer switch working in hardware) to a SW based router.
Yes, the RV340 may have a GE interface to connect to the internet but:
a) as many SW based routers it may be not able to support a GE at full speed
b) if used for intervlan routing it becomes a bottle-neck as the inter vlan traffic is limited to the one GE trunk between the router and the switch. (traffic counts twice a 50 Mbps flow between Vlan 10 and Vlan 20 will use 50 Mbps in both directions on the link between router and switch)
If instead you use the SG350 as multilayer switch the inter vlan routing is not limited to 1 GE in total but it is limited by the switching fabric bandwidth that should be at least of 10-20 Gbps.
I see a big difference here.
I don't think the RV340 can perform NAT for not directly connected subnets as you can see in the GUI there is a NAT enable flag for connected interfaces. I remember a thread where we tried with another user to enable NAT for static routes with no success.
You know your network scenario and your needs.
In my opinion is better to have far better local inter vlan routing performance on the SG350 and have a router able to perform NAT for not directly connected subnets even if this means a slower internet connection.
If your end users are using any SaaS (software as a service ) like MS Office365 Google equivalent or you have cloud connection then you need a very fast and symmetric internet pipe.
If most of the traffic is local between Vlans the solution with the SG350 performing inter-vlan routing is to be preferred.
Of course, if you change the network design the port 1 of the switch must become a trunk carrying all Vlans but that port becomes the bottle neck of performance in inter vlan routing.
Your understanding of FW rules on RV340 is correct, but I would not go with this router for the afore mentioned limitations on NAT.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2019 03:19 AM - edited 08-22-2019 08:33 AM
This is really bad news.
I currently have all the devices on a single subnet behind a switch. The communication between devices in local doesn't depend on router except for DHCP server and WAN access.
I also clearly need the 500 Mbps internet speed I currently have on the WAN side.
I want to keep the inter-VLAN routing on the switch, for the same reasons you mentioned, no devices will be directly connected to the router except the ISP modem and the switch. That's why I am attracted by the DHCP server feature on the SG350.
Now, if I also enable the inter-VLAN routing on the RV345 router, the intranet inter-VLAN routing would still be done on the switch interface at wire speed I guess since all devices are directly connected to the switch, right ? It won't drop to software inter-VLAN communication on the next node, the router in my case !
I also was sure that eventually enabling inter-VLAN routing on the RV345 router would give the VLANs internet access, else it is a useless setup for most people needing a VLAN I guess ! Really wired :-(
Next business 1GB class WAN routers are another price, but mainly another layer of complexity to setup for a small business like I want !
Any further thoughts or it is a really no way ?
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
