- Cisco Community
- Technology and Support
- Networking
- Switching
- N3K and FTD Routing and Switching Security design
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2021 07:28 AM
Hello everyone,
I need a best practice design for this scenario,
There are multiple VLANs each VLAN have a different subnet, and there are two Cisco Nexus 3048 Base License, OR two C9300 Stacking, must choose one of them Nexus OR C9300 I can't use both of them on the environment,
and there are two Cisco FTD working as HA,
I need to run the Nexus as an access and core switch so all hosts will use Nexus as a default gateway, also I need to isolate some subnets to reach each other by forwarding the traffic to the FTD to inspect it before access to the end,
Example:
Application Zine - VLAN 100 - with subnet 10.10.10.0/24 Gateway 10.10.10.1 Nexus.
Database Zone - VLAN 200 - with subnet 20.20.20.0/24 Gateway 20.20.20.1 Nexus.
The FTD has a valid IP on each VLAN, for, example 10.10.10.2 and 20.20.20.2 but this is not to be used as the default gateway on the hosts.
I need the nexus to forward the traffic to FTD to inspect it instead of direct L3 forwarding,
also in the same scenario, there are some VLANs must communicate with each other via Nexus not via FTD
Example:
Database Zone - VLAN 200 - with subnet 20.20.20.0/24 Gateway 20.20.20.1 Nexus.
BackUP Zone VLAN 300 - with subnet 30.30.30.0/24 Gateway 30.30.30.1 Nexus.
in this case, the nexus will forward the traffic directly between different VLANs, this option is needed to get the highest network speed,
-------------------------
Thanks
Solved! Go to Solution.
- Labels:
-
Catalyst 9000
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 05:01 AM
Hello @a.aljiledi ,
you can use VRFs on the Nexus so that each Zone has its own routing table and the default route for each VRF/zone will be pointing to an FTD dedicated logical link.
For causing FTD bypass for some subnets you should use the partial extranet concept that is you run MP BGP on the Nexus and you play with route targets.
The idea is that a shared subnet would be exported with multiple route targets values attached to it so that it can be imported in another VRF.
Most specific routes are preferred over default routes so leaked routes would bypass the FTD.
Before attempting to provide a config example you should check if you can run VRFs and MP BGP with your Base license on the Nexus switches.
A similar setup can be done with Catalyst 9300 with appropriate license.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 11:50 AM
Hello All
these configuration steps from A to Z
Leaking Routes with MP-BGP - Network Direction
OR
3- Leaking between VRFs Using MP-BGP - YouTube
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-22-2021 11:38 AM
i suggest making a small network diagram of how they are physically connected, so we can understand better.
as Long you have segmented the network between Zones on Layer2/Layer 3 level, you can have the different options on how you can achieve each task. for that, we need to understand the physical layout.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2021 07:05 AM
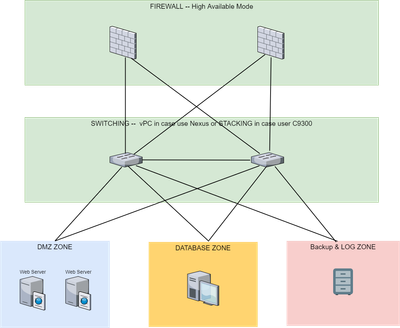
This is a simple diagram, that shows three different network Zone, on this scenario I need the traffic between DMZ and DATABASE to be inspected by the firewall so the firewall response for the routing between these ZONEs, and the traffic between DMZ, DATABASE to Backup Zone will be routed by the switch,,,
all servers must use the switch as a default gateway...
Thanks...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 05:01 AM
Hello @a.aljiledi ,
you can use VRFs on the Nexus so that each Zone has its own routing table and the default route for each VRF/zone will be pointing to an FTD dedicated logical link.
For causing FTD bypass for some subnets you should use the partial extranet concept that is you run MP BGP on the Nexus and you play with route targets.
The idea is that a shared subnet would be exported with multiple route targets values attached to it so that it can be imported in another VRF.
Most specific routes are preferred over default routes so leaked routes would bypass the FTD.
Before attempting to provide a config example you should check if you can run VRFs and MP BGP with your Base license on the Nexus switches.
A similar setup can be done with Catalyst 9300 with appropriate license.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2021 05:53 AM - edited 09-26-2021 05:54 AM
Thanks @Giuseppe Larosa for this idea,,,
I see it is supported by the Essentials license
so there is any configuration steps for this scenario, actually, I don't have experience with BGP...
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 11:12 AM
hello @Giuseppe Larosa
so if i use BGP for route leaking can i allow traffic between 2 different VRFs or just i can allow it from VRF to GRT,,,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 02:20 PM
Hello @a.aljiledi ,
MP BGP is the right tool for leaking routes between VRFs .
MP BGP cannot be used for route leaking between a VRF and the Global Routing Table, because routes in GRT have no RT associated to them so it is not possible to play with route targets in this case.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 11:50 AM
Hello All
these configuration steps from A to Z
Leaking Routes with MP-BGP - Network Direction
OR
3- Leaking between VRFs Using MP-BGP - YouTube
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-28-2021 02:36 PM - edited 09-28-2021 02:39 PM
Hello @a.aljiledi ,
the first link provides a basis for you what you need to.
You would need a more complex configuration using export-map that invokes a route-map that defines what prefixes of a given VRF should have an additional route target RT attribute ( mutiple can be associated to same prefix like it happens for standard BGP communities) so that the selected prefixes are imported to another VRF
look at slide 64 of following Cisco Live presentation
https://www.ciscolive.com/c/dam/r/ciscolive/us/docs/2018/pdf/BRKMPL-2102.pdf
it is exactly what you need and pay attention to the additive keyword used in the route-map invoked as export-map
route-map Export-VRFA-to-VRFB permit 10
match address 2
set extcommunity rt <VRFB-RT-import-value> additive
without the additive keyword prefix(es) matching ACL 2 will be sent out without multiple route targets and this is not what you need at least in multi nodes scenarios.
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2021 04:37 AM
Any Idea ??
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide