- Cisco Community
- Technology and Support
- Networking
- Switching
- SPAN port to validate MACSEC/TrustSEC
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SPAN port to validate MACSEC/TrustSEC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-10-2022 06:36 PM
All:
I'm about to run a P.O.C. evaluation of MACSEC/TrustSec technology.
For part of that, I'll want to validate the encryption of the payload inside the Layer2 Frame payload on the wire (and the details of the MACSEC 16 byte header)
If I use a SPAN port to capture traffic from the protected source/destination, I'll be seeing the frame contents pre-transmit-encrypted (or post-receive-decrypted) on the SPAN port destination port, correct?
E.g., With SPAN, the frame is duplicated/copied from the Transmit buffer before it transmits pm MAC Layer (Optical or Copper)
My understanding is that the payload hashing of MACSEC frames occurs in hardware (programmed by software, but at the time of transmit after the frame queues in the outgoing transmit buffer)
So do I need to use a passive optical splitter to make a validation on-the-wire?
Thanks, ~BAS
- Labels:
-
Other Switching
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-11-2022 01:58 AM
check below thread may help you :
https://community.cisco.com/t5/network-security/macsec-on-mirror-port/td-p/4300635
=====Preenayamo Vasudevam=====
***** Rate All Helpful Responses *****
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2023 10:25 PM
Your answer is not relevant to the thread. He is running mcasec on the span source, not the span destination.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-27-2023 10:25 PM
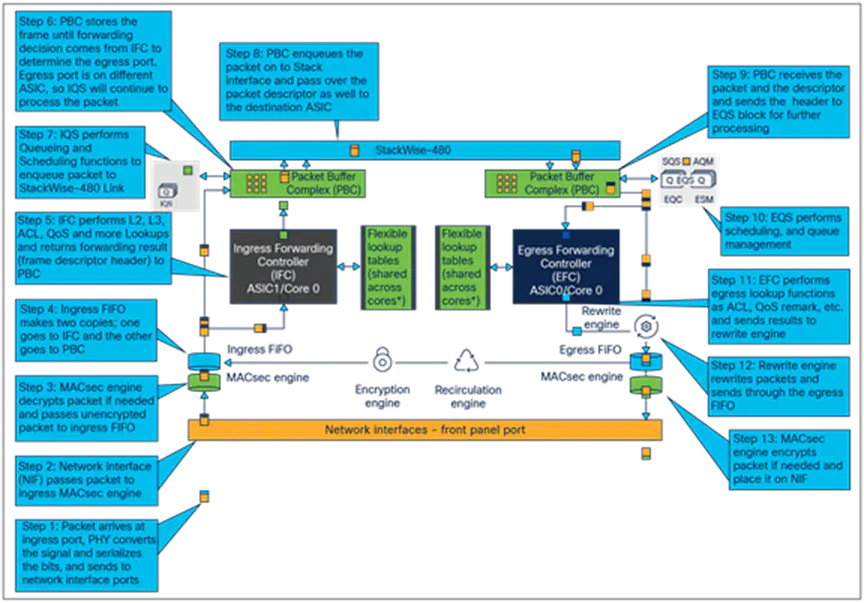
May be too late for you but leaving it here for others. At least on C9300, you're correct, SPAN cannot see the encryption, as macsec encryption is done after SPAN on egress and decryption before SPAN on ingress.
Cisco Catalyst 9300 Series Switches Architecture White Paper - Cisco
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide