- Cisco Community
- Technology and Support
- Collaboration
- Unified Communications Infrastructure
- Re: CUCM sftp backup to linux fail
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
CUCM sftp backup to linux fail
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2016 04:01 AM - edited 03-19-2019 10:33 AM
Hi,
I'm following the guide: http://cdesigner.eu/content/14-cucm-8-free-sftp-solution-backup-ubuntu-1004-server
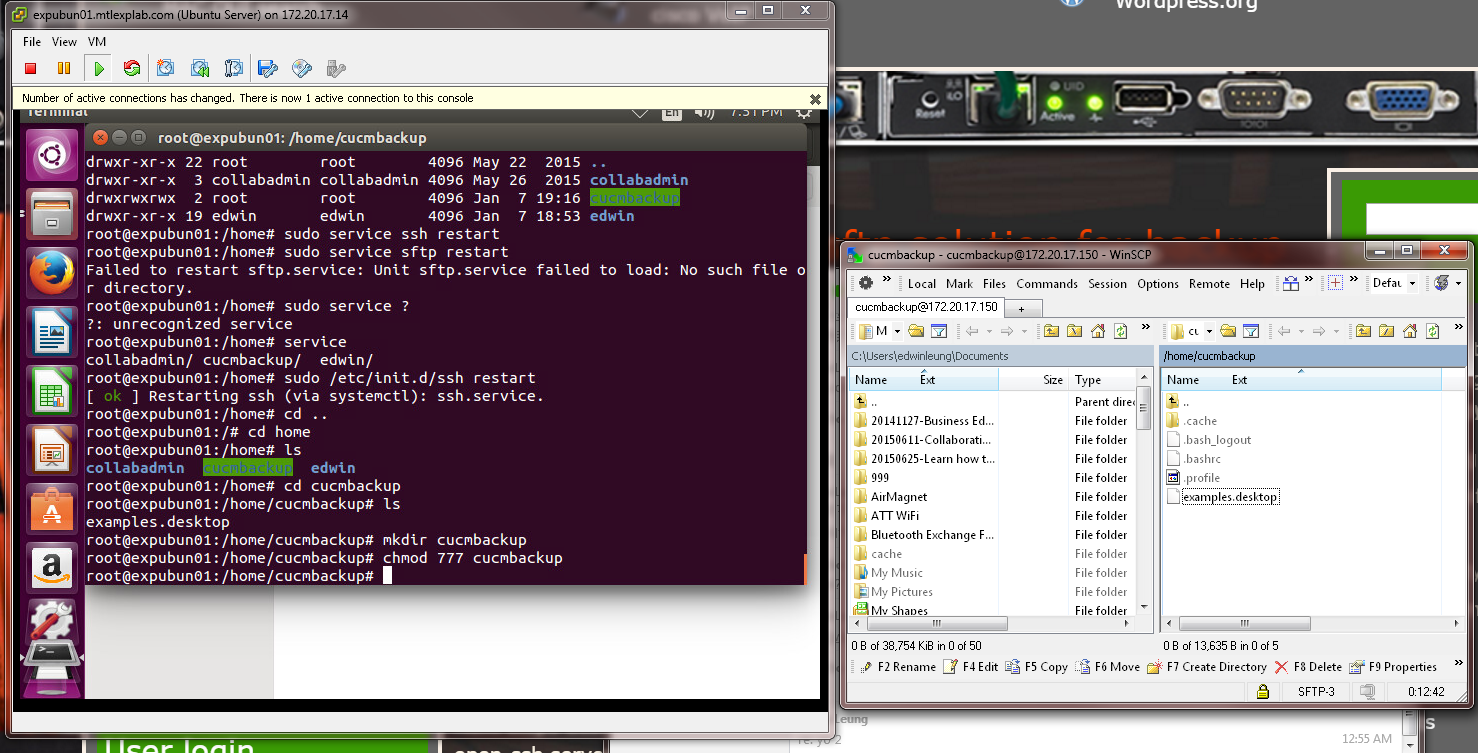
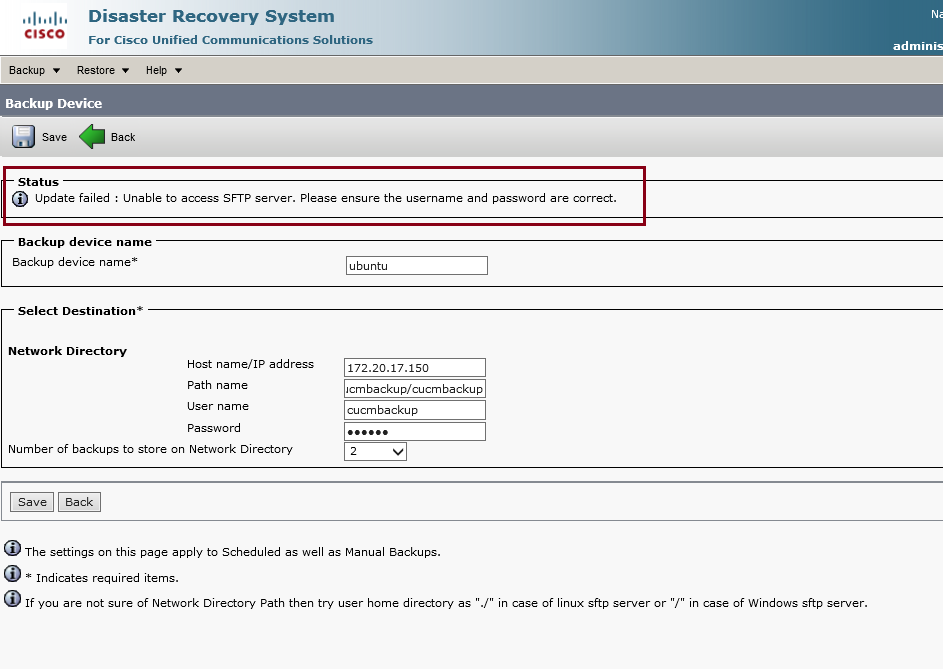
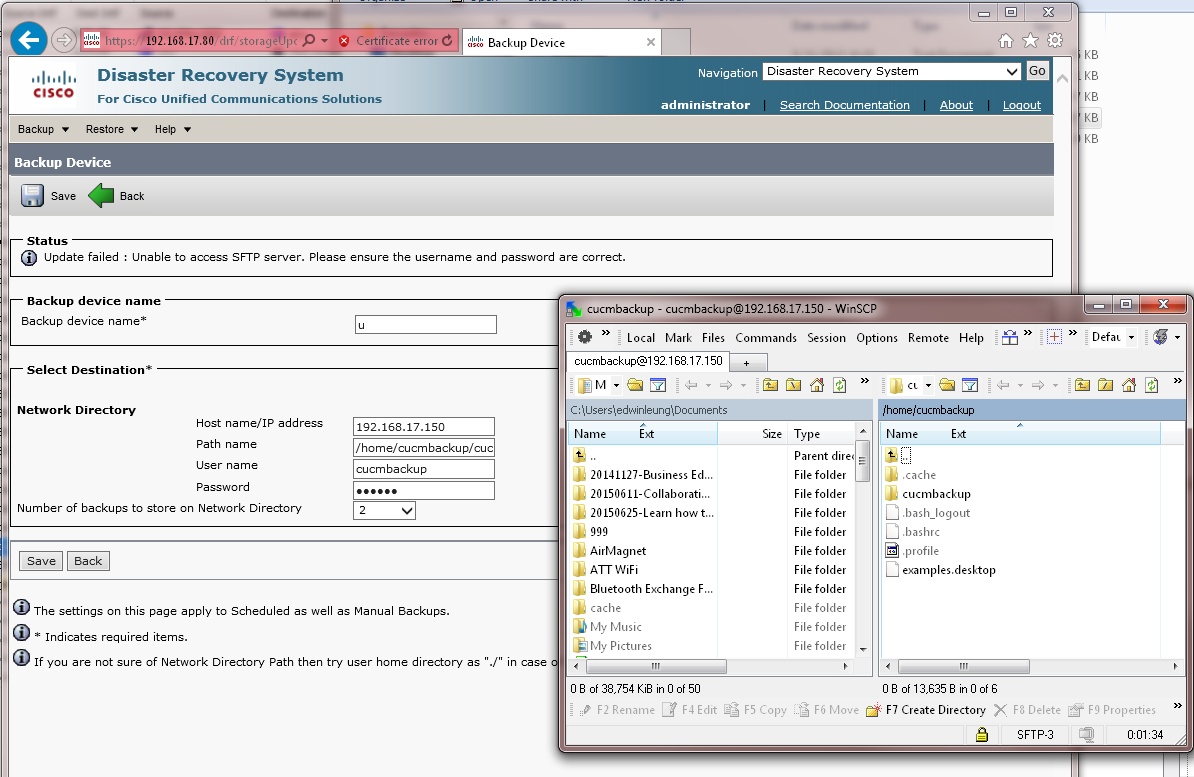
To install the ubuntu 15 as OpenSSH SFTP backup, but it got the fail on it
Error: Unableto access SFTP server. Please ensure the username and password are correct.
I followed all steps as same:
1) Create group for sftp access (optional) for further platform hardening - sudo groupadd sftpuser
2) Create user account for backup sudo adduser cucm_8 sftpuser and make password during user creation dialog
3) Change ownership of home directory sudo chown root.root /home/cucm_8
4) Alter permission for read and write to home directory of backup user sudo chmod 777 /home/cucm_8
5) Install open-ssh server sudo apt-get install openssh-server
6) Test connectivity to sftp account from FileZilla client (or your preferred supporting secure mode) - transfer and delete file!!!
- Labels:
-
UC Applications
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2016 10:12 AM
System version: 10.5.2.10000-5
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2016 10:59 AM
Hi.
Please on your linux server give chmod -R 777 home/cucmbackup/
Try again and let me know
Thanks
Carlo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2016 08:29 PM
was 777 already... but same error

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2016 10:11 PM
Hi,
now I think we have an issue in cipher algorithm configured on linux server and the one supported by CUCM.
Please refer to the following post and check your sshd config.
https://supportforums.cisco.com/discussion/12407216/cucm-backup-openssh
Also try again the command we previously suggested to transfer files from CUCM through cli and check auth logs on linux server.
Please let let us know
Regards
Carlo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2016 09:51 AM
Unfortunately, I changed the Linux server as the same subnet of CUCM and it got the same error. Is it the wrong settings on Linux SFTP server?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-07-2016 05:55 AM
try command
file list tftp *
or to be more specific
file list tftp Ringlist.xml
for downloading file
file get tftp Ringlist.xml
regds,
aman
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-20-2017 04:24 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-20-2017 05:52 AM
See my original reply above. The latest synology software has an updated ssh that would cause this problem. You may need to contact synology on how to change the key exchange algorithms if you can't just ssh into it and edit the file.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-20-2017 06:59 AM
my synology version is DSM 6.0.2-8451 Update 2
how do i check this thing you are mentioning?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-04-2016 12:02 PM
Not sure if you ever figured this out but I had the same problem after updating linux. OpenSSH removed a bunch of insecure ciphers which are still used by a good bit of Cisco stuff. With CCUM 10.0 I had to turn those ciphers back on. In my testing the below works.
Edit /etc/ssh/sshd_config and add:
Ciphers +aes128-cbc
KexAlgorithms +diffie-hellman-group1-sha1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-11-2016 12:39 PM
Edit /etc/ssh/sshd_config and add:
Ciphers +aes128-cbc
KexAlgorithms +diffie-hellman-group1-sha1
Same scenario, this was the fix for me.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-19-2018 06:25 AM
Had to change the network config to work with ens32 and systemd-networkd:
http://xmodulo.com/switch-from-networkmanager-to-systemd-networkd.html
Had to enable ssh in the iptables - sudo ufw allow ssh
And and finally the above commands here after verifying that I could access the SFTP server with the CUCM credentials via WinSCP, and logging directly into the SFTP server with the CUCM credentials.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2021 04:08 PM
Gracias Mark Fisher.
Esto funcionó para mi.
Tengo un CUCM 11.5 y un SFTP SERVER basado el linux Ubuntu 20.04.
Logré configurar el backup device y un schelude colletion hacia el servidor SFTP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-14-2017 10:46 PM
Ciphers aes128-cbc,3des-cbc,blowfish-cbc
save and restart service sshd
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-11-2021 12:42 PM
That could break SSH connections that are dependent on other ciphers. Here is the config snippet I use in sshd_config to allow a server to be an SFTP server for DRS.
KexAlgorithms +diffie-hellman-group1-sha1 KexAlgorithms +diffie-hellman-group-exchange-sha1 Ciphers +aes128-cbc Ciphers +3des-cbc
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide


