- Cisco Community
- Technology and Support
- Collaboration
- Collaboration Applications
- OAuth for Office 365 - Unity Connection 12.5 SU2
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
OAuth for Office 365 - Unity Connection 12.5 SU2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-04-2020 07:11 AM
This just came out yesterday so this is more directed for anyone lurking at Cisco, but how is this supposed to work?
Our UM has been disabled for months because of MS security requirements for resellers that broke the old way so I quickly installed this in my test lab to see if it will fix my issue.
According to all the MS documentation there should be no need to use the old Autodiscover, etc that Unity was using. You just connect to the default outlook.office365.com EWS url and use your oauth info and boom. The whole point is to not have to setup an account with special permissions, etc.
However, the fields for the old account are still there and mandatory and all the test options are going through and failing Autodiscover…
If I look at the Mailbox Sync Logs I don’t see any evidence it’s trying to use Oauth/EWS.
Anyone in the know out there?
- Labels:
-
Other Collaboration Applications
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-05-2020 04:43 AM
Hi,
As per Cisco documentation, for using OAuth2 web authentication mode, you must create and register an application on Microsoft Azure portal corresponding to the Unified Messaging Service. Please refer below document for detailed steps:
Thanks, Vaijanath S.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-10-2020 06:37 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2020 04:18 AM - edited 04-09-2020 04:21 AM
Did anyone resolved problem with autodiscovery? With basic authentication it looks fine, but when I only activate and switch into oauth2 it stops autodiscovering... On user configuration page it says "Unable to locate an Exchange server at which to access email_address"
I went through the provided guide, but I get the same result as Jon.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2020 04:58 AM - edited 04-09-2020 05:11 AM
We have same error - basic works, but when switching to OAuth2 ... autodiscovery error.
So mostly another case for TAC and to go trought logs :D
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 11:10 AM
I have the same issue.
I noticed the addresses do not match between Basic and oAuth
oAuth uses:
https://autodiscover.outlook.office365.com/autodiscover/autodiscover.xml
Basic uses:
https://OUTLOOK.OFFICE365.COM/autodiscover/autodiscover.xml
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-04-2020 02:33 PM
See above for my settings screen. This is working.
Things of note, my account is a dedicated one created on our non primary domain that DOES NOT have sso enabled.
Further if you have conditional access enabled with MFA you may need to bypass the default that blocks legacy items and create a special exception just for your UM Account. Somehow the initial process still uses some sort of legacy authentication then switches to oauth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-05-2020 08:33 AM
I had a support call with Cisco:
Ultimately we had to change the password on the service account:
https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvt29541
Mine had a special character in it.
We changed the password to just Uppercase, Lowercase and numbers.
Then we deleted the Unified Messaging Service Account in Unity Connection and then Added it back in with a Different Name.
Mine is now working
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2022 12:20 PM - edited 07-29-2022 12:22 PM
This resolved the issue I was having with 12.5.X as well. I will note that it did not work initially I had to try a couple times including building a new profile. However I think what ended up causing it to finally work was selecting the "Reset" next to "Synchronize Connection and Exchange Mailboxes (Single Inbox)" and then my test finally succeeded in connecting.I was also able to get it to work with my original profile which made it simpler.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-25-2023 07:11 AM
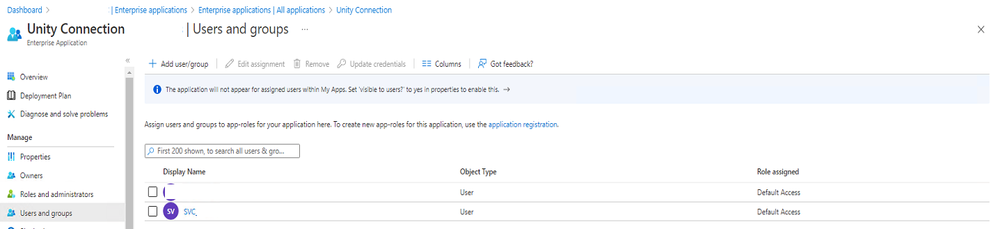
I recently found that if using a third-party Authentication provider (Duo Authentication, etc.), you will need to create an <domain>.onmicrosoft.com service account and give the necessary permissions to Impersonate as well as give permissions to the application itself Azure Active Directory > Enterprise Applications > (Application Name) > Users and Groups
Hope this additional information saves others the hours of authentication t-shooting we just went through...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2023 06:33 AM
on 12.5 we dont show the oauth2 in the drop down menu, does it magically appear when you add the azure? or are there certain versions of 12.5 that show oauth2 in the drop down? I did upgrade one customer to 11.5 su 11 and it had the oauth2 in the drop down. Thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2023 06:56 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-06-2022 11:19 AM
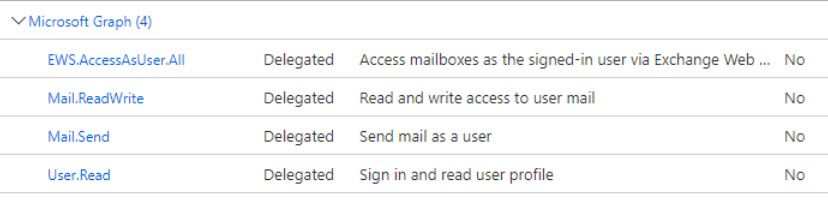
So for those of you struggling with poor email delivery and MWI times this is because Cisco is recommending you use the EWS API's which are terrible (and slow). The correct API's to use within the Oath Application process should be Graph API's (EWS will be deprecated soon anyways). Here's the permissions to use for Graph. The performance improvements are staggering (5 minute delivery and MWI times with EWS vs 15 seconds with Graph). Your Microsoft admins will thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2022 09:36 AM
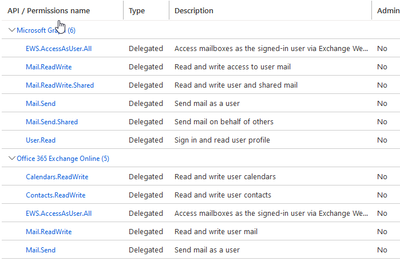
I am in the process of creating the Application, should I remove all permissions from the Office 365 section or can I leave the permissions in both?
Also, if some users need to check voicemail on a share box, do I need to have the mail.readwrite.shared?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-31-2023 03:15 PM
Not sure if you have already resolved this issue and for information to others, I have consolidated steps to enable and configure OAuth 2.0 with Cisco Unity Connection Unified messaging.
Here are the steps in summary:
- Verify Unity Connection for OAuth support
- Service Account in AD/Office365
- Register an application in Microsoft Azure
- Configure CUC Unified messaging for OAuth 2.0
Please refer my blog below for steps in detail: https://voiptechwikis.com/unified-messaging-oauth/
Thanks.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide