- Cisco Community
- Technology and Support
- Collaboration
- IP Telephony and Phones
- Using MIC cert is not
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco Phone VPN, save authentication password
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2015 09:46 AM - edited 03-17-2019 03:02 AM
Hi,
is there a way to save the user/password during VPN authentication process?
We are running CUCM 9.1.2 + ASA for register 2 IP Phone. The problem is that when the phones got unregister because some electrical or internet issue at the remote site someone has to write user/pass again, for End User is not a easy task.
Any help would be appreciated.
Regards
Please remember to rate useful posts clicking on the stars below.
LinkedIn Profile: do.linkedin.com/in/leosalcie
- Labels:
-
Other IP Telephony
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2015 05:38 AM
Answering my own question, the answer is yes...
Cisco VPN Phone support Certificate Authentication. The configuration details below:
Certificate Authentication Configuration
In order to configure certificate authentication, complete these steps in CallManager and the ASA:
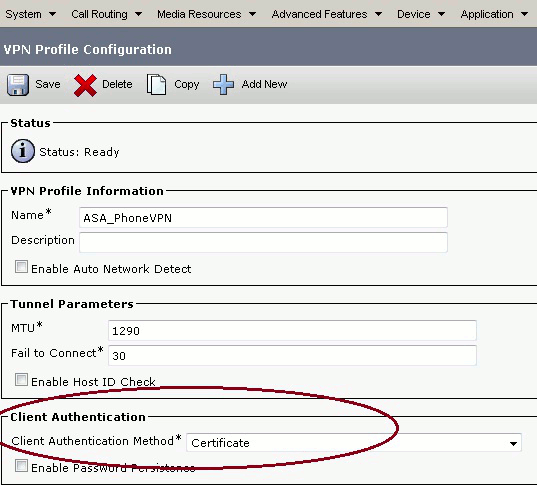
From the menu bar, choose Advanced Features > VPN > VPN Profile.
Confirm the Client Authentication Method field is set to Certificate.
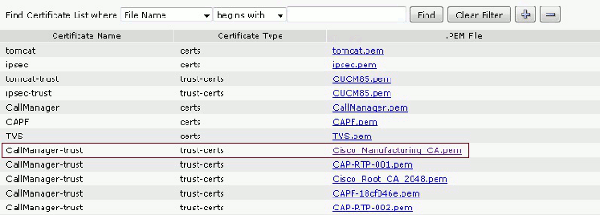
Log in to CallManager. From the menu bar, choose Unified OS Administration > Security > Certificate Management > Find.
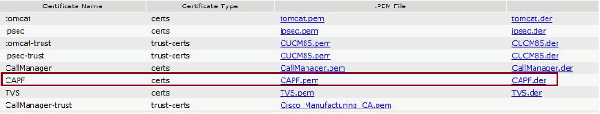
Export the correct certificate(s) for the selected certificate authentication method:
MICs: Cisco_Manufacturing_CA - Authenticate IP Phones with a MIC
LSCs: Cisco Certificate Authority Proxy Function (CAPF) - Authenticate IP Phones with an LSC
Please remember to rate useful posts clicking on the stars below.
LinkedIn Profile: do.linkedin.com/in/leosalcie
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-21-2015 06:01 AM
Using MIC cert is not recommended by Cisco due to ease of hacking the access. From:
http://www.cisco.com/c/en/us/support/docs/unified-communications/unified-communications-manager-callmanager/115785-anyconnect-vpn-00.html
Note: Cisco recommends that you use MICs for LSC installation only. Cisco supports LSCs to authenticate the TLS connection with CUCM. Because MIC root certificates can be compromised, customers who configure phones to use MICs for TLS authentication or for any other purpose do so at their own risk. Cisco assumes no liability if MICs are compromised.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2016 10:24 AM
Reviving an old post to help anyone else.
Right underneath the Client Authentication Drop-down box you circled, there's a checkbox for "Password Persistence" that would solve your initial problem, fyi.
-Tony
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide