- Cisco Community
- Technology and Support
- Collaboration
- IP Telephony and Phones
- Installing CA Signed Tomcat Certificate on CUCM
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 04:44 AM - edited 03-17-2019 01:25 PM
Hi Team,
I have installed CA signed Tomcat Certificate by following Jaime Sir's Video on CUCM.
When I try to log into CUCM using FQDN i can see "Secure Connection" mark.
But when i try to log into same CUCM using IP address or only Hostname i still get " Your connection is not secure".
Am i missing something. Are there any Pre-requisites with respect to domain and DNS ?
Solved! Go to Solution.
- Labels:
-
CUCM
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 05:34 PM - edited 09-05-2018 05:26 AM
No public ca will touch that CSR for sure.
If you local one doesn’t have a problem with it you can always try if should work however why bother with it. Just make yourself some book marks. However those other names would need to be in your SANs field not CN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2018 12:09 AM
no if requesting a certificate from a public CA, the CN can only contain ONE name, either domain name or FQDN. the other names must be specified in the SAN
depends on the CA if only names within the same domain as the CN are accepted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2018 07:44 AM
the common name (CN) is the DNS host name of the CUCM, other addresses go in the SAN (Subject Alternate Names), this guide will better explain what you need from a CUCM perspective >> https://www.cisco.com/c/en/us/support/docs/voice-unified-communications/unified-communications-manager-callmanager/115957-high-level-view-ca-00.html#commonsubject
feel free to go through the whole TechNote
Hope this helps - please rate if helpful
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 05:23 AM
there must be a match between names in the certificate and the url that you use to access the CUCM
so either you need multiple certificates (hostname, FQDN, IP-address) or you need a single (FQDN) certificate that specifies IP address and shortname as SAN (subject alternative name / alias)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 05:38 AM
unfortunately ive not seen this Video, but Generally speaking, certificates are created for the hostname/FQDN of the server in this case the CUCM, as a result if you browse to the IP address it does not recognise it and will show you an error, you can test this by visiting https://www.google.com and thereafter https://64.233.162.105 you will see a difference. in theory you can add IP address in the SAN but this is not normal practice
Hope this helps - please rate if helpful
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 09:55 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 03:32 PM
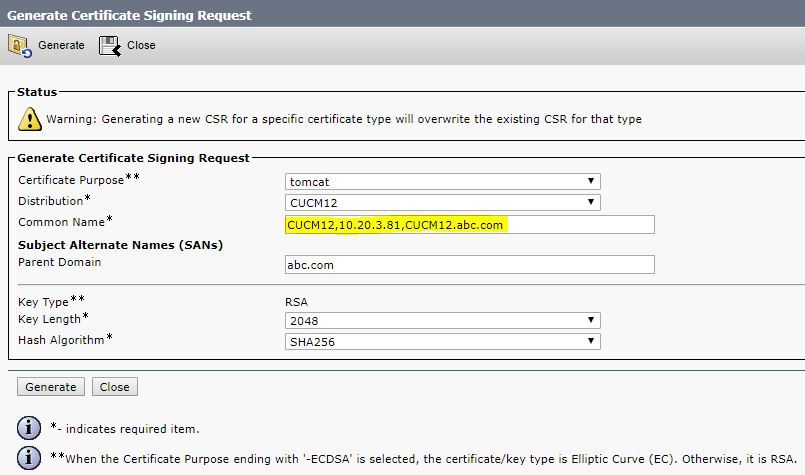
What if I put Hostname, IP Address and FQDN while generating CSR from CUCM.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 05:34 PM - edited 09-05-2018 05:26 AM
No public ca will touch that CSR for sure.
If you local one doesn’t have a problem with it you can always try if should work however why bother with it. Just make yourself some book marks. However those other names would need to be in your SANs field not CN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-04-2018 09:04 PM
https://support.dnsimple.com/articles/what-is-common-name/
java
if this helps, please rate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2018 12:09 AM
no if requesting a certificate from a public CA, the CN can only contain ONE name, either domain name or FQDN. the other names must be specified in the SAN
depends on the CA if only names within the same domain as the CN are accepted.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-05-2018 07:44 AM
the common name (CN) is the DNS host name of the CUCM, other addresses go in the SAN (Subject Alternate Names), this guide will better explain what you need from a CUCM perspective >> https://www.cisco.com/c/en/us/support/docs/voice-unified-communications/unified-communications-manager-callmanager/115957-high-level-view-ca-00.html#commonsubject
feel free to go through the whole TechNote
Hope this helps - please rate if helpful
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide