- Cisco Community
- Technology and Support
- Security
- Security Blogs
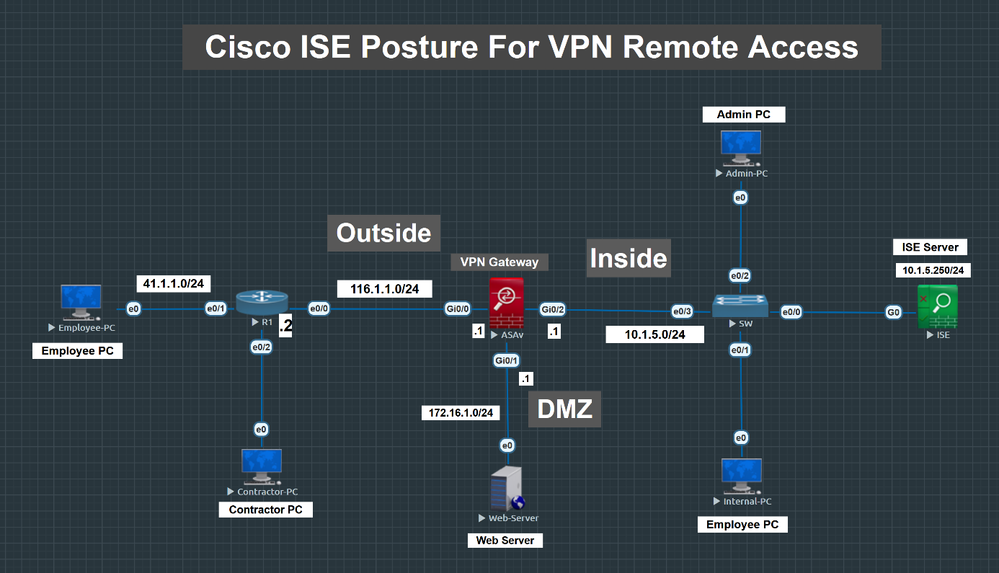
- Cisco ISE Posture Configuration for VPN Remote Access
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Step 1: Configure posture conditions
Windows Assets can be marked as ‘Compliant’ when:
- Windows update agent is running
- Any Firewall product is running
- Any Anti-Malware software is installed
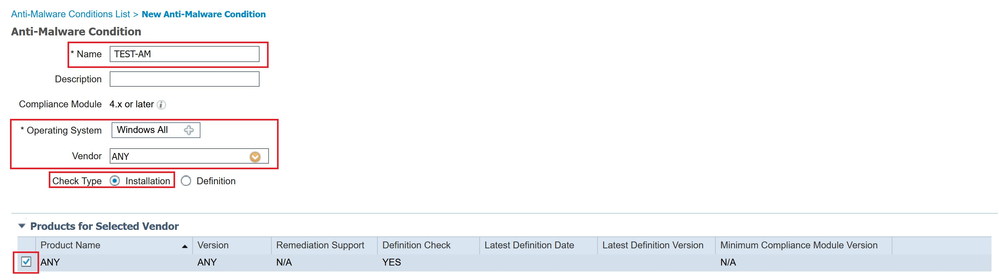
Create a condition for Anti-Malware, navigate to (1)Work Centers → (2)Posture → (3)Policy Elements → (4)Conditions → (5)Anti-Malware and press Add.
Click Submit to save the new condition.
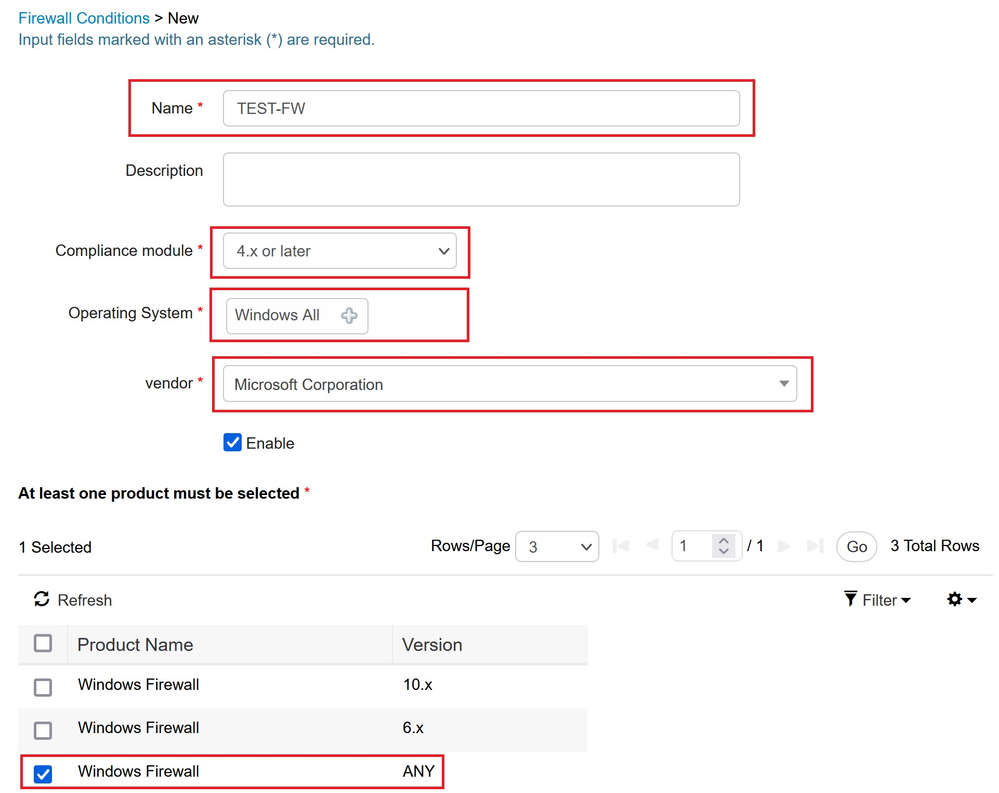
Create a condition for Firewall check, navigate to (1)Work Centers → (2)Posture → (3)Policy Elements → (4)Conditions → (5)Firewall Condition and press Add.
Click Submit to save the new condition.
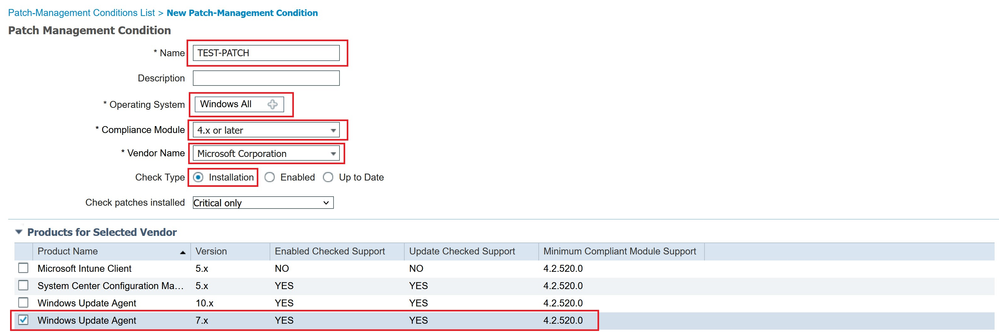
Create a condition for Windows update check, navigate to (1)Work Centers → (2)Posture → (3)Policy Elements → (4)Conditions → (5)Patch Management and press Add.
Click Submit to save the new condition.
Step 2: Configure posture requirements
Posture requirement is a configuration item on ISE which connects Posture Conditions with Posture Remediation actions. In other words, we define what the agent needs to check (Requirement) and what the agent needs to do in case the specified posture conditions have not been met (Remediation) such as'Message text only' remediation which could be defined directly in the posture requirement.
To create Posture Requirements, navigate to (1)Work Centers → (2)Posture → (3) Policy Elements → (4)Requirements.
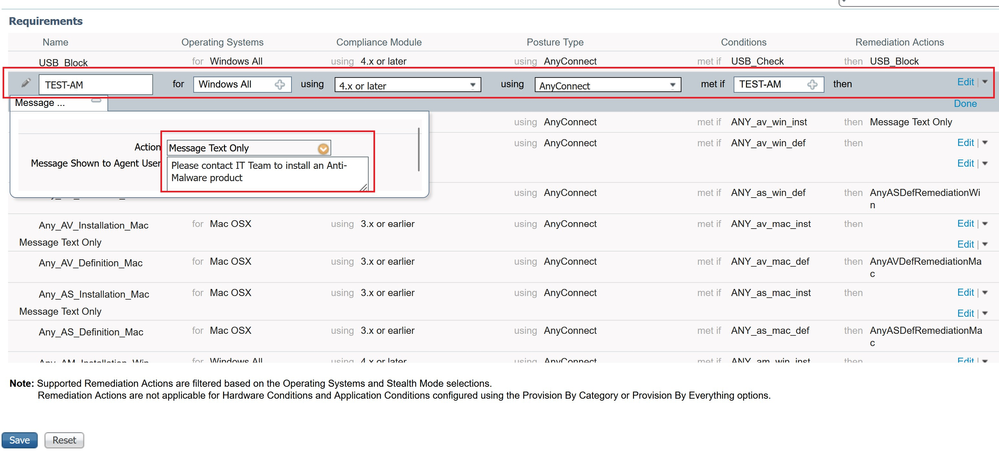
- Define a requirement name – TEST-AM
- As OS select – Windows All
- For compliance module select – 4.x or later
- Select as agent – AnyConnect
- Define a posture condition - Select the previously created TEST-AM condition from the list
- Define a remediation action - In the remediation list, select ‘Message Text Only’ and add a txt
The final configuration of the Anti-Malware requirement should look like the below example.
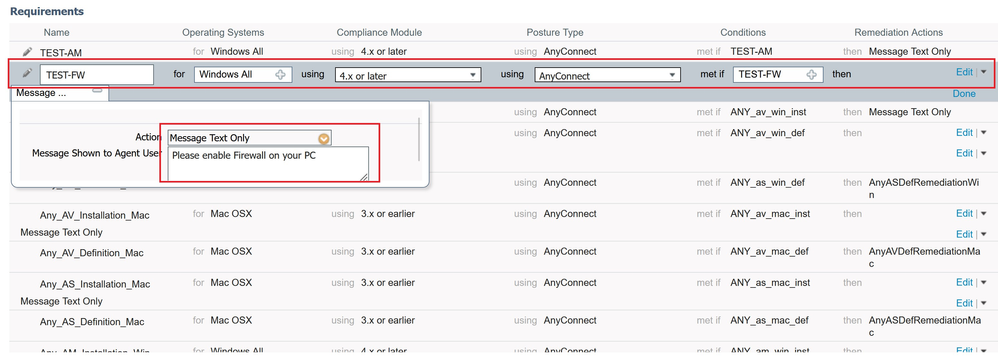
- Define a requirement name – TEST-FW
- As OS select – Windows All
- For compliance module select – 4.x or later
- Select as agent – AnyConnect
- Define a posture condition - Select the previously created TEST-FW condition from the list
- Define a remediation action - In the remediation list, select ‘Message Text Only’ and add a txt
The final configuration of the Firewall requirement should look like the below example.
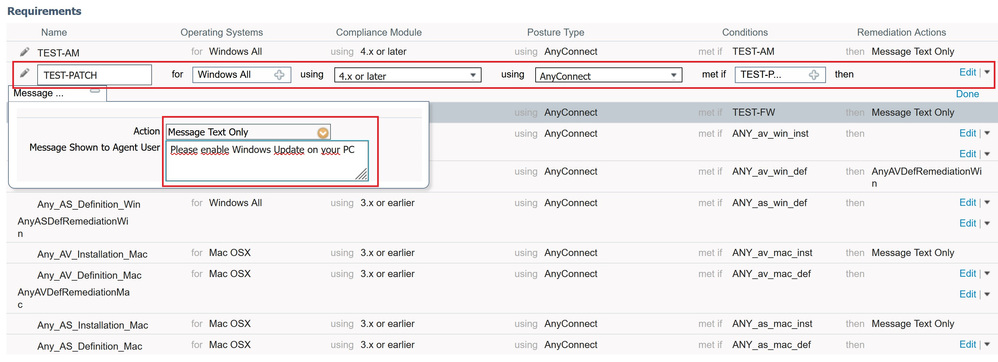
- Define a requirement name – TEST-PATCH
- As OS select – Windows All
- For compliance module select – 4.x or later
- Select as agent – AnyConnect
- Define a posture condition - Select the previously created TEST-PATCH condition from the list
- Define a remediation action - In the remediation list, select ‘Message Text Only’ and add a txt
The final configuration of the Windows Update requirement should look like the below example.
Step 3: Configure a posture policy
We need to define a posture policy which will be used for both redirect and non-redirect flows.
To create a new posture policy, navigate to (1)Work Centers → (2)Posture → (3) Posture Policy.
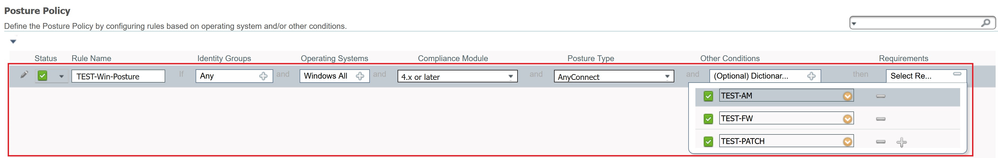
- Policy name – TEST-Win-Posture
- Operation Systems – Windows All
- Compliance Module – 4.x or later
- Posture Type – AnyConnect
- Requirements – Select all three requirements created in Step 2 (TEST-AM, TEST-FW and TEST-PATCH)
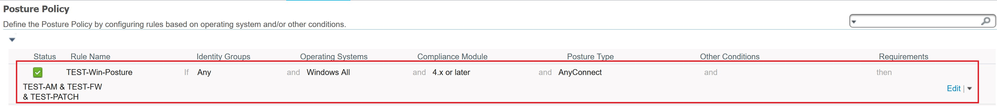
Final configuration of the posture policy should look like the below example.
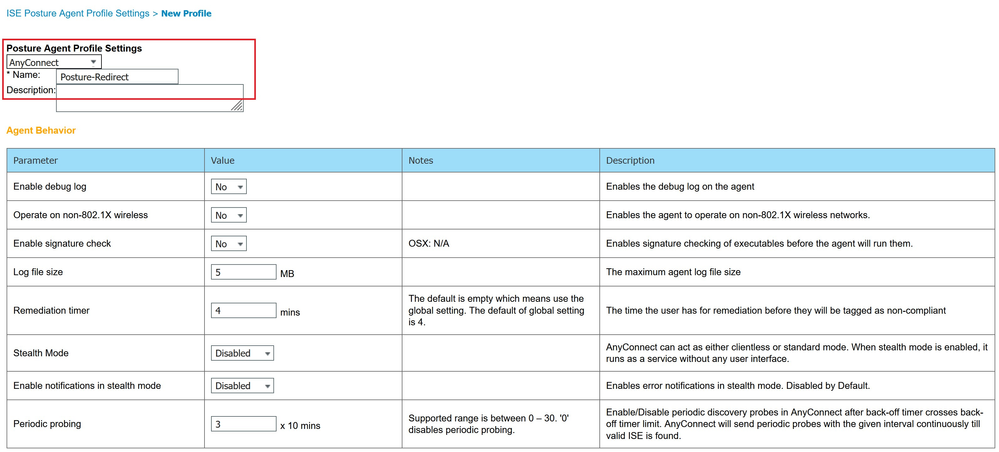
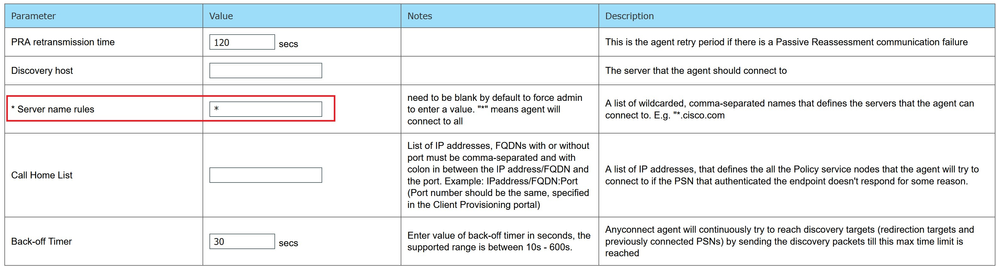
Step 4: Configure AnyConnect ISE posture profile
ISE posture profile is an essential part of client provisioning configuration on ISE. Basically, we only need to define a profile name and specify the server name rules.
Navigate to (1)Work Centers → (2)Posture → (3)Client Provisioning → (4) Resources.
Click Add and select “NAC Agent or AnyConnect Posture Profile”.
- Choose agent type – AnyConnect
- Define a profile name – POSTURE-REDIRECT
- Specify Server name rules – put ‘*’ here. Server name rules instructs the AnyConnect ISE posture module to which PSNs it is allowed to connect. Validation happens based on PSN name provided during the posture process from ISE to the agent.
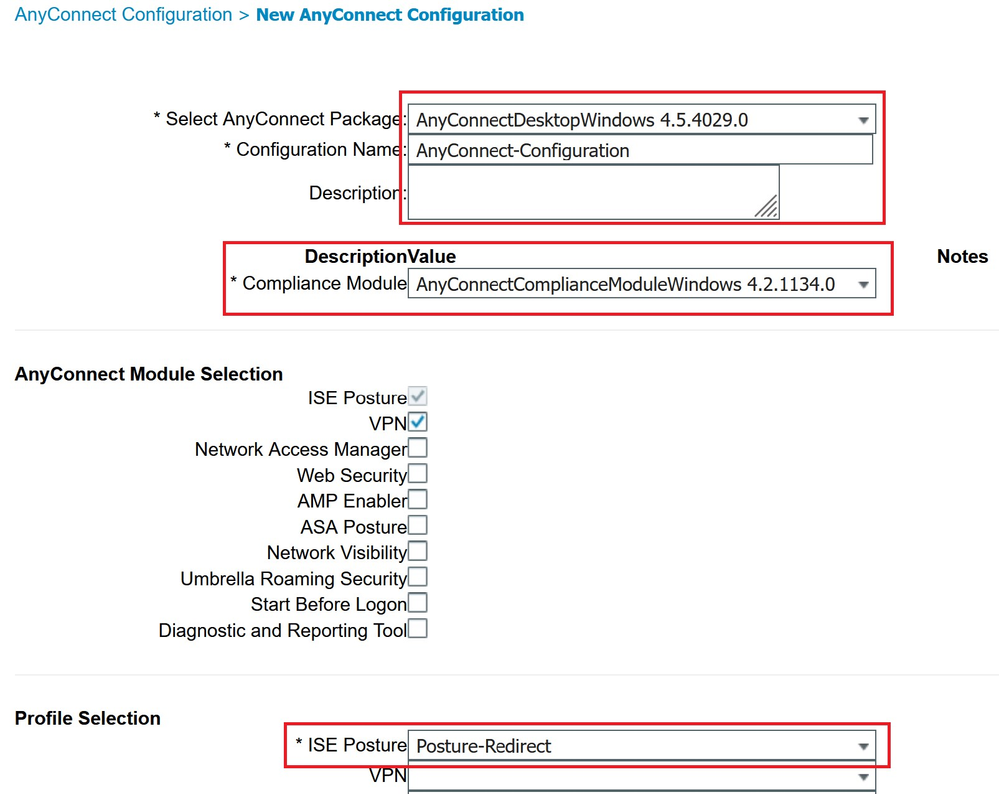
Step 5: Create AnyConnect configuration
We need to create an AnyConnect configuration which conbines together AnyConnect pkg version, compliance module version and posture profile. This is the place where an administrator can define which AnyConnect modules should be provisioned and with which profiles.
On the same page Click Add and select – AnyConnect Configuration as shown below.
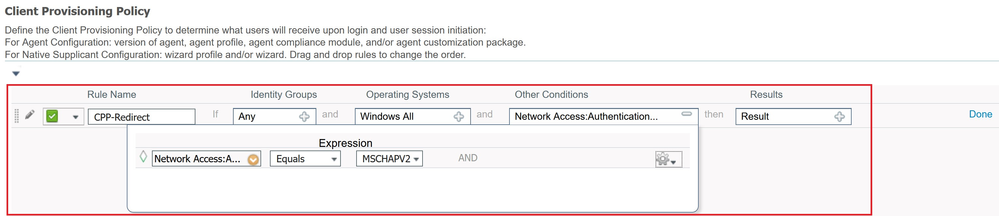
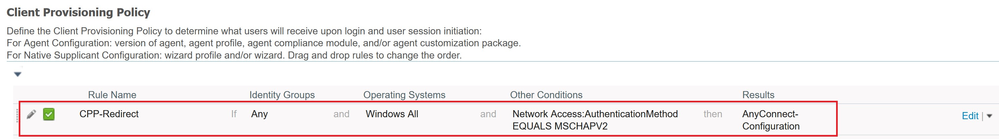
Step 6: Create Client Provisioning Policy
The Client Provisioning policy in ISE specifies which Resources (BYOD/Posture) should be provisioned to the end-user.
Navigate to (1)Work Centers → (2)Posture → (3)Client Provisioning → (4) Client Provisioning Policy.
The scenario has the following requirements for provisioning of the AC configuration which you've just created for the redirect-based flow:
- User should belong to Internal Identity Group Employee (You can AD Group if you have Active Directory integrated)
- VPN authentication should be performed over – MS-CHAPv2
Step 7: Create Authorization Profiles
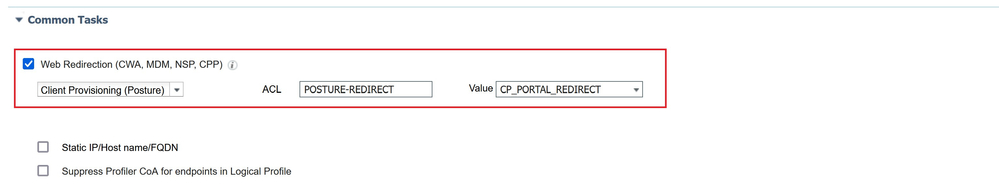
The first Authorization Profile must be applied to VPN User during the posture assessment, the goal is to provide limited access to internal ressources and redirection to the Client Provisioning Portal.
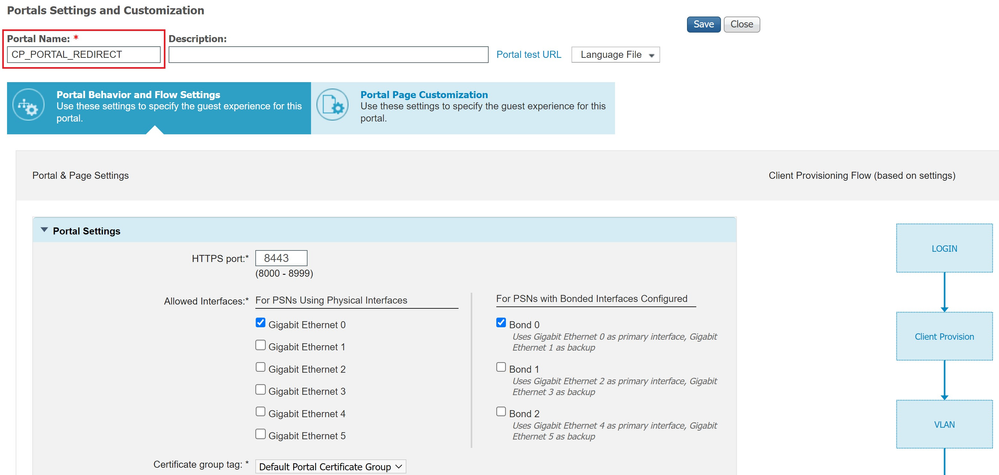
Navigate to (1)Work Centers → (2)Posture → (3)Client Provisioning → (4) Client Provisioning Portal. Create a Client Provisioning Portal named CP_PORTAL_REDIRECT.
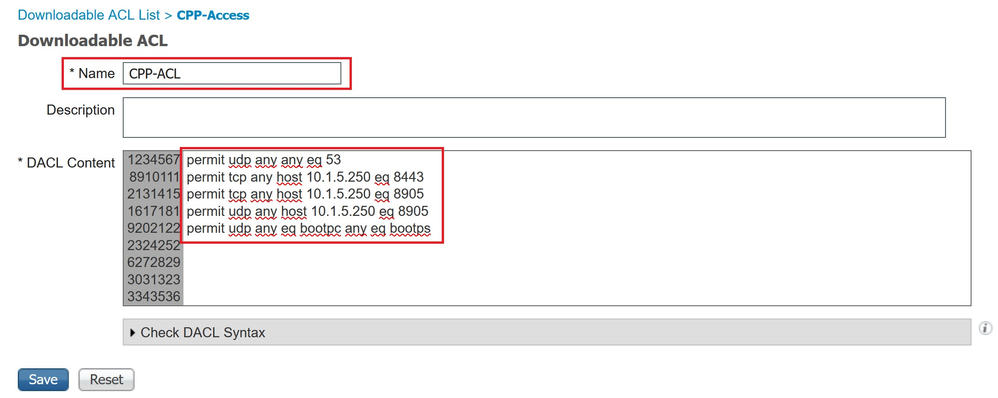
Navigate to (1)Work Centers → (2)Posture → (3)Policy Elements → (4)Downloadable ACLs to create a Downloadable ACL with some restriction (for example allow DNS, DHCP and SWISS protocol UDP and TCP Ports.
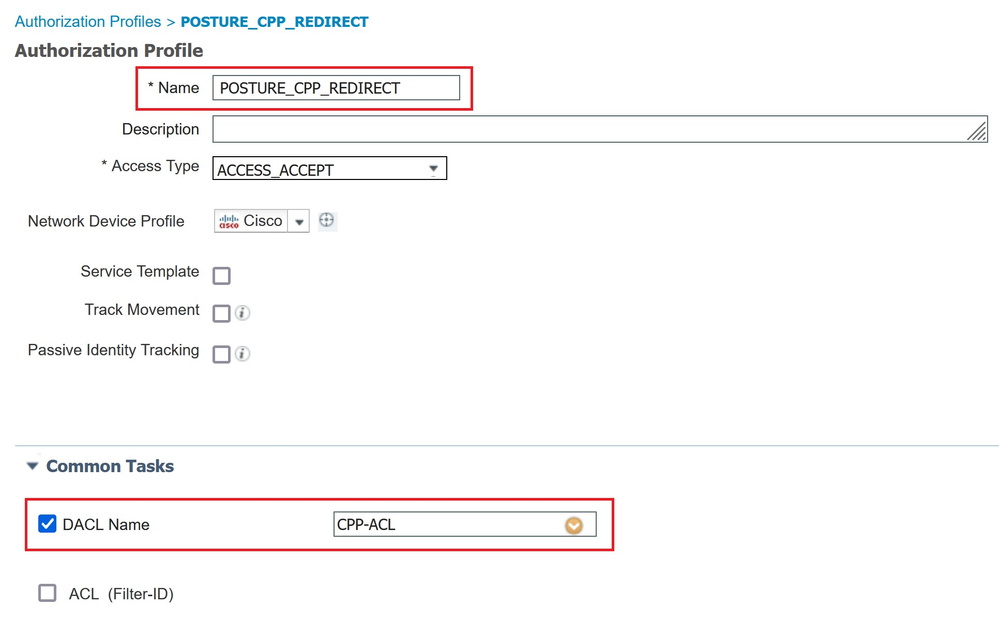
Navigate to (1)Work Centers → (2)Posture → (3)Policy Elements → (4)Authorization Profiles to create an Authorization Profile that must be applied during posture assessment. Associate the previous dACL.
In the Common Task, select Client Provisioning (Posture) for web redirection, then the Redirection ACL (the name must match the name configured on the ASA), finally select the Client Provisioning Portal created previously CP_PORTAL_REDIRECT.
Once the end user's PC is compliant, we need to change the authorization to provice full access to the internal ressources. This is the second authorization profile.
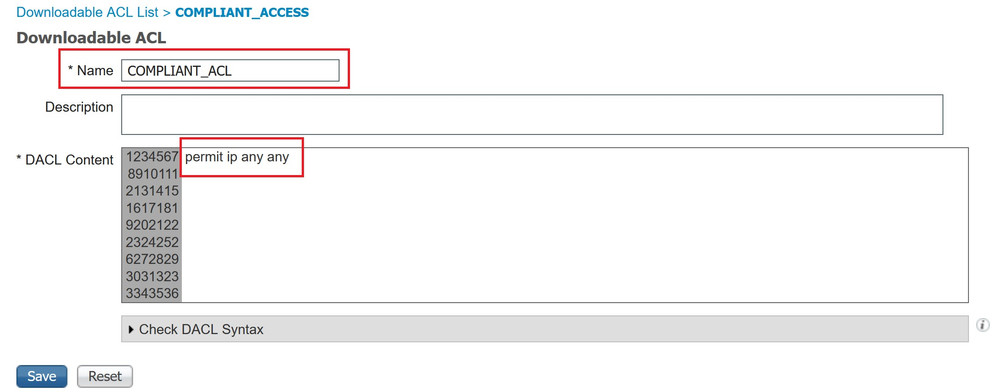
Navigate to (1)Work Centers → (2)Posture → (3)Policy Elements → (4)Downloadable ACLs to create a Downloadable ACL with permit ip any any.
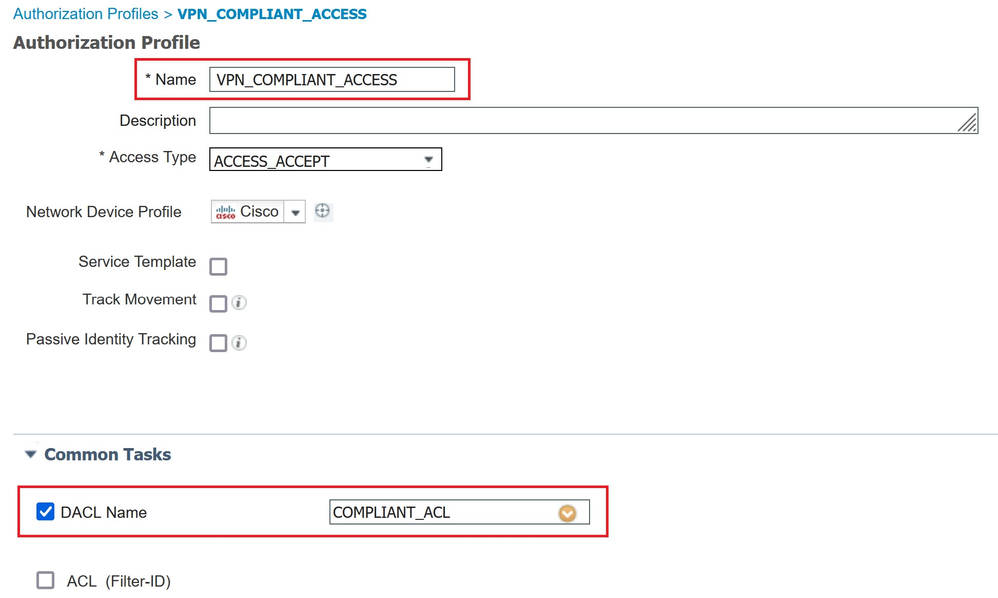
Navigate to (1)Work Centers → (2)Posture → (3)Policy Elements → (4)Authorization Profiles to create an Authorization Profile that must be applied after posture assessment. Associate the previous dACL.
Finally we have two Authorization Profiles.
The Authorization Profile POSTURE_CPP_REDIRECT for pre-assesssment.
The Authorization Profile VPN-COMPLIANTE-ACCESS for post-assesssment.
Step 8: Create two Authorization Policies
In this step, we need to associate the Authorization Profiles created in step 7 to two Authorization Policies.
Navigate to (1)Work Centers → (2)Posture → (3)Policy Sets. Edit the Policy Set of VPN Access.
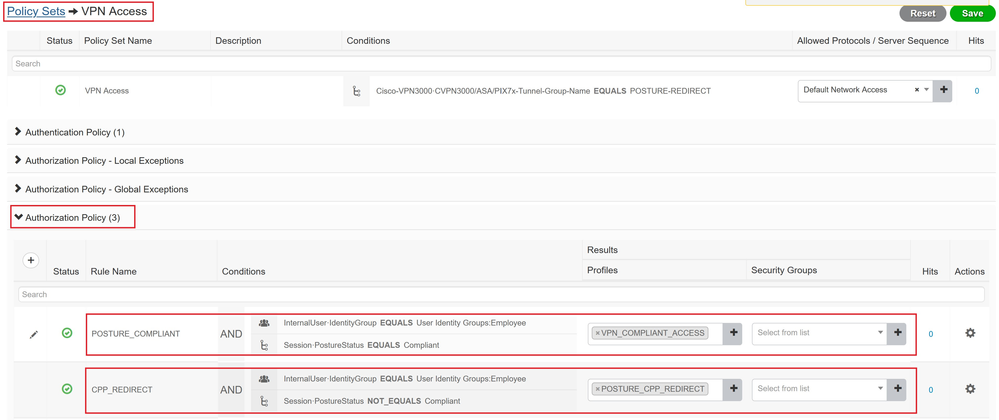
Under this this Policy Set, create two Authoriztion Policies.
Authorization Policy for compliant PCs.
- Name: POSTURE_COMPLIANT
- Conditions: InternalUser:IdentityGroup EQUALS User Identity Groups:Employee AND Session:PostureStatus EQUALS Compliant
- Profiles: VPN_COMPLIANT_ACCESS
Authorization Policy for redirection.
- Name: CPP_REDIRECT
- Conditions: InternalUser:IdentityGroup EQUALS User Identity Groups:Employee AND Session:PostureStatus NOT_EQUALS Compliant
- Profiles: POSTURE_CPP_REDIRECT
Step 9: Test Posture
Let’s test from the remote user Employee PC.
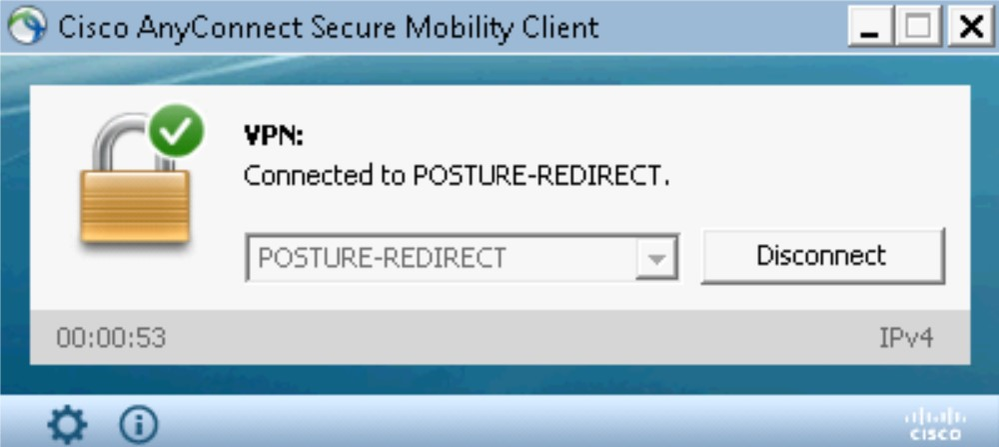
Access the VPN AnyConnect.
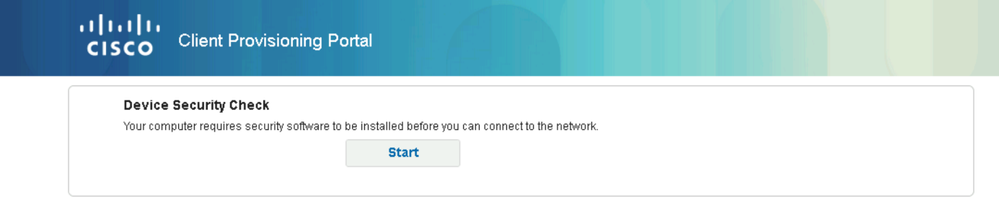
Open a web browser and type any URL.
The ISE redirects the http request to the Client Provisioning Portal. Click the Start Button.
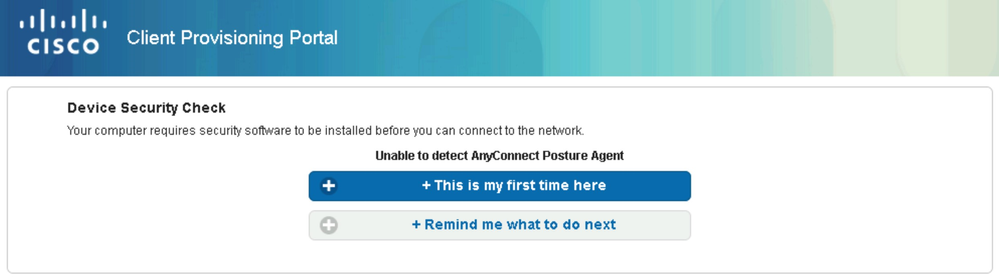
Click the This is my first time here button.
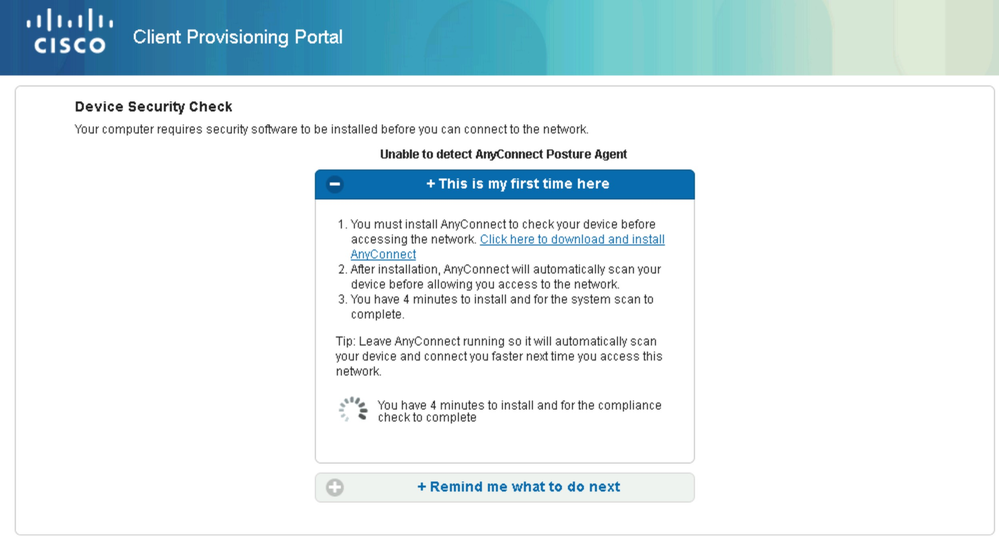
The posture module is not provisioned yet on the remote PC. The purpose of the Client Provisioning Portal is to allow end users to download the AnyConnect Posture Module. Click on Click here to download and install AnyConnect button.
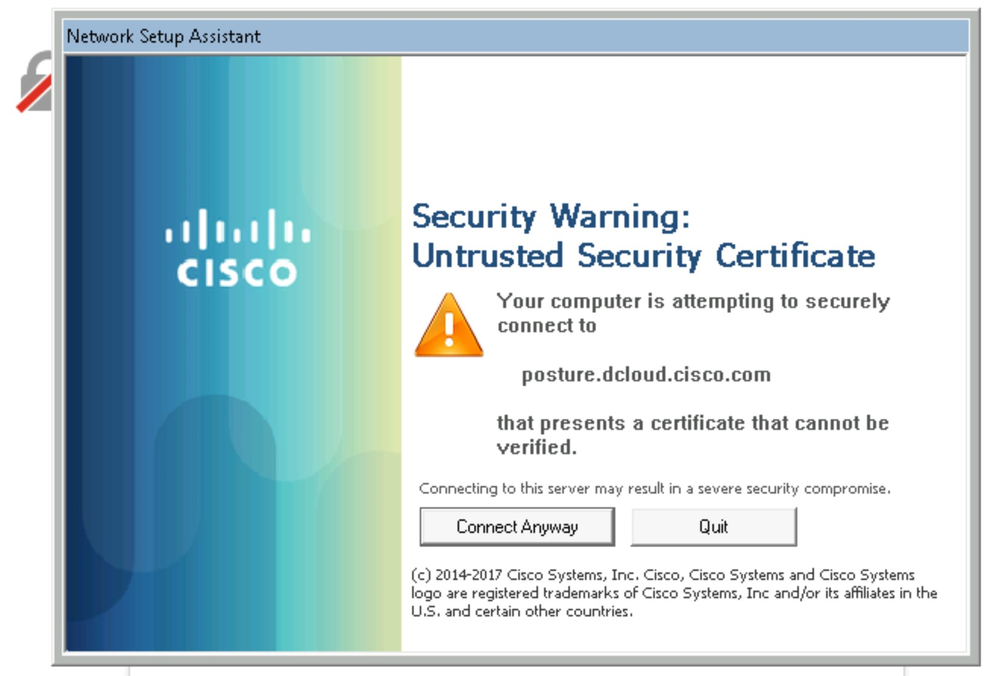
The Network Setup Assistant is launched to download the posture module.
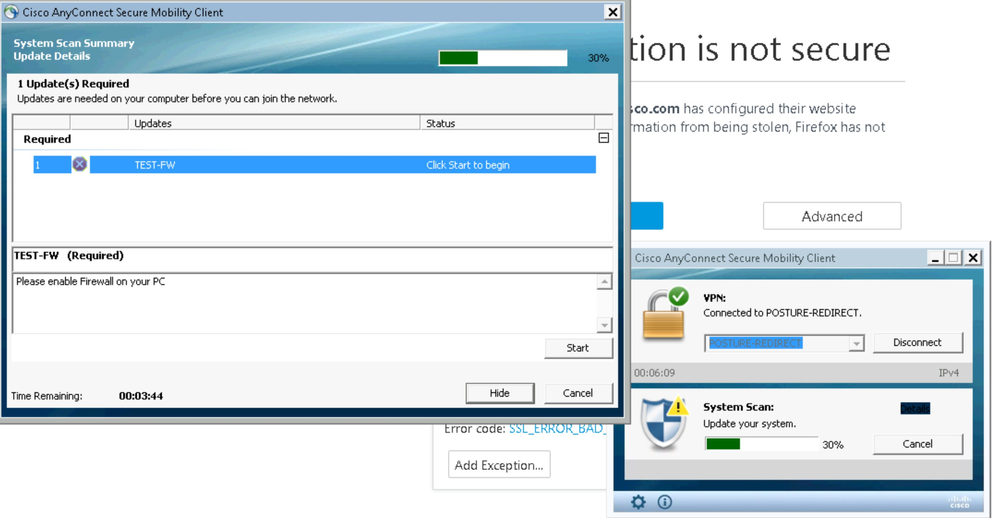
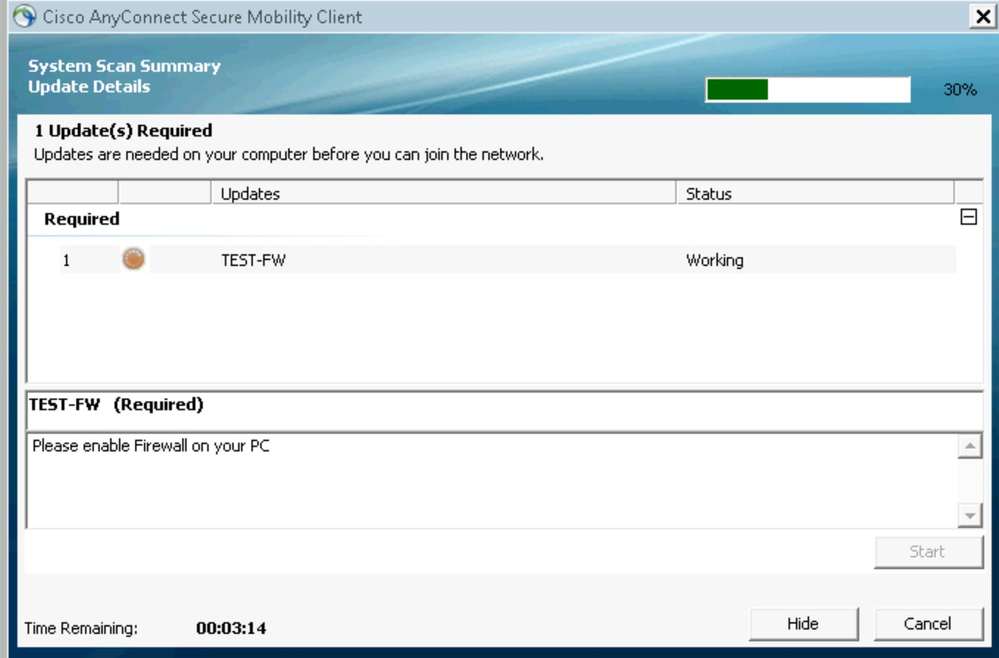
AnyConnect Posture module and compliance module will start the download and installation process. The scan starts as shown below.
A warning indicates that the Firewall on the PC is not enabled.
On the PC, enable the Firewall Windows.
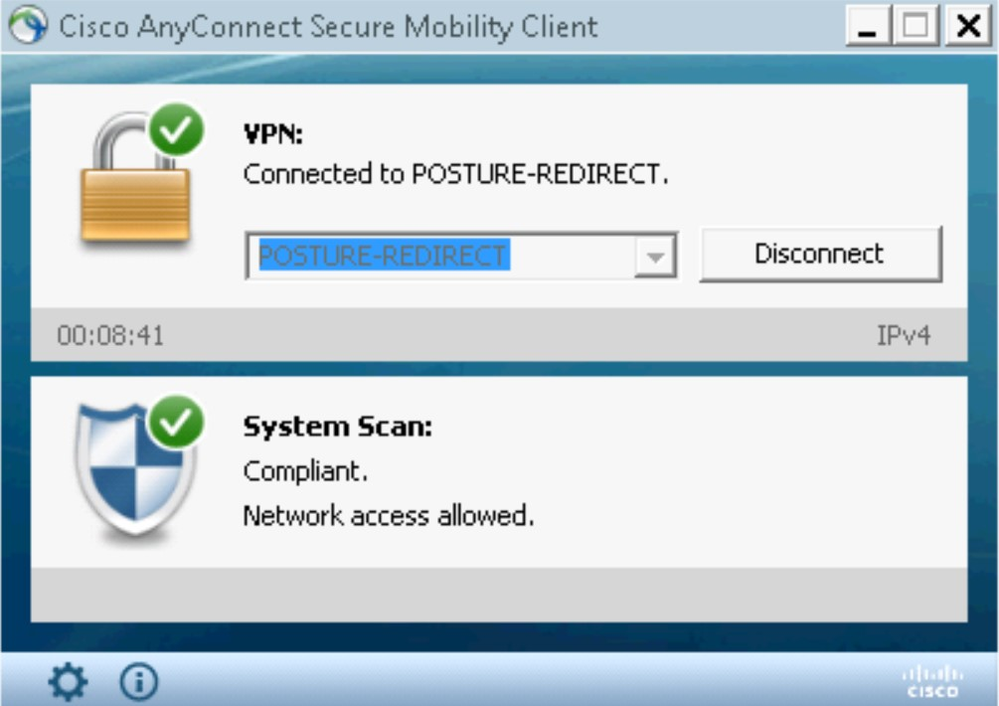
The user will gain access to the network with a Compliant status.
-
AAA
-
Access Control Server (ACS)
-
AMP for Endpoints
-
AnyConnect
-
Buying Recommendation
-
Cisco Adaptive Security Appliance (ASA)
-
Cisco Defense Orchestrator (CDO)
-
Cisco SecureX
-
Cisco Threat Response
-
Cisco Vulnerability Management
-
Cloud Security
-
Cognitive Intelligence
-
DUO
-
Email Security
-
Event Analysis
-
Identity Services Engine (ISE)
-
Integrated Security Architecture
-
IPS and IDS
-
NGFW Firewalls
-
NGIPS
-
Orbital Advanced Search
-
Other Security Topics
-
Passive Identity
-
Physical Security
-
Policy and Access
-
Security Management
-
Sourcefire
-
Stealthwatch
-
TrustSec
-
Umbrella
-
VPN
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: