Pre-filtering is the first phase of access control, before the system performs more resource-intensive evaluation. It is used to bypass or block traffic that does not require further inspection by access control policy. This process occurs without adding significant overhead to the device.
Pre-Filtering is the optional first step of packet flow on Firepower Threat Defense. A pre-filter policy contains rules that match simple values, like IP’s and ports, L3 and L4 informations. There is no deep packet inspection in a pre-filter policy. We can compare the Prefilter rules to ACL on ASA.
One of the reasons to use this is to quickly allow or deny traffic, without deeper inspection. For example, we don’t allow FTP traffic on your network. You could create a pre-filter policy that blocks TCP port 22 or 21. This means the traffic is not passed to the SNORT engine or check a malware policy. It blocks the traffic without wasting resources on FTD.
We want also to allow SSH traffic for administrator without further inspection. This traffic can be put on the Fast-Path. The fast-path allows traffic while bypassing deeper inspection. You could add this to the pre-filter policy with an action of fast-path, saving resources.
Pre-filtering is only supported on Firepower Threat Defense. ASA with FirePOWER Services does not support pre-filter policies, instead we use ACL to bypass the snort engine.
The Action can be set to:
- Analyze: This will pass traffic to the ACP for deep analysis
- Block: Drops traffic that matches the rule
- Fastpath: Adds traffic to the fast path. This traffic bypasses any extra inspections
Policies are a series of rules, as shown below. There are two types of rule available:
- Prefilter: This is a normal ACL style rule, used to block or fastpath traffic. Traffic can also be passed to the ACP for deep inspection
- Tunnel: These rules block, fast-path, or rezone a plaintext tunnel
Each policy has a default action. The default action only applies to tunnel traffic. All other unmatched traffic is sent to the ACP for deep analysis.
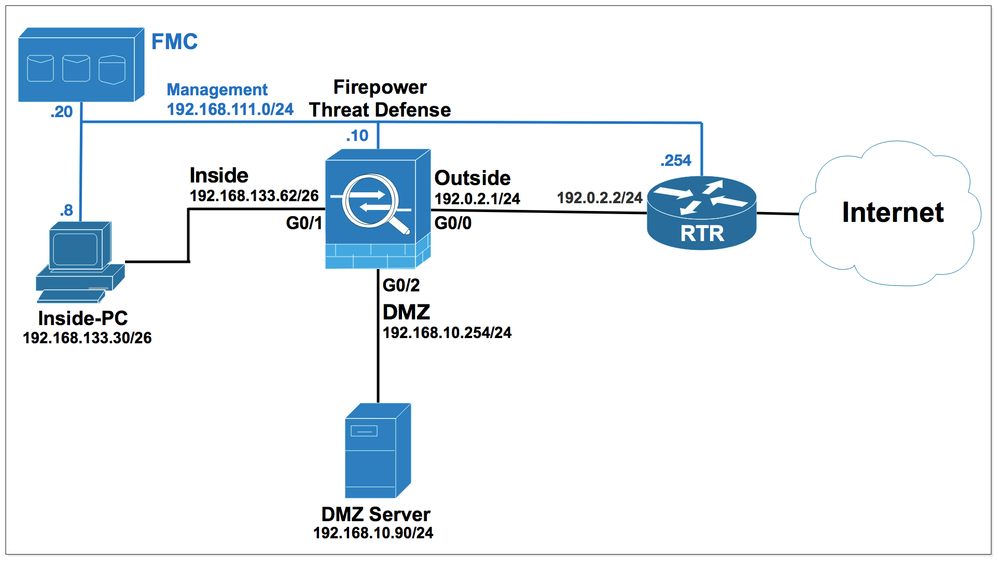
Before testing the prefilter feature, from the Inside PC, ftp to the DMZ Server 192.168.10.90, the FTD access should be successful.
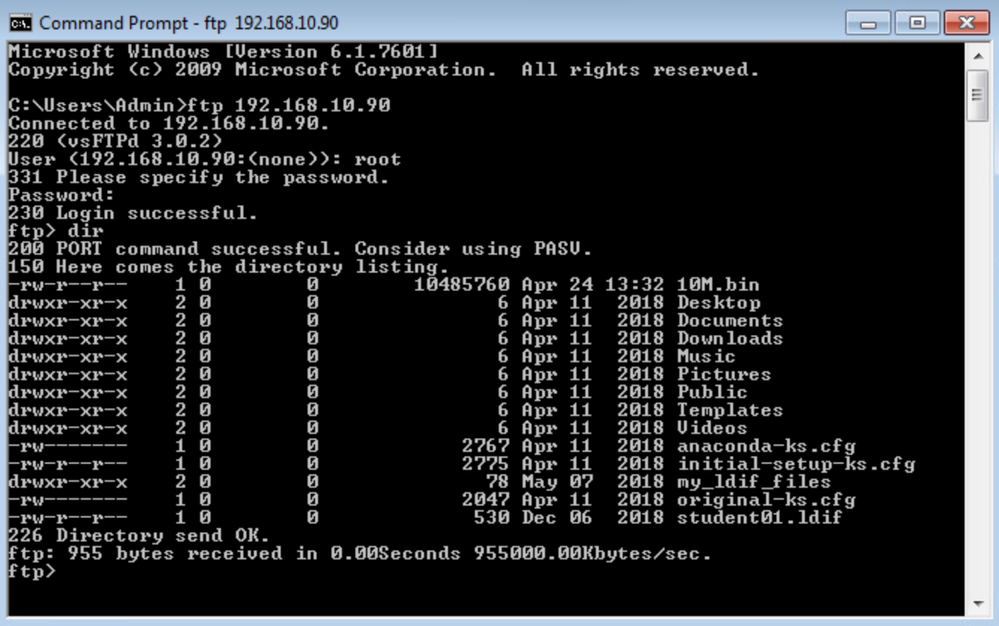
Navigate to Policies > Access Control > Prefilter.
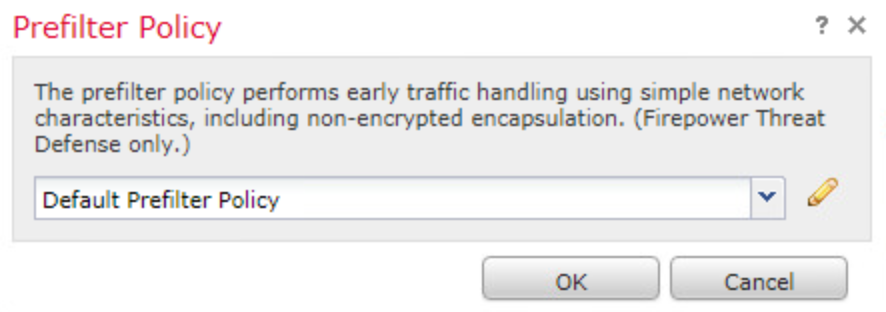
Firepower includes a default policy called Default Prefilter Policy. This policy passes all traffic through to ACP for deep inspection. Firepower uses this policy by default when you create a new ACP.
The default policy can only have limited changes made. You can change the default action and the logging settings, but you cannot add new rules. The best practice is not to change the default policy at all, instead create a custom prefilter policy.
Create a custom policy by clicking New Policy.
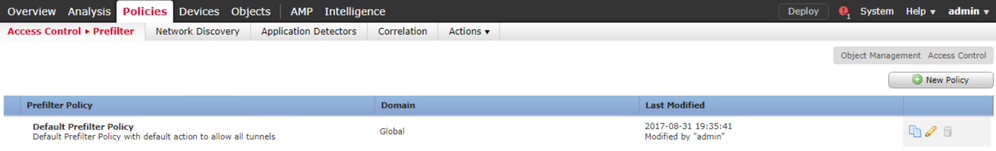
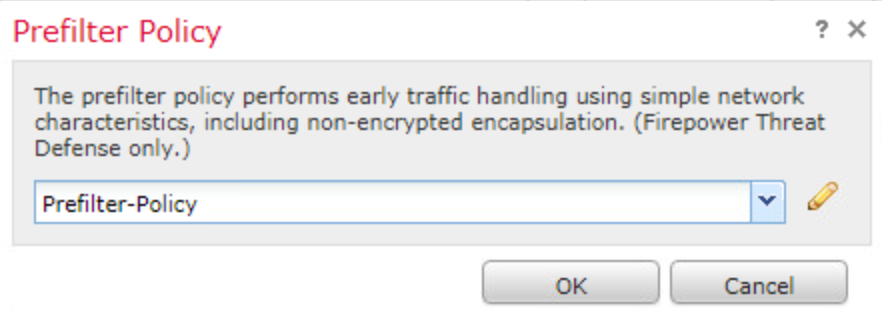
Enter the name Prefilter-Policy and click Save.
Click Add Prefilter Rule.
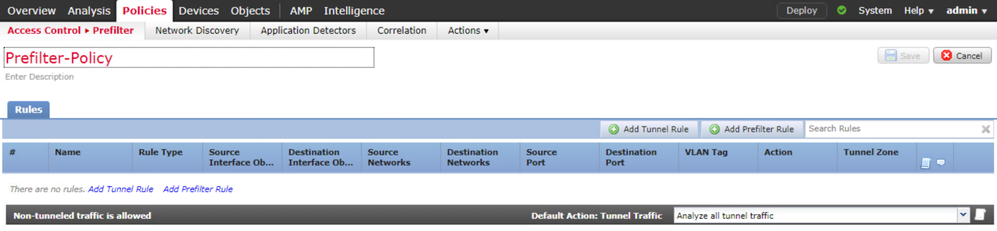
In the Name field enter the FTP-Rule, in the Action field select the Block action.
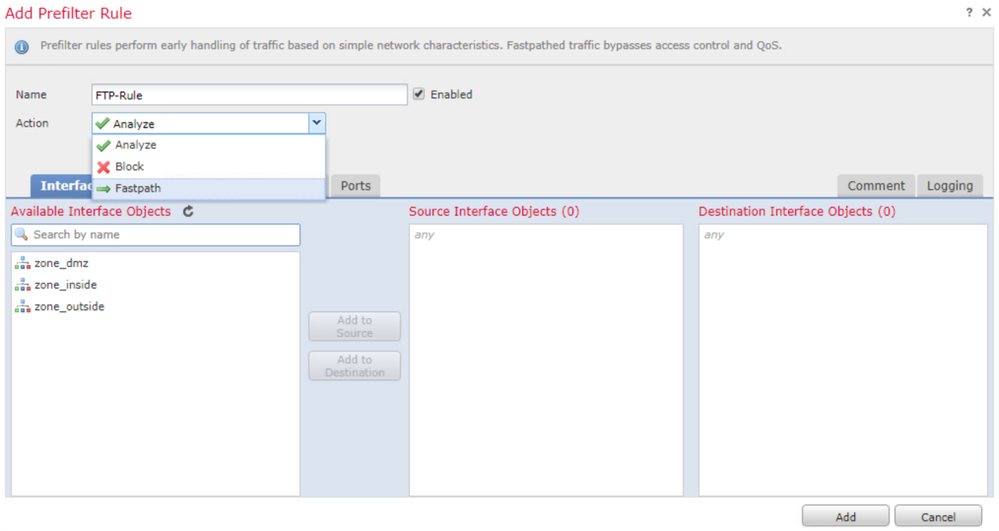
From the Interface Objects tab, under the Available Interface Objects, select the zone_inside and click Add to Source. For the Destination Interface Objects, select the zone_dmz and click Add to Destination.
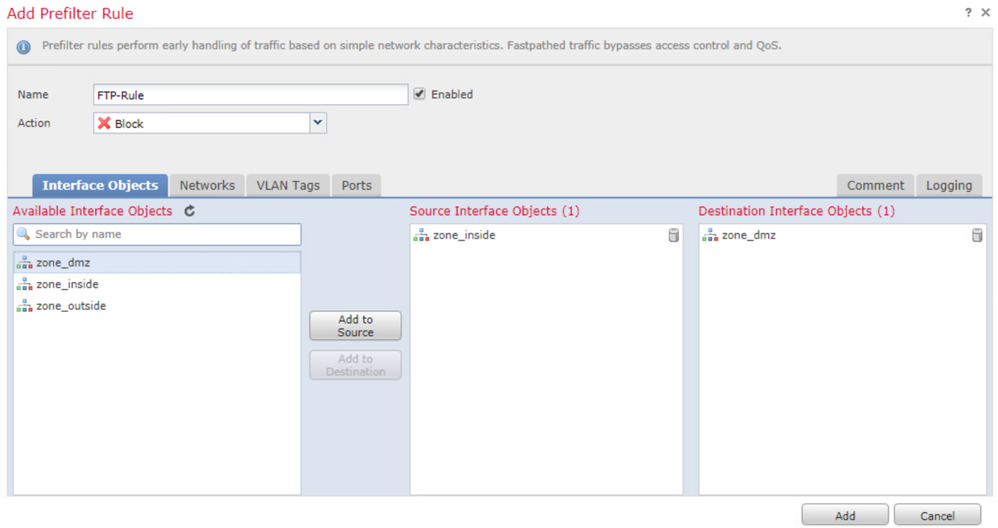
In the Logging tab, check the Log at Beginning of Connection check boxes and click Save.
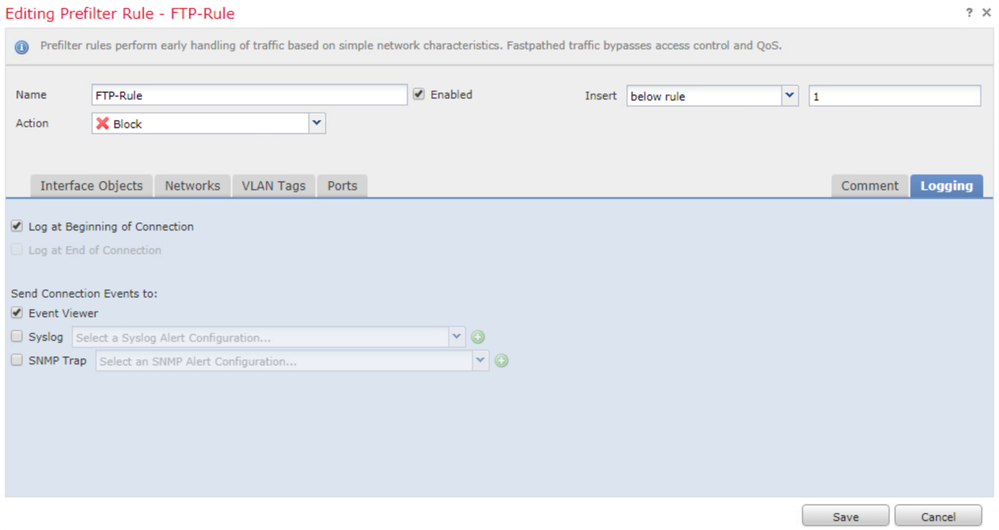
Click Save.
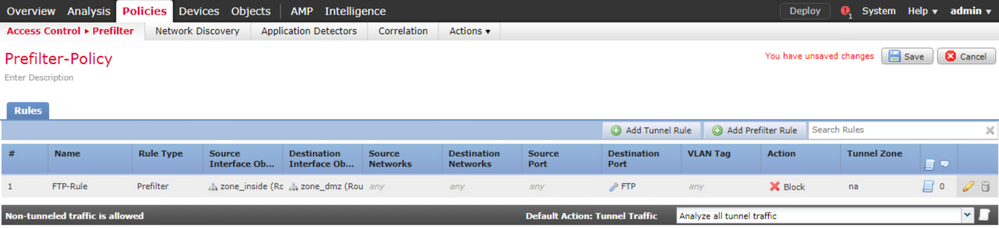
Navigate to Policies > Access Control > Access Control Policy.
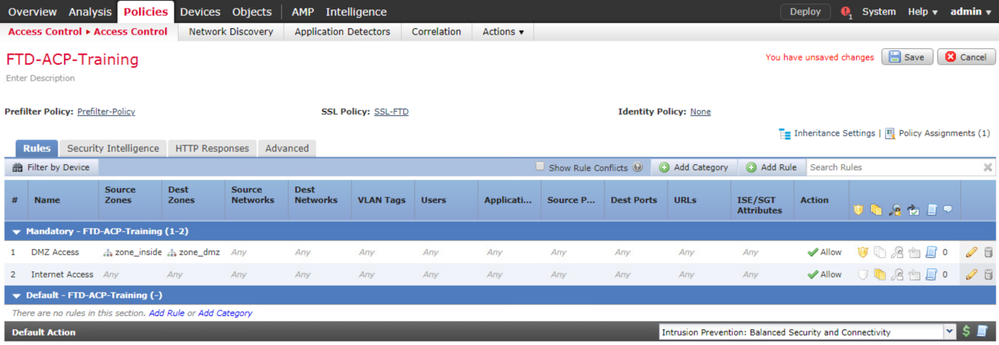
Edit the Access Control Policy FTD-ACP-Training.
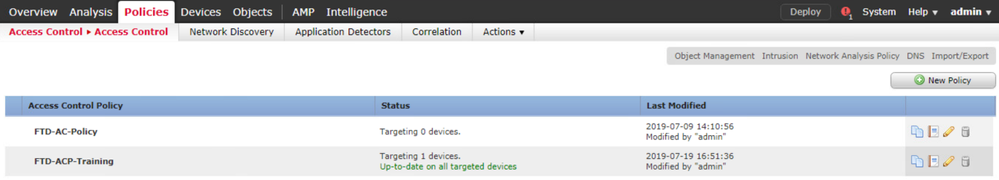
Click the Default Prefilter Policy.

You should see the Prefilter Policy windows appears, select the Prefilter Policy created previously and apply it to the ACP. Click OK.
Click the Save button to save the changes of the ACP. Then deploy the ACP to the Managed Device.
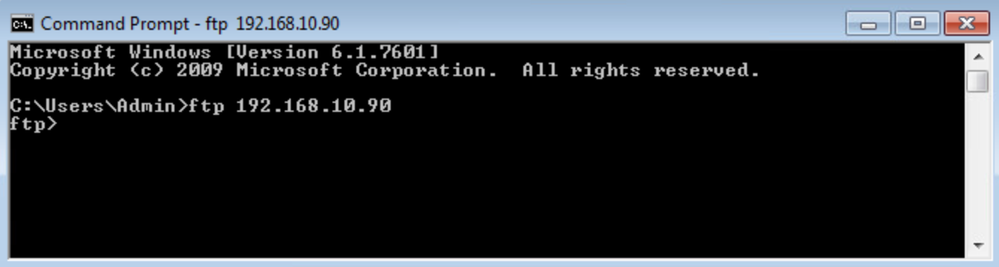
From the Inside PC, ftp to the DMZ Server 192.168.10.90.
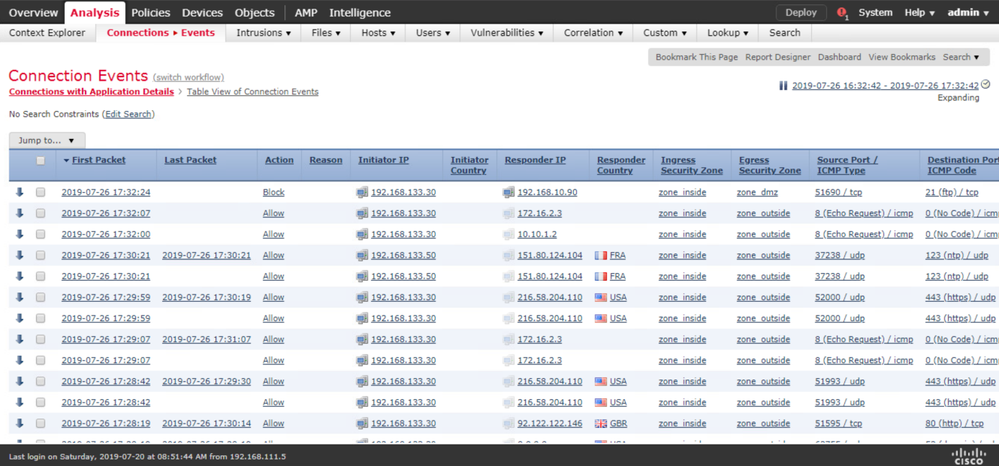
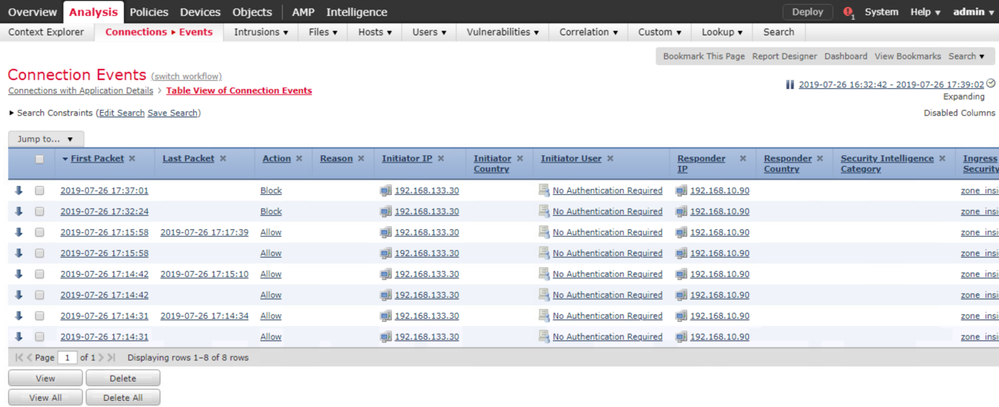
From the FMC, navigate to the Analysis > Connections > Events page.
Click Table View of Connection Events. You should see the IP address 192.168.133.30 as the Initiator IP, the IP address 192.168.10.90 ad the Responder IP, the Action of Block, the destination Port 21 (21) / TCP.
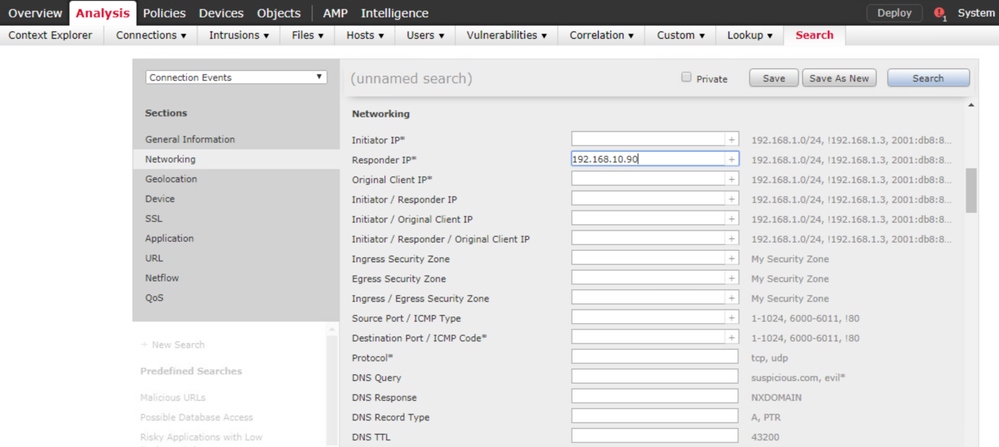
Optionally you can filter the logs to display only the events that include the Responder IP 192.168.10.90 by clicking the Edit Search.
You should see only the events related to the Responder IP 192.168.10.90.
In the Tunnel/Prefilter Rules, you should see the FTP-Rule applied to the FTP traffic.

