- Cisco Community
- Technology and Support
- Networking
- Switching
- Hi dougken444,
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2017 08:57 AM - edited 03-08-2019 10:39 AM
Dear networking experts,
I have an ASA 5506-X and I use ASDM to manage the ASA. My end goal is to have a user connected to my Guest WIFI network access a host on my internal network. The job of the host is to authenticate the guest users and allow them to access the internet once the guest accepts our TOS.
Background Info:
I have multiple interfaces on the ASA, but the main focus is on 3 of them.
Interface 1/2 - Inside security level 100
Interface 1/2.30 - GuestWifi (vlan30) security level 40
Intterface 1/3 - COMCAST (outside network) security level 0
GuestWIFI vlan uses a different subnet than the inside interface and uses the ASA as a DHCP server to issue IP address to clients. Right now, everything works, the users are able to connect to the guest wifi and obtain an IP address and surf the web. However, I want the guest users to accept a TOS before accessing the internet. The TOS is a web application installed on a server that is connected to the inside network. By default, in the guest interface, there is an Implicit rule created that will allow traffic from any source to any destination with a less secure network, see the image below. With this rule in place internet connectivity works, but the host is not accessible via the Guest Wifi. When I create an ACL to allow traffic destined for port 8843, it overrides the Implicit rule, and therefore the internet connectivity stops working. How do I keep the internet connectivity as wells allow clients to access the host to authenticate and accept the TOS?
The NAT Rules are below:
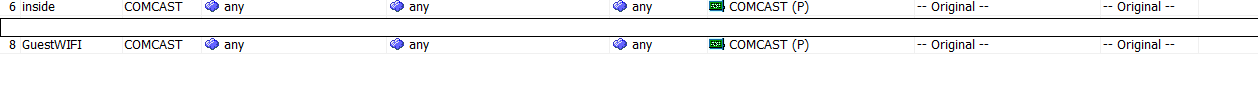
The ACL:

Solved! Go to Solution.
- Labels:
-
Other Switching
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 11:43 AM
Hey,
Following config is missing.
access-group GuestWIFI_access_in in interface GuestWIFI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2017 02:31 PM
Hi dougken444,
You need to add two Access-list rule at GuestWiFi
one is to allow access from any to host at port 8843
second is to allow access from any to any less secure networks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 08:18 AM
Hi,
Thank you so much for your response. This might be a noob question, but every time I add an access-list it overrides the access-list that allows traffic from any to any less secure network. The questions what is the command or GUI element to add that access-list back?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 08:35 AM
Hi dougken444,
Can you provide me the subnet information you are using for Inside and GuestWiFi. Inside host to whom you want to provide access to WiFi hosts.
Also the CLI output of "show runn access-group".
So that i will help you with full CLI configuration.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 09:30 AM
Hi,
The subnet for the inside network is 172.xx.xx.x/23
The subnet for the Guest WIFI network is 192.168.18.0/24
The CLI output is below:
Result of the command: "show
access-group outside_access_in in interface outside
access-group GuestWIFI_access_in in interface GuestWIFI
access-group COMCAST_access_in in interface COMCAST
You can ignore the outside interface for now.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 09:44 AM
Try the following CLI configuration:-
object-group network INSIDE_SUBNET
network-object 172.xx.xx.xx 255.255.255.254
!
object-group network TOS_HOST
network-object HOST 172.xx.xx.xx
!
object-group network GuestWiFi_SUBNET
network-object 192.168.18.0 255.255.255.0
!
access-list extended GuestWIFI_access_in permit tcp object-group GuestWiFi_SUBNET object-group TOS_HOST eq 8843
access-list extended GuestWIFI_access_in deny ip object-group GuestWiFi_SUBNET object-group INSIDE_SUBNET
access-list extended GuestWIFI_access_in deny ip object-group GuestWiFi_SUBNET any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 11:24 AM
I get an error when I run the commands below, any idea?
access-list extended GuestWIFI_access_in permit tcp object-group GuestWiFi_SUBNET object-group TOS_HOST eq 8843
access-list extended GuestWIFI_access_in deny ip object-group GuestWiFi_SUBNET object-group INSIDE_SUBNET
access-list extended GuestWIFI_access_in deny ip object-group GuestWiFi_SUBNET any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 11:40 AM
Ooops Sorry,
It should be the following
access-list GuestWIFI_access_in extended permit tcp object-group GuestWiFi_SUBNET object-group TOS_HOST eq 8843
access-list GuestWIFI_access_in extended deny ip object-group GuestWiFi_SUBNET object-group INSIDE_SUBNET
access-list GuestWIFI_access_in extended deny ip object-group GuestWiFi_SUBNET any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 11:54 AM
Hi,
Thank you so much for the fast reply. I added the 3 access rules. The computer when connected to the guest WIFI network still cannot access the TOS host. As soon as the computer connects to the guest wifi, it opens the web browser and redirects to 172.xx.xx.xx:8843/guest/... and then I get "The Page cannot be displayed"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 12:06 PM
Is there any access list at Inside interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 12:13 PM
No, except the any to any less secure networks implicit rule. Also, there is a global implicit rule that denies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 12:19 PM
Add the following config and check that are you able to ping TOS host from wifi network.
access-list GuestWIFI_access_in line 1 extended permit icmp object-group GuestWiFi_SUBNET object-group TOS_HOST
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 01:03 PM
After adding that, I lost internet connectivity on the Guest Network. Before, I was able to ping the TOS Host by enabling ICMP via the GUI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2017 01:28 PM
Try to allow all traffic to TOS from GuestWiFi instead of tcp port 8843. Following is the cofig
no access-list GuestWIFI_access_in extended permit tcp object-group GuestWiFi_SUBNET object-group TOS_HOST eq 8843
no access-list GuestWIFI_access_in extended deny ip object-group GuestWiFi_SUBNET object-group INSIDE_SUBNET
no access-list GuestWIFI_access_in extended deny ip object-group GuestWiFi_SUBNET any
access-list GuestWIFI_access_in extended permit ip object-group GuestWiFi_SUBNET object-group TOS_HOST
access-list GuestWIFI_access_in extended deny ip object-group GuestWiFi_SUBNET object-group INSIDE_SUBNET
access-list GuestWIFI_access_in extended deny ip object-group GuestWiFi_SUBNET any
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-23-2017 11:16 AM
Hi,
I added the ACLs below, I still can't access the TOS_Host and I can't ping it either.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide