- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: windows radius and catalyst c9800-l dynamic vlan
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2022 01:07 AM
Hi there!
Please, help.
I have cisco wlc 5520 + windows radius nps with dynamic vlans assigment and it works fine.
I bought cisco catalyst c9800-l and configure it by cisco guides with is using my working windows radius nps to got dynamic vlan assigment on my new wlc, however it is not work - each time my test user got random vlan number...
AAA override for wlan enabled. Also I tried 3 different firmware from 17.3.5b to 17.9.1...
Radius ip 10.10.6.2/23
wlc c9800 ip 10.10.4.2/23 (vlan 1114)
AP ip 10.10.4.28/23 (vlan 1114)
correct users vlan id 4
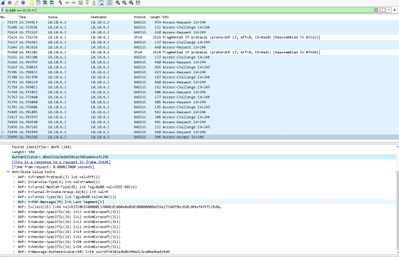
Here is dump from my radius server and debug from my new c9800-l at the same time:
only one access-accept in the dump - authentificator number c2 95 (string 5006)
2022/10/31 10:25:23.038501048 {wncd_x_R0-0}{1}: [aaa] [22860]: (debug): Valid server internal check: server MY_s02-dc03 with handle f5000005 : is valid
2022/10/31 10:25:23.038508777 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: authenticator 0b ec 51 6a 7e de 93 8c - ec 9d 5a e4 4c af c2 95
2022/10/31 10:25:23.038515475 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Framed-Protocol [7] 6 PPP [1]
2022/10/31 10:25:23.038520920 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Service-Type [6] 6 Framed [2]
2022/10/31 10:25:23.038524582 {wncd_x_R0-0}{1}: [radius] [22860]: (info): 00:
2022/10/31 10:25:23.038526930 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Tunnel-Medium-Type [65] 6 ALL_802 [6]
2022/10/31 10:25:23.038531828 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Tunnel-Private-Group-Id[81] 3 "4"
2022/10/31 10:25:23.038535653 {wncd_x_R0-0}{1}: [radius] [22860]: (info): 00:
2022/10/31 10:25:23.038537817 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Tunnel-Type [64] 6 VLAN [13]
2022/10/31 10:25:23.038541837 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: EAP-Message [79] 6 ...
2022/10/31 10:25:23.038548917 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: EAP-Message [79] 6
RADIUS: 03 0c 00 04
2022/10/31 10:25:23.038553292 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Class [25] 46 ...
2022/10/31 10:25:23.038599449 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: Class [25] 46
RADIUS: b3 72 0b 53 00 00 01 37 00 01 02 00 0a 0a 06 02 00 00 00 00 ed 55 e2 77 a0 79 bc d5 01 d8 8a f4 75 f1 28 d0 00 00 00 00 01 66 55 45 [ rS7Uwyu(fUE]
2022/10/31 10:25:23.038604141 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Microsoft [26] 12
2022/10/31 10:25:23.038608211 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: MS-Link-Util-Thresh[14] 6 ...
2022/10/31 10:25:23.038623496 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: MS-Link-Util-Thresh[14] 6
RADIUS: 00 00 00 32 [ 2]
2022/10/31 10:25:23.038627657 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Microsoft [26] 12
2022/10/31 10:25:23.038631649 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: MS-Link-Drop-Time-Limit[15] 6 ...
2022/10/31 10:25:23.038647034 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: MS-Link-Drop-Time-Limit[15] 6
RADIUS: 00 00 00 78 [ x]
2022/10/31 10:25:23.038661037 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Microsoft [26] 12
2022/10/31 10:25:23.038665273 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: MS-MPPE-Enc-Policy [7] 6 ...
2022/10/31 10:25:23.038671870 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: MS-MPPE-Enc-Policy [7] 6
RADIUS: 00 00 00 02
2022/10/31 10:25:23.038675906 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Microsoft [26] 12
2022/10/31 10:25:23.038679872 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: MS-MPPE-Enc-Type [8] 6 ...
2022/10/31 10:25:23.038686375 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: MS-MPPE-Enc-Type [8] 6
RADIUS: 00 00 00 0e
2022/10/31 10:25:23.038690433 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Microsoft [26] 14
2022/10/31 10:25:23.038695017 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: MS-CHAP-DOMAIN [10] 8 "MY_DOMAINO"
2022/10/31 10:25:23.038699246 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Microsoft [26] 51
2022/10/31 10:25:23.038704020 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: MS-CHAP-V2-Success [26] 45 "S=683ED09CD8CC52B4263F000E85E7373A477CF49C"
2022/10/31 10:25:23.038708164 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Microsoft [26] 58
2022/10/31 10:25:23.038712122 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: MS-MPPE-Send-Key [16] 52 *
2022/10/31 10:25:23.038716351 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: MS-MPPE-Send-Key [16] 52 *
2022/10/31 10:25:23.038720323 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Microsoft [26] 58
2022/10/31 10:25:23.038724191 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: MS-MPPE-Recv-Key [17] 52 *
2022/10/31 10:25:23.038728326 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: MS-MPPE-Recv-Key [17] 52 *
2022/10/31 10:25:23.038732576 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Message-Authenticator[80] 18 ...
2022/10/31 10:25:23.038753971 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: Message-Authenticator[80] 18
RADIUS: 6f 18 38 3a db 06 34 4e 31 3c a0 be 96 e4 14 d6 [ o8:4N1<]
debug logs, that I got during connecting my user to wlan:
authenticator id started from string 5006, and there is correct vlan (4) - Tunnel-Private-Group-Id[81] 3 "4", but in previous stings I saw strange symbols like qnJ'cC_N4bA<? (sting 4966) and incorrect vlan vlan-id=1360 in string 4979...
2022/10/31 10:25:23.037075199 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Service-Type [6] 6 Framed [2]
2022/10/31 10:25:23.037079469 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Cisco [26] 27
2022/10/31 10:25:23.037084764 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Cisco AVpair [1] 21 "service-type=Framed"
2022/10/31 10:25:23.037090420 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Framed-MTU [12] 6 1485
2022/10/31 10:25:23.037094606 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: EAP-Message [79] 108 ...
2022/10/31 10:25:23.037171621 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: EAP-Message [79] 108
RADIUS: 02 0c 00 6a 19 00 17 03 03 00 5f 00 00 00 00 00 00 00 05 90 3e e0 8e 3a 45 76 ff 2d ee 95 ab d6 db 72 da 35 a3 e1 c5 1b 05 56 95 aa 97 b5 2a 84 cc 4b eb e9 46 88 bd 87 83 a8 3d 65 e1 e5 85 a8 99 d7 53 [j_>:Ev-r5V*KF=eS0Œalü]
2022/10/31 10:25:23.037202047 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: a4 1a f5 71 c8 e3 fc cf 6e c0 e4 4a 27 63 43 80 5f 04 13 bf 4e 9a d4 34 62 41 a2 a7 c3 96 3c af 9d 89 9b 3f 9d 89 99 [ qnJ'cC_N4bA<?]
2022/10/31 10:25:23.037206614 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Message-Authenticator[80] 18 ...
2022/10/31 10:25:23.037228335 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: Message-Authenticator[80] 18
RADIUS: 05 e1 53 16 5d b7 b6 6f 78 a6 50 eb 84 6b 76 80 [ S]oxPkv]
2022/10/31 10:25:23.037232782 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: EAP-Key-Name [102] 2 *
2022/10/31 10:25:23.037237052 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: EAP-Key-Name [102] 2 *
2022/10/31 10:25:23.037241218 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Cisco [26] 49
2022/10/31 10:25:23.037246266 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Cisco AVpair [1] 43 "audit-session-id=02040A0A000006552CEE4EBA"
2022/10/31 10:25:23.037250347 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Cisco [26] 20
2022/10/31 10:25:23.037255371 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Cisco AVpair [1] 14 "method=dot1x"
2022/10/31 10:25:23.037265138 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Cisco [26] 32
2022/10/31 10:25:23.037269934 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Cisco AVpair [1] 26 "client-iif-id=3254781334"
2022/10/31 10:25:23.037273890 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Cisco [26] 20
2022/10/31 10:25:23.037278479 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Cisco AVpair [1] 14 "vlan-id=1360"
2022/10/31 10:25:23.037284563 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: NAS-IP-Address [4] 6 10.10.4.2
2022/10/31 10:25:23.037289767 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: NAS-Port-Type [61] 6 802.11 wireless [19]
2022/10/31 10:25:23.037294816 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: NAS-Port [5] 6 111417
2022/10/31 10:25:23.037298832 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: State [24] 38 ...
2022/10/31 10:25:23.037339881 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS: State [24] 38
RADIUS: 73 b7 09 00 00 00 01 37 00 01 17 00 fe 80 00 00 00 00 00 00 ed 55 e2 77 a0 79 bc d5 00 00 00 04 ed 7d 06 78 [ s7Uwy}x]
2022/10/31 10:25:23.037343961 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Cisco [26] 36
2022/10/31 10:25:23.037348725 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Cisco AVpair [1] 30 "cisco-wlan-ssid=MY_WLAN1"
2022/10/31 10:25:23.037352698 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Cisco [26] 37
2022/10/31 10:25:23.037357450 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Cisco AVpair [1] 31 "wlan-profile-name=MY_WLAN"
2022/10/31 10:25:23.037362304 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Called-Station-Id [30] 11 "10.10.4.2"
2022/10/31 10:25:23.037367080 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Calling-Station-Id [31] 14 "ac675dfb43bb"
2022/10/31 10:25:23.037371367 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Vendor, Airespace [26] 12
2022/10/31 10:25:23.037376151 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Airespace-WLAN-ID [1] 6 1
2022/10/31 10:25:23.037380965 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: Nas-Identifier [32] 6 "WLC1"
2022/10/31 10:25:23.037385786 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: wlan-group-cipher [187] 6 " "
2022/10/31 10:25:23.037390446 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: wlan-pairwise-cipher[186] 6 " "
2022/10/31 10:25:23.037395066 {wncd_x_R0-0}{1}: [radius] [22860]: (info): RADIUS: wlan-akm-suite [188] 6 " "
2022/10/31 10:25:23.037395800 {wncd_x_R0-0}{1}: [radius] [22860]: (debug): RADIUS(00000000): Sending a IPv4 Radius Packet
2022/10/31 10:25:23.037421396 {wncd_x_R0-0}{1}: [aaa] [22860]: (debug): Valid server internal check: server MY_s02-dc03 with handle f5000005 : is valid
Full log in attach.
in radius-screen-log stange that account session identifier is - (empty). I compared this with worked wlc (5520) - there is some id...
I don't know what to try...
Solved! Go to Solution.
- Labels:
-
Catalyst Wireless Controllers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2022 04:07 AM
Hi again...
In general, there was needed authorization config
simple... but not obviously
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2022 02:24 AM
- Below , you will find the output of your attached debug when processed with : https://cway.cisco.com/wireless-debug-analyzer/ , it would also be advisable to start with a checkup of the current c9800-l configuration with the CLI command : show tech wireless , have the output analyzed by https://cway.cisco.com/
Review this document too : https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wlan-security/217043-configure-dynamic-vlan-assignment-with-c.html
--following debug analyzed with https://cway.cisco.com/wireless-debug-analyzer/ --- (seems rather normal at first glance)
TimeTaskTranslated
| 2022/10/31 10:25:22.945 | client-orch-sm | Client made a new Association to an AP/BSSID: BSSID 84f1.476f.49ad, WLAN MY_WLAN, Slot 1 AP 84f1.476f.49a0, APF01D.2DB7.6904 |
| 2022/10/31 10:25:22.946 | dot11 | Association success for client, assigned AID is: 1 |
| 2022/10/31 10:25:22.946 | client-orch-sm | Client started layer 2 authentication (either dot1X or PSK) |
| 2022/10/31 10:25:22.951 | client-auth | Entering 802.1X authentication process |
| 2022/10/31 10:25:22.951 | client-auth | Entering 802.1X authentication process |
| 2022/10/31 10:25:23.040 | client-auth | Starting EAPOL 4-Way Handshake |
| 2022/10/31 10:25:23.040 | client-keymgmt | Sent M1 for EAPOL 4-Way Handshake |
| 2022/10/31 10:25:23.042 | client-keymgmt | Received and validated M2 for EAPOL 4-Way Handshake |
| 2022/10/31 10:25:23.042 | client-keymgmt | Sent M3 for EAPOL 4-Way Handshake |
| 2022/10/31 10:25:23.044 | client-keymgmt | Received and validated M4 for EAPOL 4-Way Handshake |
| 2022/10/31 10:25:23.044 | client-keymgmt | Negotiated the following encryption mechanism: AKM:DOT1X Cipher:CCMP WPA Version: WPA2 |
| 2022/10/31 10:25:23.044 | client-orch-sm | Client passed layer 2 authentication |
| 2022/10/31 10:25:23.044 | client-orch-state | Starting Mobility Anchor discovery for client |
| 2022/10/31 10:25:23.046 | client-orch-state | Entering IP learn state |
| 2022/10/31 10:25:24.713 | client-iplearn | Client got IP: 10.10.4.25, discovered through: ARP |
| 2022/10/31 10:25:24.714 | client-orch-sm | IP Learn state completed, IP information discovered through: IPLEARN_METHOD_ARP |
| 2022/10/31 10:25:24.714 | client-orch-state | Client reached RUN state, connection completed. |
| 2022/10/31 10:25:27.002 | client-iplearn | Controller updated IP information. IP: 10.10.4.25, discovered through: DHCP |
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2022 03:25 AM
Thank you for answer.
Yes, it seems like all right, but assigned vlan and ip that device got are not correct
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2022 04:33 AM
- Have you already executed the procedure concerning WirelessAnalyzer ?
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2022 02:22 AM
wireless analyzer output:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2022 04:34 AM
- Note that all red-flagged items should be corrected,
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2022 10:14 AM
1. I recommend 17.6.4 as the best stable release at the moment.
2. If I understand correctly, you say your radius is sending the wrong VLAN id, but you think that is because it's not getting the correct session identifier from the WLC?
Check that you have all the correct settings enabled for radius. For example we use:
radius-server attribute wireless authentication callStationIdCase lower
radius-server attribute wireless authentication mac-delimiter hyphen
radius-server attribute wireless authentication call-station-id ap-name-ssid
radius-server attribute wireless 44 include-in-access-req
But your config will depend on what your radius server requires. Similarly for accounting we use:
radius-server attribute wireless accounting mac-delimiter hyphen
radius-server attribute wireless accounting username-delimiter hyphen
radius-server attribute wireless accounting username-case lower
radius-server attribute wireless accounting call-station-id ap-name-ssid
radius-server attribute wireless accounting callStationIdCase lower
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Default AP console baud rate from 17.12.x is 115200 - introduced by CSCwe88390
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2022 04:13 AM - edited 11-01-2022 04:28 AM
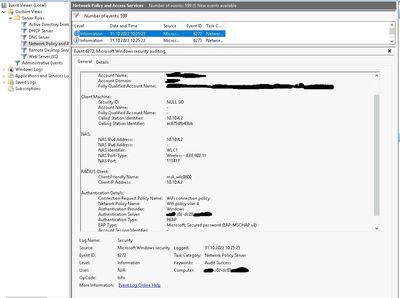
Hi, no, radius returns correct vlan - vlan 4, but controller see not only vlan 4, and vlan 1360.
Here is my config from controller:
WLC1#sho run | inc radius-server
radius-server attribute wireless accounting mac-delimiter none
radius-server attribute wireless accounting call-station-id ipaddress
radius-server attribute wireless authentication mac-delimiter none
radius-server attribute wireless authentication call-station-id ipaddress
I will try authentication callStationIdCase lower and authentication 44 include-in-access-req +accounting username-case lower and accounting callStationIdCase lower.
Unfortunately, it didn't help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2022 04:20 AM
Then I think you need to open a TAC case.
If there was a general bug I'm sure lots of other people would have seen this so I suspect something specific to your setup.
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.196.0, latest 9800 releases, 8.5.182.12 (8.5.182.13 for 3504) and 8.5.182.109 (IRCM, 8.5.182.111 for 3504)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Default AP console baud rate from 17.12.x is 115200 - introduced by CSCwe88390
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2022 05:08 AM
ehhh, obviously, but I can't
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-31-2022 11:30 AM
Is the APs are in Local mode or Flex mode?
Do you have any SVI's configured in your WLC? (interface Vlan with IP address apart from the WMI)
Are you using any VLAN Groups? If yes did the client get an IP from a vlan in the pool?
TAC recommended codes for AireOS WLC's
Best Practices for AireOS WLC's
TAC recommended codes for 9800 WLC's
Best Practices for 9800 WLC's
Cisco Wireless compatibility matrix
___________________________________________
Arshad Safrulla
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2022 04:28 AM
Hi, Arshad.
Local mode and yes, I configured SVI per vlan (vlan 4, vlan 2, vlan 1114) and made vlan group and mapped it to wlan interface.
Users get IP, but these IP not correct because they moved to incorrect vlans (I expected vlan 4 for users, but they put to vlan 1114 or vlan 1360 etc)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-01-2022 05:21 AM
Hi Peter,
I would suggest you to read the best practices guide (link in my signature). Please start fixing the issues highlighted by the config analyzer first and then check how you can incorporate the best practices to your design.
For 9800s you don't need to configure any SVI's for any VLANs attached to WLANs unless you use mdns or dhcp bridging. So you can start removing them from the WLC if not needed. Also make sure that you don't use any Native VLAN's connecting to WLC uplinks from switch and WLC side both. For AP connecting switchports use the AP management VLAN as the native VLAN and also refer the below section form the best practices guide to understand why you need the policy profile configured correctly.
- https://www.cisco.com/c/en/us/products/collateral/wireless/catalyst-9800-series-wireless-controllers/guide-c07-743627.html#:~:text=mode%2C%20as%20expected%3A-,Local%20switching,-Enable%20local%20switching
- https://www.cisco.com/c/en/us/products/collateral/wireless/catalyst-9800-series-wireless-controllers/guide-c07-743627.html#:~:text=has%20lower%20security.-,Use%20of%20VLAN%201%20in%20a%20Policy%20Profile,-To%20configure%20the
Also make sure that you allow only the required VLAN's on the trunk ports connecting to the WLC. I am pretty certain that this is a configuration issue in your WLC. I have almost 50 WLC's deployed for K12 currently working with NPS for dynamic VLAN assignment mostly on 17.3 codes and also 17.6 codes where we have all Catalyst APs.
TAC recommended codes for AireOS WLC's
Best Practices for AireOS WLC's
TAC recommended codes for 9800 WLC's
Best Practices for 9800 WLC's
Cisco Wireless compatibility matrix
___________________________________________
Arshad Safrulla
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-02-2022 11:39 AM
Could you check that your WLC's configuration matches the configuration from this guide:
The guide uses Cisco ISE but if your NPS is already working with a 5520 then it should also work with the 9800
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-14-2022 04:07 AM
Hi again...
In general, there was needed authorization config
simple... but not obviously
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide