- Cisco Community
- Technology and Support
- Collaboration
- Collaboration Knowledge Base
- CUCM Uploading CCMAdmin Web GUI Certificates
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-05-2009 11:48 AM - edited 03-12-2019 09:21 AM
1. Verify Hostname and Settings
Certificates are based on names. Make sure the names are correct before starting.
From SSH CLI
admin: show web-security
Subject: CN=CUCM7-PUB.bbbburns.lab, OU=TAC, O=Cisco, L=RTP, ST=North Carolina, C=US
X509v3 Subject Alternative Name:
DNS:CUCM7-PUB.bbbburns.lab, DNS:CUCM7-Pub
Use CLI to change these settings if desired
In the next example we move to BXB, and set an Alternate name of “ThePub” so we can type that into our browser
admin: set web-security TAC Cisco BXB Massachusetts US ThePub
After running "set web-security" Tomcat must be restarted for the new certificate to be used when accessing CCMAdmin and CCMUser.
admin: utils service restart Cisco Tomcat
2. Generate and Download CSR
OS Admin > Security > Certificate Management > tomcat.pem > Generate CSR
Download CSR (CUCM7-Pub.csr)
Note: Prior to CUCM 8.0(3), these Tomcat CSRs were generated with 1024 bit RSA keys. With the resolution of defect
CSCso62711 Cert Manager should generates Tomcat CSR using RSA 2048 instead of 1024
CUCM in versions 8.0(3) and later will generate a 2048 bit key / CSR for Tomcat. This defect currently only addresses Tomcat in 8.0(3). Other types of CSRs (like CallManager) will be addressed in future versions. Follow defect CSCtn01236 for 2048 bit updates.
3. Submit CSR to CA
Open the CSR file downloaded from the previous step (CUCM7-Pub.csr in this example) in Notepad and copy the entire contents including the ---BEGIN CERTIFICATE REQUEST--- and ---END CERTIFICATE REQUEST-- lines.
If your CA is Windows 2k3
https://<CA Server Name: In my example JASBURNS-AD>/certsrv > Advanced Certificate Request
Paste the contents into this window to submit the request.
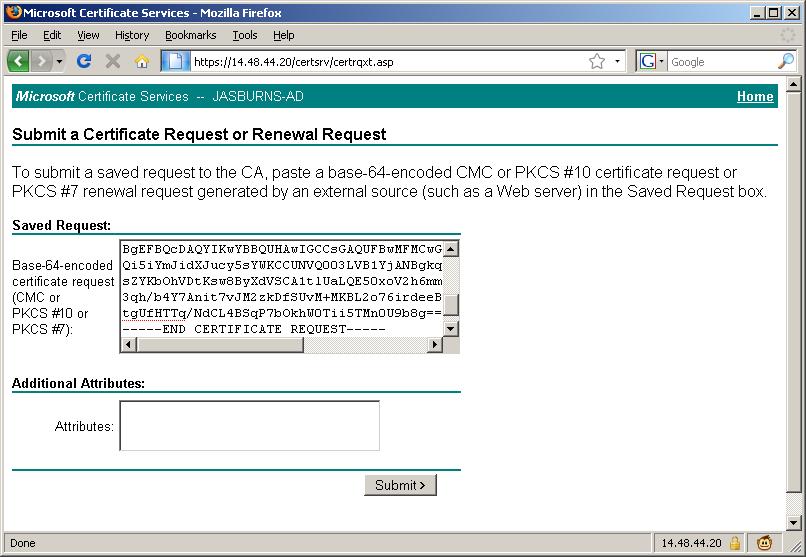
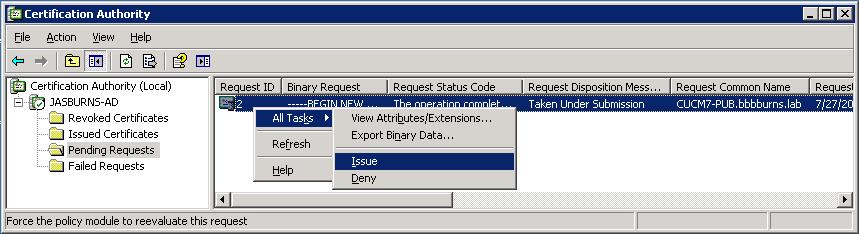
4. CA Approves CSR
This is where the magic happens.
The CA inspects the CSR and determines if the person submitting the CSR really owns CUCM7-PUB.bbbburns.lab
With Verisign or GoDaddy this step will require payment, and email or maybe even human verification
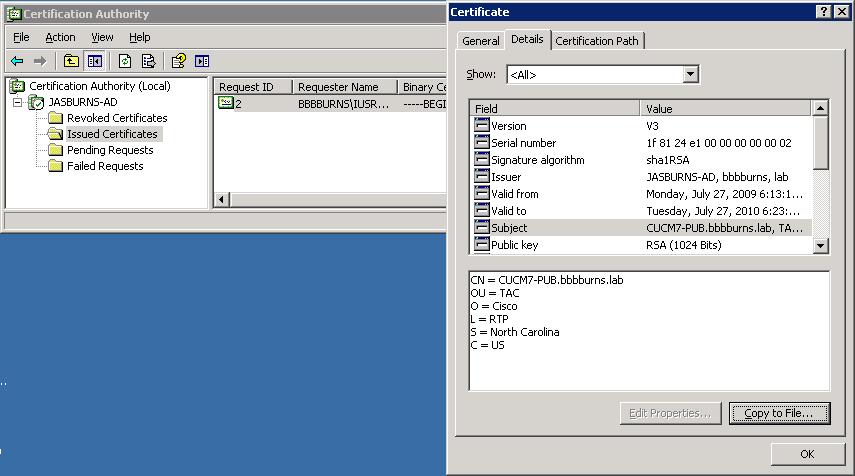
5. Server Admin Downloads Issued Cert
With Win2k3 go to CA MMC > Issued Certificates > Copy to file > Base-64 > (CUCM7-Pub.bbbburns.lab.cer)
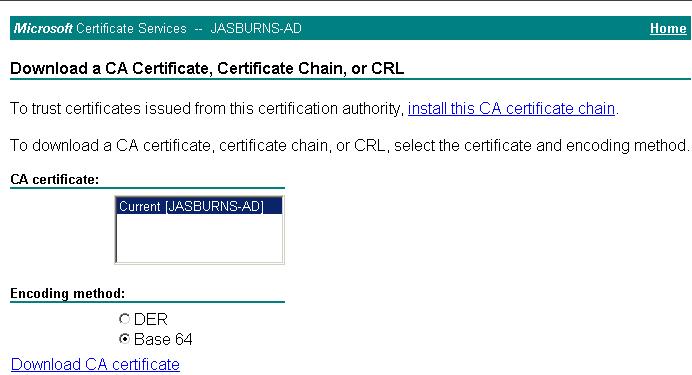
6. Server Admin downloads CA Cert
The Server Admin must build a complete chain of certs, so needs to download the root CA cert
https://<CA Server Name: In my example JASBURNS-AD>/certsrv > Download CA Cert > Base-64 > (jasburns-ad_PEM.cer)
7. Server Admin Uploads Root Certificate(s) as tomcat-trust
CUCM Server needs to have all certificates in the chain uploaded, starting at the top (root).
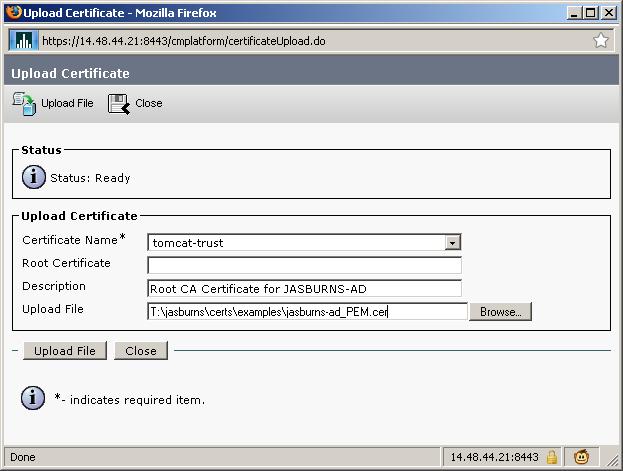
Note that the name of the file uploaded is jasburns-ad_PEM.cer. This is a Base64 encoded PEM file. Once it gets uploaded to CUCM though it will show up with filename JASBURNS-AD.pem. CUCM changes the name of the file to <SUBJECT CN>.pem.
7b. Uploading an intermediate certificate
This step is only necessary if the Certficate Authority (CA) has provided a signed certificate with multiple certificates in the certificate chain as shown.
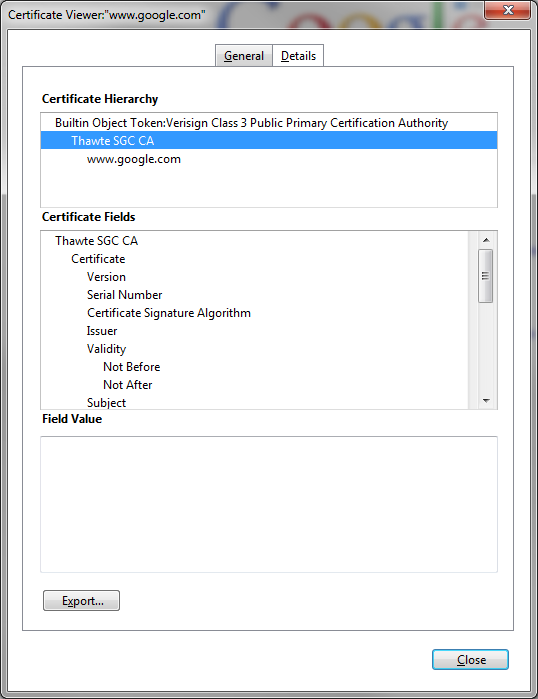
After uploading the root certificate in Step 7, export the intermedia certificate and upload it as a Tomcat-trust also while specifying the filename (minus the extension) of the root certificate in the "Root Certificate" field.
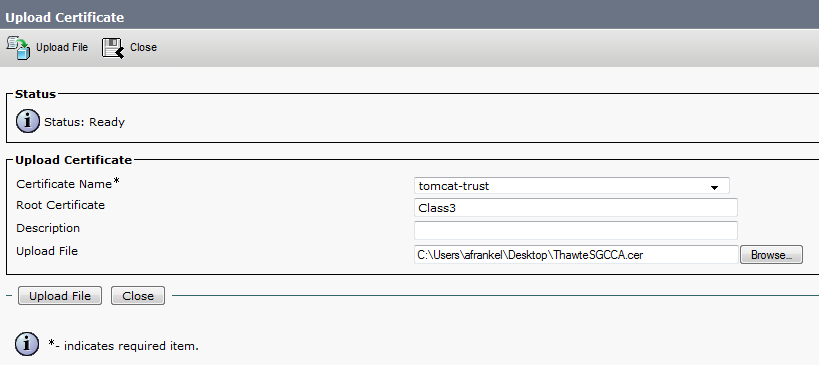
If there are more intermediate certificates in the chain, each one will need to be uploaded in order until finally uploading the signed certificate as shown in Step 8.
The purpose here is to build a chain of certificates. We upload the root certificate and leave the root cert field blank. When we upload the 1st intermediate certificate we put the file name of the root certificate in the root cert field. If there is 2nd intermediate, we put the name of the 1st intermediate in the root cert field. This builds the chain of trust that can be followed from the identity certificate to the root certificate.
8. Server Admin Uploads Identity Certificate as tomcat
This is the identity certificate issued by the CA.
Complete the cert chain by specifying .pem root cert. Note that the name below is JASBURNS-AD.pem. That's because I went to the OS Admin Certificate page to get the name of the newly uploaded tomcat-trust certificate from the last step. This is VERY important.
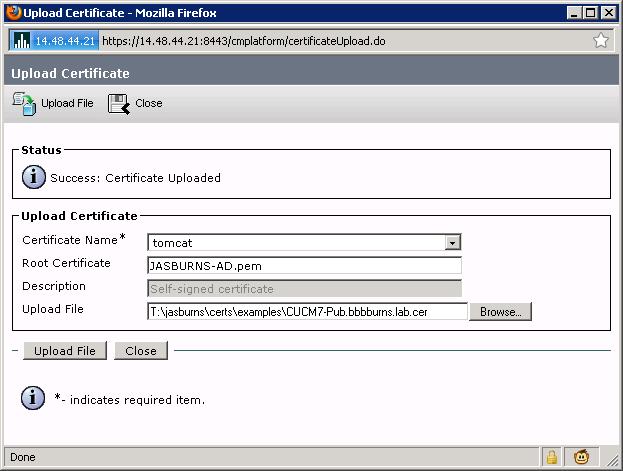
The root certificate you specify here could be the name of the root cert, or the name of some intermediate cert. The purpose is to find the certificate that signed the identity certificate, and use that certificate file name in this root cert field.
9. Restart Tomcat
This one is pretty simple. Just restart Tomcat from the SSH CLI
admin: utils service restart Cisco Tomcat
When Tomcat comes back up you can access the CCMAdmin or CCMUser GUI to verify your newly added certificates in use.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
In your example you show a cert with multiple alternative names, however the set web-security command won't accept multiple alternative names -- or perhaps I don't know what the correct syntax is. I tried commas, quotes, and various combinations. What I'd like is a FQDN for the cert such as CUCM01.mydomain.com, an alternate name of CUCM.mydomain.com (which via DNS would resolve to any server in the cluster), and a "friendly" name such as CALLMANAGER (without the domain name). To do this I need to be able to enter two Alternate Names however as I said the CLI on my 8.5 system does not seem to allow it, nor do the docs say it can be done. But your example above seems to indicate it is possible:
admin: show web-security
Subject: CN=CUCM7-PUB.bbbburns.lab, OU=TAC, O=Cisco, L=RTP, ST=North Carolina, C=US
X509v3 Subject Alternative Name:
DNS:CUCM7-PUB.bbbburns.lab, DNS:CUCM7-Pub
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
CUCM 10.5
When I generate CSR , there is a field there called Domain name and usually shows the companyname.com
I was told that in 10.5 this is needed as in this version, the pub propagates the certs to all the other servers in the cluster.
Also, in the CSR generation, I choose CallManager. My goal is to encrypt the call. Am I missing something? thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I'm interested in doing this too on CUCM 10.1. I'd like to have 3 SANs. I cannot find a way of doing this via the CLI.
Any suggestions?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
In 10.x, specifying a SAN has changed a bit. You can now specify multiple SAN's when generating the CSR from the OS Admin page.
HTH.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I think it's specifically 10.5 onwards as I cannot see an option in 10.0 to have multiple SANs.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Correct. Prior to 10.5, you'll only be able to set a single SAN -- with the CLI.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you very much for this procedure.
I wish I had this file back in September when I was first attempting to install certificates. This made it relatively painless. Can you do one for CUPS (IM & Presence) as they have 2 certs one for Tomcat and one for XMPP?
Also with CUCM9 adding the intermediate certificate does not require to point back to the root certificate.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi All,
I'm conscious that im replying to a 4 year + old post, However believe people still use this information as its a good guide to follow when executing CCMAdmin Tomcat Certs.
So my issue.
I recently renewed my certificate by basically generating a new CSR and having them signed. Uploaded in the normal fashion and restarted the Tomcat Service..... All good for another couple of years.
However I'm still getting these RTMT alerts (Below) any idea how to make them stop?
Been getting them for
(I've replaced the CUCM Name with XXXXXX)
SeverityMatch : Critical
MatchedEvent : Mar 5 00:00:07 XXXXXX local7 2 : 207: XXXXXX : Mar 05 2015 00:00:07.473 UTC : %UC_CERT-2-CertValidfor7days: %[Message=Certificate expiration Notification. Certificate name:XXXXXX.der Unit:tomcat-trust Type:own-cert Expira][AppID=Cisco Certificate Monitor][ClusterID=][NodeID=XXXXXX]: Alarm to indicate that Certificate has Expired or Expires in less than seven days AppID : Cisco Syslog Agent ClusterID :
NodeID : XXXXXX
TimeStamp : Thu Mar 05 00:00:07 GMT 2015
Any assistance will be great.
Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Jon,
This is the remaining tomcat-trust cert automatically propagated from your previous certificate. To effectively remove this you will need to stop the Certificate Notification Service on all nodes from the Unified Serviceability page, delete the cert from the OS Admin page on every node, then start the service back up.
HTH
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi all,
thanks for posting that guide.
One question, is it the same logic if I woul like to use CA Trusted Callmanager certs ?
Thanks,
Stefan
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have expired certs that are no longer being used so is it safe to delete all certs in the cahin without reprecutions after stopping the services noted and do I need to restart tomcat?
i.e. CallManager-trust Type:own-cert
Unit:tomcat-trust Type:own-cert
Message=Certificate expiration Notification. Certificate name:servername.der Unit:tomcat-trust Type:own-cert Expiration:Wed Nov 4 16:09][AppID=Cisco Certificate Monitor][ClusterID=][NodeID=servername]:
SeverityMatch : Critical
MatchedEvent : Nov 2 18:00:09 servername local7 2 : 73: servername.domain: Nov 03 2015 00:00:09.842 UTC : %UC_CERT-2-CertValidfor7days: %[Message=Certificate expiration Notification. Certificate name:CAPF-700d51b4.der Unit:CallManager-trust Type:own-cert Expiration:Wed Nov 4][AppID=Cisco Certificate Monitor][ClusterID=][NodeID=servername]: Alarm to indicate that Certificate has Expired or Expires in less than seven days AppID : Cisco Syslog Agent ClusterID :
NodeID : servername
TimeStamp : Mon Nov 02 18:00:10 CST 2015
SeverityMatch : Critical
MatchedEvent : Nov 2 18:00:09 servername local7 2 : 74: servername.domain: Nov 03 2015 00:00:09.844 UTC : %UC_CERT-2-CertValidfor7days: %[Message=Certificate expiration Notification. Certificate name:servername.der Unit:CallManager-trust Type:own-cert Expiration:Wed Nov 4 ][AppID=Cisco Certificate Monitor][ClusterID=][NodeID=servername]: Alarm to indicate that Certificate has Expired or Expires in less than seven days AppID : Cisco Syslog Agent ClusterID :
NodeID : servername
TimeStamp : Mon Nov 02 18:00:11 CST 2015
SeverityMatch : Critical
MatchedEvent : Nov 2 18:00:09 servername local7 2 : 75: servername.domain: Nov 03 2015 00:00:09.846 UTC : %UC_CERT-2-CertValidfor7days: %[Message=Certificate expiration Notification. Certificate name:publisher.der Unit:CallManager-trust Type:own-cert Expiration:Wed Nov 4 ][AppID=Cisco Certificate Monitor][ClusterID=][NodeID=servername]: Alarm to indicate that Certificate has Expired or Expires in less than seven days AppID : Cisco Syslog Agent ClusterID :
NodeID : servername
TimeStamp : Mon Nov 02 18:00:12 CST 2015
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
QUALITY POST: ONLY issues I have with it is that there isn't direct specification of process with reguards to Unity and IM/P.
I'm dealing with a 9.1.2 environment: and I'm checking my self against this and TAC to confirm.
SHOULD Subs' certs be imported through the Pub, or on the CM Sub directly?
You have to import the CUC cert chain on the CUC directly...(in 9).
I see the date here : so I know I'm late to the party on this conversation.
I note changes from 7 to 8 in this specific arena.
I'd LIKE to see a follow up / repost of the above with a brief run down of major diff from 7, 8, 9, 10 and 11 so that this one doc could be a one-stop-shop answer for the whole of the process.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
These procedures worked in version 6,7 and 8 ... we recently upgraded to version 10.5, and they no longer work.
how do you down load the new CSR after it is generated? the icon to "download CSR" no longer appears.
If I understand correctly, we no longer have to have to do this for all the servers in the cluster ... how is it done now ?
thanks!
CID
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Jose,
Just a quick one did you find solution for version 10.5? If yes, can you please share it with us. Currently I am updating all our certificates. We are using CA LSC CAPF. Can you please advice if your outcome is any different?
Another question, When you upload the certificates to CUCM do you need to also upload it in subscriber or is it just Pub. Reason for this question is I downloaded 5 CSR certificates from each server.
Please Advice
Gengad
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The button to download a CSR is there in 10.5 just as it is shown in the screenshots above.
If you are using a CA to sign endpoint LSC certificates then you have to get the CSRs from the CLI. Follow the steps in the UCM Security Guide.
For your second question Trust certs are propagated to the entire cluster by the Cisco Certificate Change Notification service. Multi-server certificates are only uploaded to the publisher. Single-server identity certs must be uploaded to the server that generated the CSR.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: