Some applications use a technique referred to as TLS/SSL pinning or certificate pinning, which embeds the fingerprint of the original server certificate in the application itself. As a result, if you configured a TLS/SSL rule with a Decrypt - Resign action, and this rule matches this traffic, when the application receives a resigned certificate from Cisco FTD (Firepower Threat Defense), the validation fails and the connection is aborted.
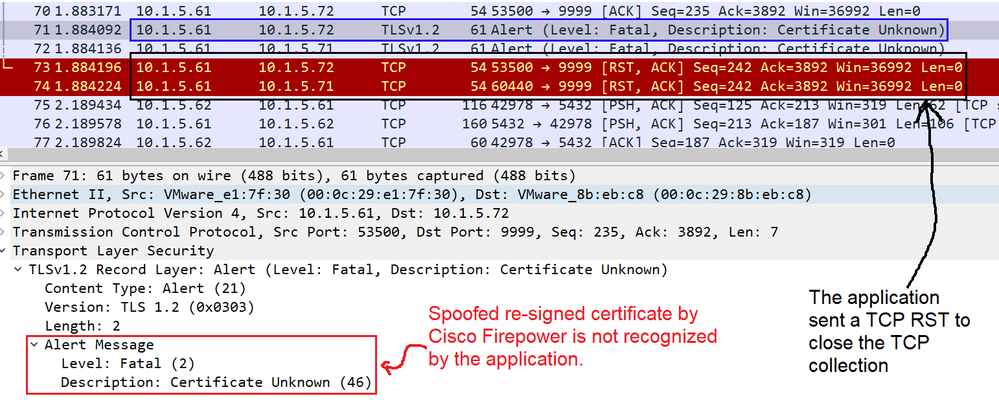
In the capture wireshark from the client side connection or the application you can detect this failed validation with the TLS alert message , The Alert Message indicates the spoofed re-signed certificate is not recognized by the application because the application is expecting to receive and validate only server certificate signed by a specific CA (Certification Authority) but it is receiving the server certificate signed by the Firewall Cisco FTD, finally a TCP Reset is sent by the application to close the TCP connection.
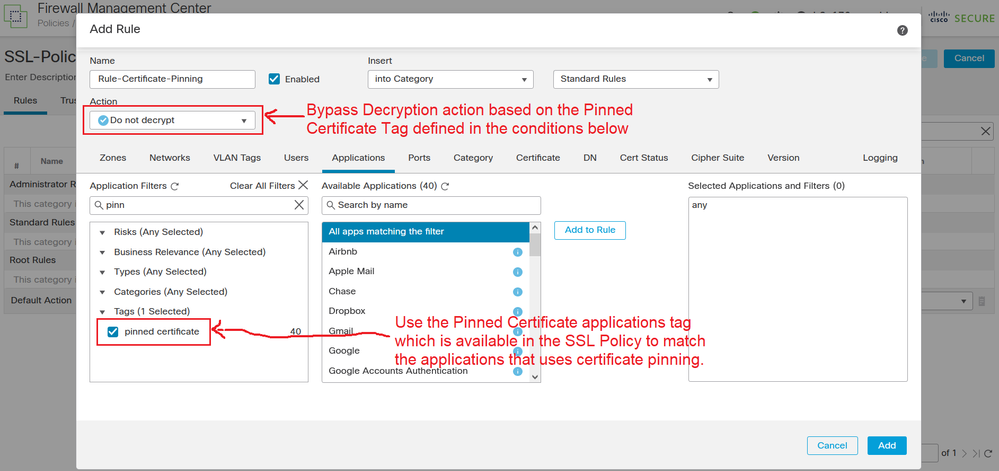
If your browsers or your applications uses certificate pinning to verify a server certificate, you cannot decrypt this traffic by re-signing the server certificate. You can use Pinned Certificate applications tag available in the SSL Policy. Use this tag to match application traffic that should bypass decryption with Do not decrypt action.
For collaboration fans, Certificate Pinning is largely deployed for Cisco Meeting Server C2W CallBridge to WebBridge Connection to prevent rogue webbridges.
