CRL Checks on Cisco ASA /FTDs
IntroductionCisco ASAs and FTDs can be configured with Certificate Authority to perform various jobs, like authenticating the users based on certificates before they connect to the VPN. However, the c...

IntroductionCisco ASAs and FTDs can be configured with Certificate Authority to perform various jobs, like authenticating the users based on certificates before they connect to the VPN. However, the c...

How to troubleshoot VOIP issues with Firewalls First, VoIP traffic has two components: 1-Signalling: Process of establishing and terminating calls Commonly used protocols are SIP, H.323, MGCP, Skinny,...

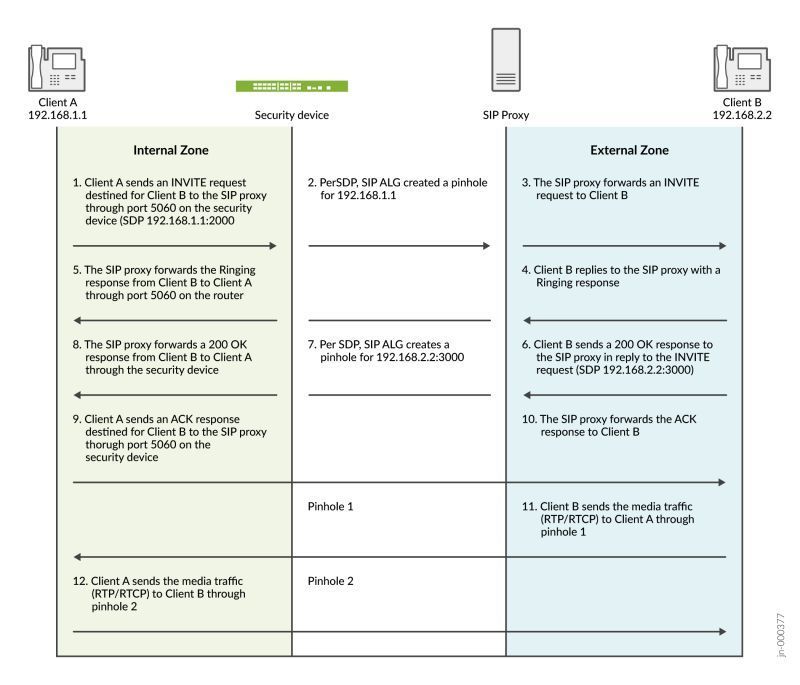
What is SIP ALG Application Layer Gateway and SIP Pinhole.SIP ALG is a feature where the firewall will inspect the SIP packets to perform Layer 7 NAT ( from private IP to public IP).Goal of SIP ALG1- ...
If you work in a large data center and your task is to support firewalls (Cisco ASA), then you probably encountered a huge number of lines in their configurations. These configurations can include tho...

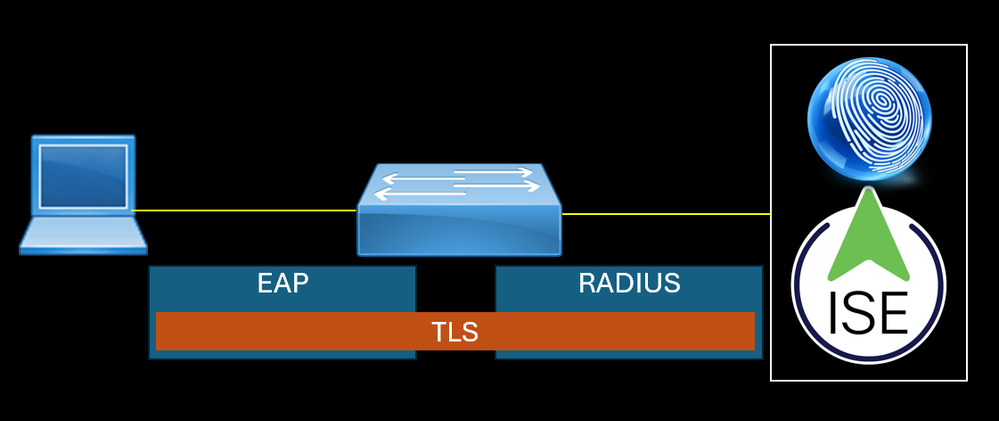
EAP runs over Layer 2 of the OSI model, the data link layer, and doesn't require Layer 3 IP connectivity. EAP Packet sent by the endpoint does not have L3 and L4 headers, the L7 data is encapsulate...
Today’s threats are evolving quickly and security tools and the professionals who manage them cannot keep pace to effectively defend their organizations, let alone take proactive steps to stay ahead o...

Cisco ISE system certificates are server or entity certificates that validate a Cisco ISE node in inter-node communication and to end users such as guest and device portal. System certificates are ...

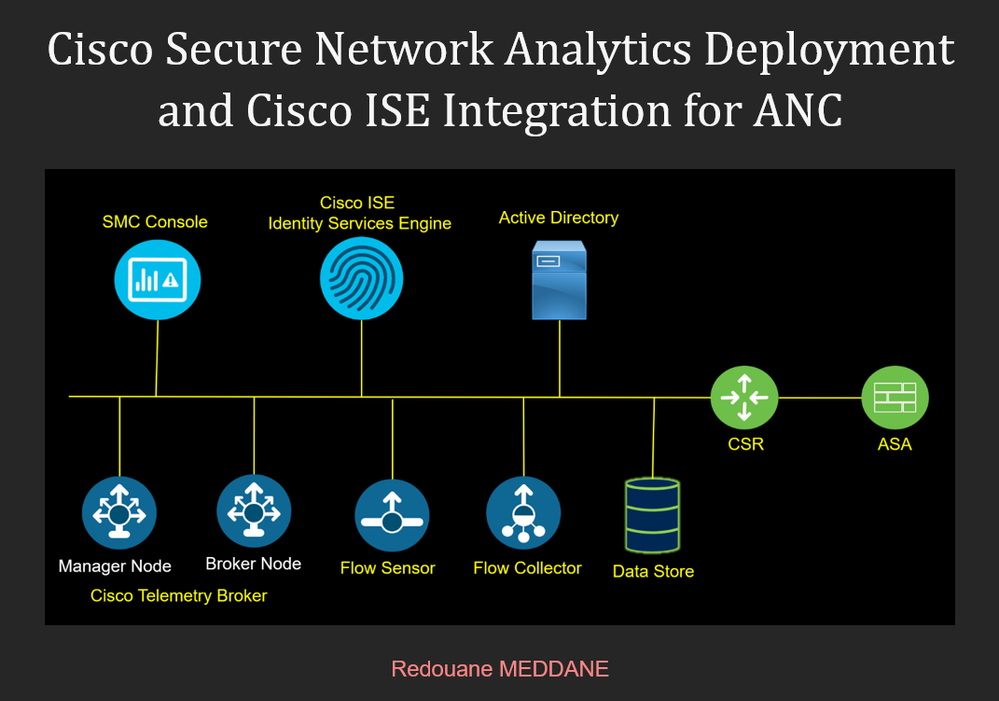
Full Cisco Secure Network Analytics Appliances Deployment and Integration with Cisco ISE using PXGrid for ANC and Automatic Response. I finished to write a complete guide of Cisco Secure Network Ana...
We recently hosted a live stream with Cisco DevNet discussing AI security. The session covered a range of topics, from current vulnerabilities in AI systems to future trends, the risks associated with...

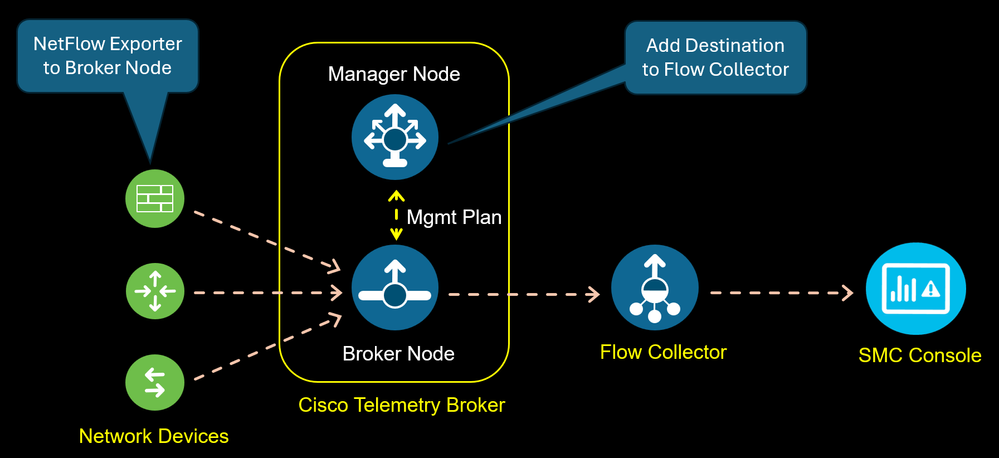
Cisco Telemetry Broker Architecture in Cisco Secure Network Analytics Solutions.The architecture of Cisco Telemetry Broker consists of two components: -Manager Node-Broker Node. Broker Nodes are all m...
Objective:Connect two machines at same time to allow them to authenticate using EAP-TLS and PEAP at the same time.

Hello Team, I hope you are doing great, I have an external Radius Server (Secure W2 Radius), in which a have a Network Policy for Dot1x in which the only condition I have is NAS-Port-Type Ethern...

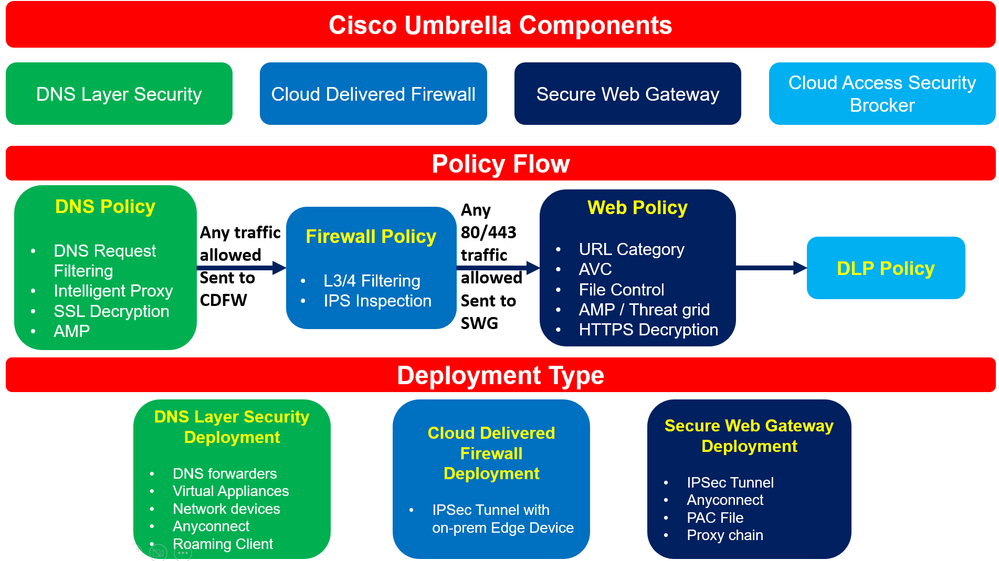
Umbrella offers a broad set of security functions that until now required separate firewall, web gateway, threat intelligence, and cloud access security broker (CASB) solutions. Umbrella DNS is resolv...
Zero Trust architecture is the new trend of Security Philosophy based on the principe, never trust and continuously verify trust, which means even if the user is authenticated and permitted to access ...

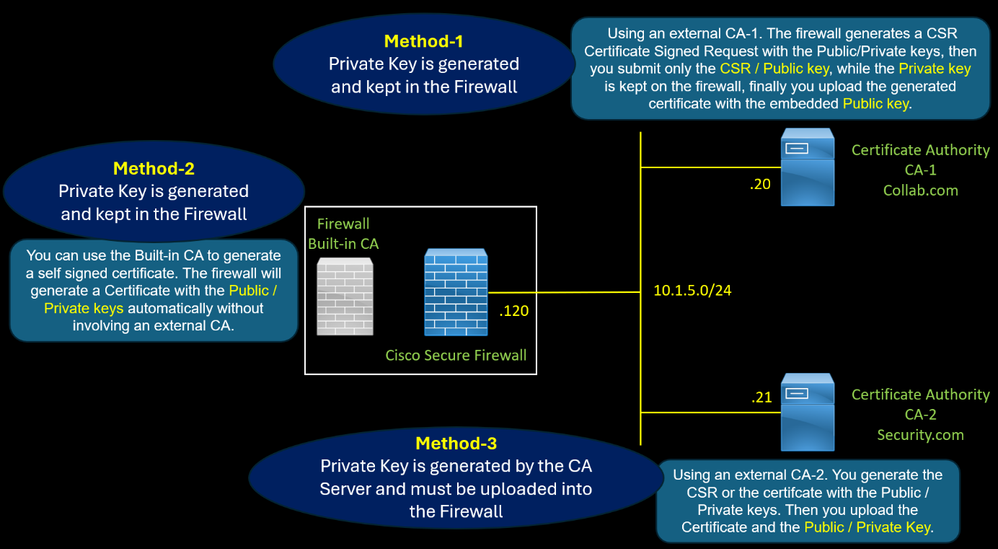
The firewall uses a certificate with the role of CA Certificate of Authority to perform SSL Decryption for outbound traffic. There are three methods to generate this certificate. Method 2 : Using a...