Hello, Cisco Community!I’m really happy to share that I’ll be hosting the Cisco Community Lab Series, a brand-new hands-on learning journey designed to help you build practical networking skills step by step.Every Thursday at 8 PM EST, I’ll post a ne...
Switching
- Cisco Community
- Technology and Support
- Networking
- Switching
- Mark all as New
- Mark all as Read
- Float this item to the top
- Subscribe
- Bookmark
- Subscribe to RSS Feed
- Threaded format
- Linear Format
- Sort by Topic Start Date
-
2960X stack issue
(1) -
9200L Bundle Install Mode
(1) -
9300
(1) -
AAA
(7) -
Access Control Server (ACS)
(2) -
ACI
(2) -
ACI App Center
(1) -
AMP for Endpoints
(1) -
Announcements
(3) -
Application Networking
(1) -
Assurance and Policy
(1) -
Autres sujets de Commutation
(1) -
Autres sujets de Routage
(1) -
boot
(1) -
Branch Router
(769) -
Buying Recommendation
(342) -
BYOD
(1) -
C1000 cluster
(1) -
c3850
(1) -
c9200
(1) -
C9200-24P-E Support Contract
(1) -
C9500-16X
(1) -
Catalyst
(1) -
Catalyst 2000
(1,840) -
Catalyst 3000
(2,686) -
Catalyst 4000
(944) -
Catalyst 6000
(894) -
Catalyst 8000
(101) -
Catalyst 9000
(4,063) -
Catalyst 9000 Switches
(9) -
Catalyst Switch
(31) -
Cisco ACI
(3) -
Cisco Adaptive Security Appliance (ASA)
(1) -
Cisco Annual Internet Report
(1) -
Cisco Bugs
(30) -
Cisco Cafe
(93) -
Cisco Catalyst Center
(35) -
Cisco Digital Network Architecture-DNA
(3) -
Cisco DNA Assurance
(1) -
Cisco DNA Automation
(1) -
Cisco DNA Center
(2) -
Cisco Firepower Management Center (FMC)
(1) -
Cisco IE-2000(U) EIGRP vs EIGRP Stub
(1) -
Cisco ONE
(5) -
Cisco Press Cafe
(3) -
Cisco Software
(74) -
Cisco Spaces
(2) -
CISCO START ASEAN
(3) -
Cisco Start India
(5) -
Cisco SW
(1) -
Cisco User Groups
(1) -
Cisco.com Idea Center
(5) -
CiscoChat
(6) -
Cloud Networking
(2) -
Collaboration
(1) -
Collaboration Endpoints
(1) -
Collaboration Solutions
(5) -
Community Bug or Issue
(9) -
Community Feedback Forum
(130) -
Community Ideas
(59) -
Commutation
(2) -
Compliance and Posture
(1) -
Conferencing
(1) -
Configuration
(12) -
Contact Center
(1) -
CSC Content with No Valid Community to Post
(12) -
Data center
(1) -
Data Center Networking
(3) -
Desk Endpoints
(1) -
Device Admin
(7) -
EEM Scripting
(5) -
Email Security
(2) -
etherchannel
(1) -
Firewalls
(1) -
General
(3) -
Guest
(1) -
Identity Services Engine
(1) -
Identity Services Engine (ISE)
(6) -
Industrial Switching
(1) -
Integrations
(1) -
Intent Based Networking
(1) -
iOS
(1) -
IOS issue
(1) -
IOS Version
(1) -
ios xe
(1) -
IP Phone and Accessories
(1) -
IP Phones and Accessories
(1) -
IPS and IDS
(1) -
IPv6 Configuration
(1) -
ISE
(1) -
ISR 4000 Series
(1) -
LAN
(9) -
LAN Switching
(20,329) -
LAN Switching and Routing
(1) -
License
(1) -
Meraki
(1) -
Meraki Switch
(174) -
Movilidad
(1) -
Multi-Domain
(1) -
Network Assurance
(1) -
Network Management
(110) -
Network Security
(1) -
network stich issue
(1) -
Networking
(4) -
New Document Idea
(3) -
Nexus
(1) -
Nexus 7000
(1) -
Nexus 9000
(1) -
Nexus Dashboard Insights
(1) -
Nexus Series Switches
(3) -
NGIPS
(1) -
NX-OS
(1) -
Online Chat Support
(2) -
Online Tools and Resources
(4) -
Optical Networking
(12) -
Other Cisco DNA
(3) -
Other Cisco.com Ideas
(1) -
Other Collaboration Applications
(8) -
Other Collaboration Endpoints
(3) -
Other Collaboration Topics
(18) -
Other Community Feedback
(9) -
Other Data Center Switches
(2) -
Other Data Center Topics
(1) -
Other Identity Services Engine (ISE)
(1) -
Other IP Telephony
(1) -
Other NAC
(3) -
Other Network
(23) -
Other Network Architecture
(1) -
Other Network Security Topics
(8) -
Other Networking
(26) -
Other NGFW Firewall Topics
(1) -
Other NGFW Firewalls Topics
(1) -
Other Policy-Access Topics
(2) -
Other Routers
(6) -
Other Routing
(11) -
Other Routing and Switching topics
(13) -
Other SD-WAN
(2) -
Other Security Topics
(3) -
Other Storage Networking
(1) -
Other Switches
(6,197) -
Other Switches Routing
(8) -
Other Switching
(75,054) -
Other Wireless - Mobility Subjects
(1) -
Other Wireless and Mobility Subjects
(7) -
Peripherals
(3) -
Physical Security
(2) -
Positive Feedback
(3) -
Primary boot loader issue
(1) -
Prioritization
(1) -
Remote Access
(1) -
Room Endpoints
(1) -
Routing
(172) -
Routing Protocols
(11) -
SD-Access
(4) -
SD-WAN
(1) -
Security
(2) -
Security Management
(5) -
Security Policy-Access
(2) -
Small Business Network and Smart Storage
(1) -
Small Business Routers
(2) -
Small Business Security
(1) -
Small Business Support Service
(1) -
Small Business Switches
(36) -
Small Business Wireless
(1) -
Smart Call Home
(1) -
smart net total care portal and collector
(1) -
Software Upgrades
(9) -
Storage Networking
(4) -
Support
(7) -
Switches
(20) -
Switching
(34) -
Switching or Switches
(3) -
Swtiches
(3) -
Technical Documentation
(11) -
Technical Documentation Ideas
(1) -
UCCE CTI Protocol
(1) -
UCS Networking and Storage
(2) -
UCS Solutions
(1) -
Unified Branch
(1) -
Unified Computing System (UCS)
(3) -
Update Document
(1) -
Voice Gateways
(1) -
VPN
(1) -
WAN
(405) -
Webex Meetings
(1) -
Wi-Fi 6
(73) -
Wired
(5) -
Wireless Controllers
(1) -
Wireless Network Management
(1) -
Wireless Security and Network Management
(2) -
XR OS and Platforms
(3) -
YANG Development Kit (YDK)
(1) -
ルータ一般 (IOS & IOS-XE)
(1)
- « Previous
- Next »
Forum Posts
This is new installation. able to login 192.168.1.1 and default login in Cisco. also i had successfully configured management interface g0/0. ip 10.131.61.7. its shows configuration was successful. but i could not able to access 10.131.61.7 in direc...
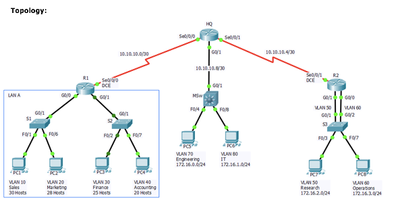
Hi! Does anyone know here what is the command for these tasks?:Configure static routing on HQ with route summarization to VLAN 10, 20, 30 and 40. Identify and configure all other remote networks of HQ.Configure static routing on R1 with route summar...
Good Afternoon,we had a power failure in the premises last week and after that one of our Switch is rebooting over and over and we can not login to the console the message displayed is "error reading the serial port".do someone here face such an iss...
Hi, Is it possible to use C9400 one supervisor slot for linecards to connect endpoints..? C9400 have 2 SUP slots, one among is using as SUP and other one is empty as of now. So we thought to use it for Linecards. Is it possible..? Please post y...
Good day I want to find out if it is possible to block a specific port within a vlan so that the user on that port do have access to the network resources like other user pc's, print ect but not to the internet vlan or port? the switch is a Cisco Cat...
Resolved! port switch is not stable
problem port is not stable i have a switch 2960-X linked with WLC 1815i with inter gi/0/15 probleme : port switch : green ( 60 seconde ) then Off ==> i would port switch green stable that allow WLC is green ? what comand used to trouble s...
Dear all, I would just like to confirm the following mismatched specification on Cat3K different version. So normally in my understanding when locally DOT1X authentication success then the switches learn & create IP-SGT mapping table below but acc...
hey i am practicing at home with packet tracer. i have two networks both have one router and a switch and a Pc.i am trying to make both ospf and eigrp talk to each on each router over a serial cable. i cant figure out how to make them take and make t...

Good Day, With respect to DHCP, If i shut/noshut a VLAN interface will that trigger a request from the client for a new IP lease? I know it will if applied directly to the interface. Thanks in advance.AUSD
How do I setup the Network Policy Server in Windows Server 2016 in order to added as my RADIUS server in the Switches and Routers Cisco? Thanks
I've got a switch stack of 3 WS-C3650-48PQ. Currently ports 1/1/1 and 1/1/2 are servicing 1 gig connections. Ports 2/1/1, 2/1/2, 3/1/1, & 3/1/2 are all servicing 10 gig connections. I've got a device I've patched into all the open ports and none of t...
I have problem with router 2921 it restart and get in console:" WARNING: DDR ECC errors detected!Memory POST Test FailedFailed all 0xffffffff testBad RAM at location 0x8040375C: wrote 0xFFFFFFFF, read 0xFFFBFFFF%%ERROR: DDR memory test failed! Stop.W...
I am reviewing our console servers to make sure that each console connection actually goes to the device that it's labeled as. What is puzzling me is that in some scenarios we'll have a switch stack of say 3 switches....I console into [supposedly] s...
I have just started deploying Avaya IP phones on Cisco 2960X switches stacked. After some time a block of 14 ports will quit providing POE. Nothing fixes the issue until we cold boot the switch. Anyone has this problem? Here is stack information ...
Hello, how would i verify which ACL is applied to a specific VLAN? CAT 4500 switch.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
| Subject | Author | Posted |
|---|---|---|
| 12-07-2025 12:41 PM | ||
| 12-04-2025 11:01 AM | ||
| 11-27-2025 10:43 AM | ||
| 11-25-2025 10:49 AM | ||
| 11-20-2025 11:03 AM |
| User | Count |
|---|---|
| 7 | |
| 5 | |
| 4 | |
| 4 | |
| 2 |
