Cisco Umbrella Web Policy Matching Logic
Web Policy Rulesets Rulesets are “containers” for rules. A Web policy ruleset defines a collection of identities and rules. Rulesets can include identities from a specific geographic area or physical ...
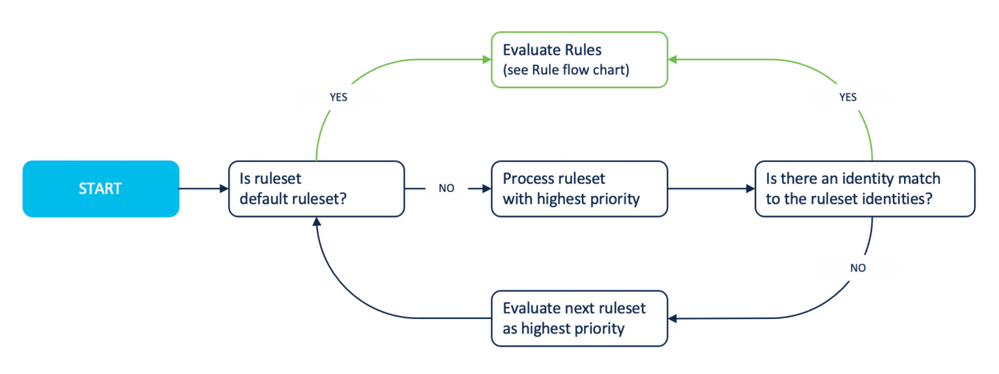
Web Policy Rulesets Rulesets are “containers” for rules. A Web policy ruleset defines a collection of identities and rules. Rulesets can include identities from a specific geographic area or physical ...

Step 1: Configure posture conditions Windows Assets can be marked as ‘Compliant’ when: Windows update agent is runningAny Firewall product is runningAny Anti-Malware software is installed Create a co...
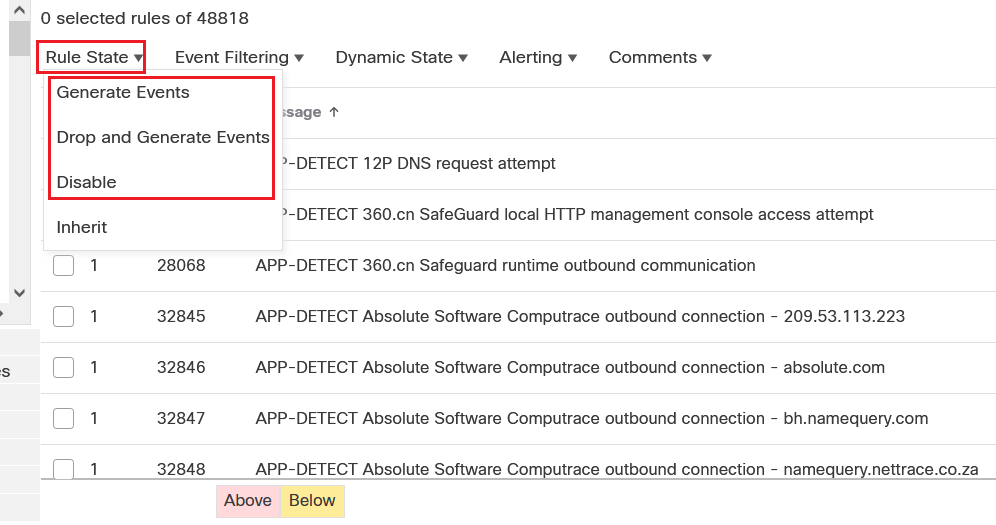
Rule States/Action - Snort Version 2 versus Snort Version 3 Snort 3 calls this rule Action. Snort 2 calls this rule State Snort 2 rule states: Generate EventsDrop and Generate EventsDisable Snort...

Come and have lunch with the Security team at Cisco Live US to get a sneak peek of our latest announcements, request a meeting with our executives, and challenge yourself at Capture the Flag.

How can information security leaders ensure that employee usage of artificial intelligence tools to help increase organizational productivity is not putting sensitive company data at risk of leakage? ...

Happy RSAC Monday! The long-awaited day has come – we are so excited to announce the launch of Cisco XDR!

Good Afternoon All,I am looking at replacing our FTD 4110 with a FTD 3110. I have a few questions please?1) is it possible to export the complete configuration for the 4110 and import it into the FTD ...

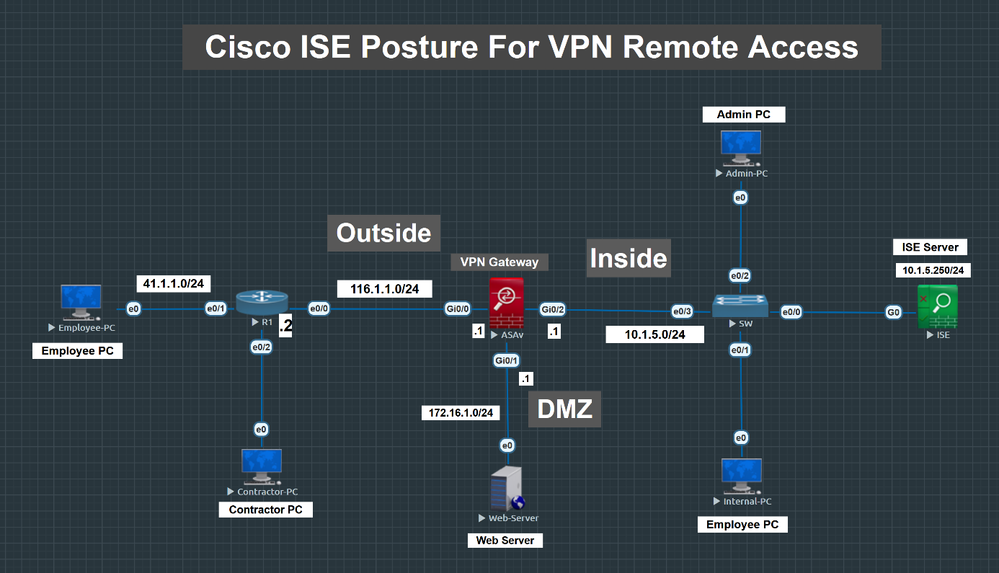
IntroductionIn this blog we will configure Remote Access VPN on cisco ASA with authentication using Certificate but Authorization using ISE via Active Directory.Video lab demo: https://youtu.be/UJWUk3...

Want to ensure business resiliency with a Threat-Informed Defense? On May 23rd, we are inviting a selected group of security customers in your region for a chance to learn and ask questions about T...

Welcome to our Pre-RSA LinkedIn live series, where we talk about what's 'Top of mind in SecOps'. Sign up for the first session of the series!

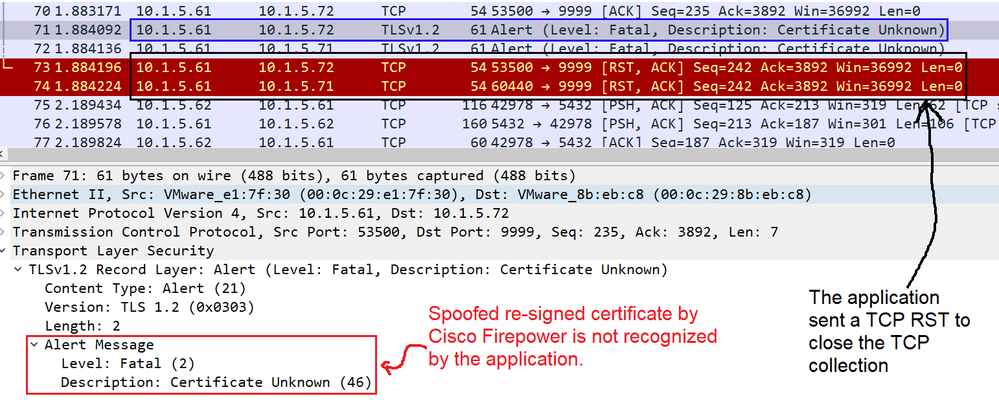
Some applications use a technique referred to as TLS/SSL pinning or certificate pinning, which embeds the fingerprint of the original server certificate in the application itself. As a result, if you ...
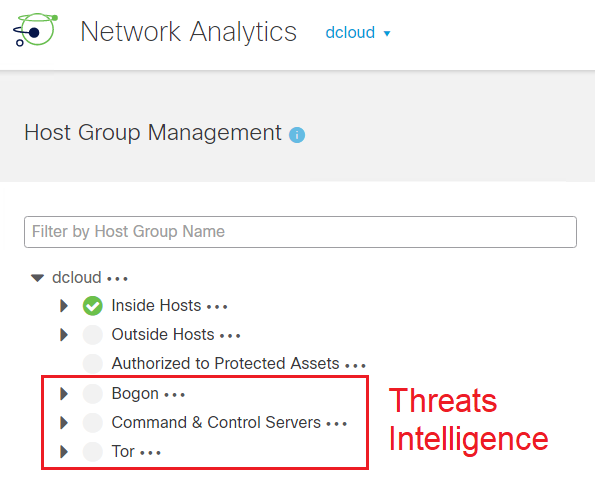
Threat Intelligence on Cisco Secure Network Analytics is similar to Security Intelligence on Cisco Firepower Threat Defense, while on FTD the informations of Malicious IPs URLs and DNS downloaded fro...
Policy Based Routing is the process of using a route map to specify an attribute other that the destination ip address like with the traditional routing protocol, then based on these attributes, you d...

From verified push – which protects organizations from MFA-focused phishing attacks – to Wi-Fi Fingerprint, and Remembered Devices, the performance enhancements with Enterprise Single Sign-on and Cisc...
